Ransomware of the sextortion type have adopted new tactics that helps to bypass various spam filters and security gateways. Sextortion ransomware now writes letters in foreign languages.
Recall that sextortion is a special type of online ransomware that has recently become widespread among cybercriminals.Attackers, as a rule, convince the victim that they have a video, which proves the fact and the process of visiting the pornographic sites. To prevent these media materials from getting anywhere, the user needs to pay ransomware of a certain amount“, – inform The Sun. reporters.
Sextortion has become so widespread that protective email gateways and spam filters have learned to quickly figure out and intercept such emails.
However, the new criminal tactics seem to solve this problem. For bypassing the above-mentioned filters, attackers send letters in foreign languages, and the addresses of wallets for transfer are divided into two parts.
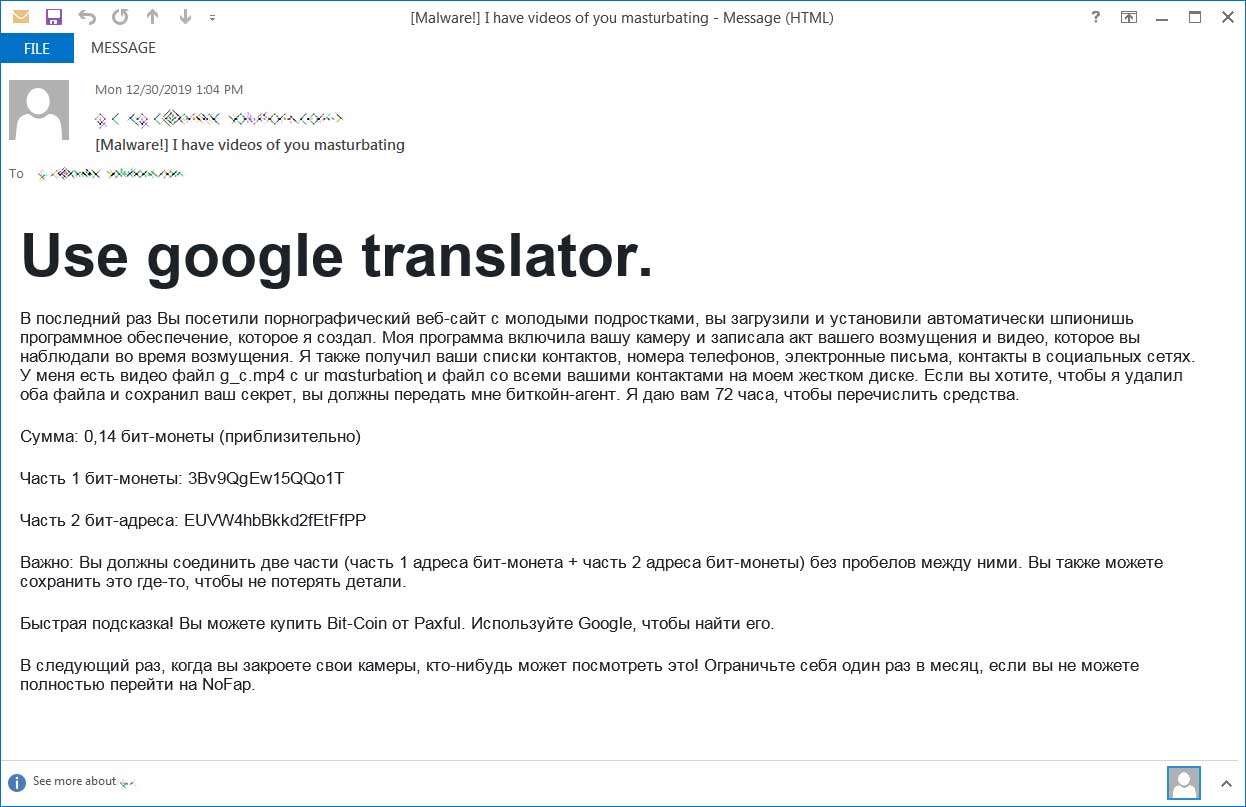
The following is an example of such a letter that was written in Russian, but intended for English-speaking users.
Text of the letter (at the top, the ransomware calls for using the Google Translator service):
“The last time you visited a pornographic website with young teens, you downloaded and installed automatically spy software that I created. My program turned on your camera and recorded the act of your indignation and the video that you observed during the indignation. ”
“I also received your contact lists, phone numbers, emails, contacts on social networks. I have a video file g_c.mp4 with ur mαsturbatioɳ and a file with all your contacts on my hard drive. If you want me to delete both files and keep your secret, you must pass me the bitcoin agent. I give you 72 hours to transfer funds. ”
“Amount: 0.14 bit-coin (approximately) Part 1 bit-coin: 3Bv9QgEw15QQo1T Part 2 bit-addresses: EUVW4hbBkkd2fEtFfPP
Important: You must connect the two parts (part 1 of the bit-coin address + part 2 of the address of the bit-coin) without spaces between them. You can also save this somewhere not to lose the details. Quick tip! You can buy Bit-Coin from Paxful. Use Google to find it. ”
“The next time you close your cameras, someone can watch this! Limit yourself once a month if you cannot fully switch to NoFap.”
In this way, the attackers create potential translation problems, counting on a guaranteed bypass of spam filters.
Gangs have been known to use “honey trap” actors to lure their victims in and record the images before threatening to share them with the victims’ friends and family unless they accede to their demands for payment
Most appear to single out victims based on their “ability to pay” and because “they have something to lose” and ransom demands range from a few hundred to a few thousand pounds.
Sextortion ransomware is based on the effect of surprise and criminals rarely publish naughty photography customers, but Maze ransomware operators recently published part of the stolen data from city of Pensacola in Florida to show that their intentions are serious.
Recommendations:
Anyone who receives this type of email is advised not to click on any links or open any attachments as this could load ransomware to the device.

hello!!
we already got infected from 2 weeks back and we can’t find a solution to decrypt these files .devil
if any possibility that will be a tool decrypt it soon?