A deeply troubling new extortion scam has emerged through spam emails, where scammers claim to be hackers with compromising footage of the recipient. The email threatens to leak videos and personal information publicly, unless a ransom payment is made in bitcoin. Known as the “I Am A Professional Hacker” email scam, this scheme spreads through mass spamming. This article will provide an in-depth analysis of how this scam works, how to spot extortion emails, and what actions to take to protect yourself.
Bitcoin Email Scam
How the Professional Hacker Email Scam Works
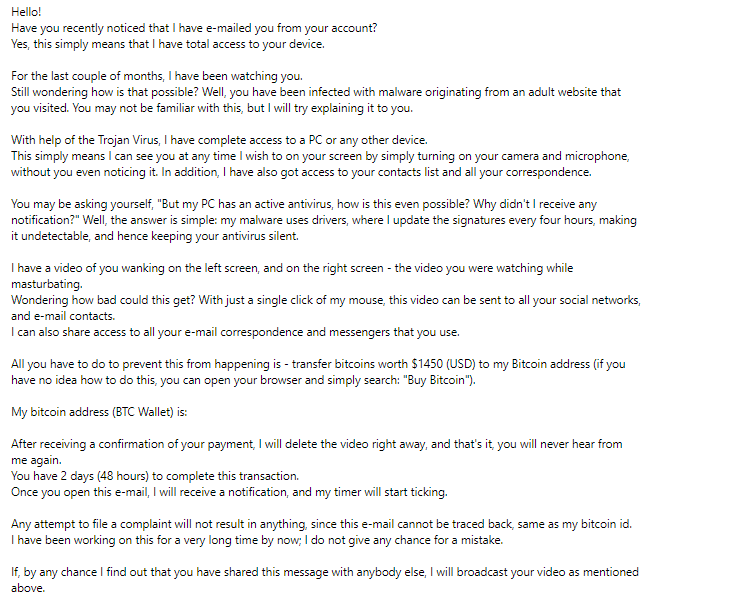
The “I Am A Professional Hacker” email scam is a form of extortion, in which scammers send out a mass of spam emails with the same message. The email falsely claims that the sender has compromising footage of the recipient and threatens to expose it publicly unless a ransom payment is made in Bitcoin.
Here is how a scam email looks:
Subject: Your personal data has leaked due to suspected harmful activities. Hi there! I am a professional hacker and have successfully managed to hack your operating system. Currently I have gained full access to your account. In addition, I was secretly monitoring all your activities and watching you for several months. The thing is your computer was infected with harmful spyware due to the fact that you had visited a website with porn content previously. Let me explain to you what that entails. Thanks to Trojan viruses, I can gain complete access to your computer or any other device that you own. It means that I can see absolutely everything in your screen and switch on the camera as well as microphone at any point of time without your permission. In addition, I can also access and see your confidential information as well as your emails and chat messages. You may be wondering why your antivirus cannot detect my malicious software. Let me break it down for you: I am using harmful software that is driver-based, which refreshes its signatures on 4-hourly basis, hence your antivirus is unable to detect it presence. I have made a video compilation, which shows on the left side the scenes of you happily masturbating, while on the right side it demonstrates the video you were watching at that moment… All I need is just to share this video to all email addresses and messenger contacts of people you are in communication with on your device or PC. Furthermore, I can also make public all your emails and chat history. I believe you would definitely want to avoid this from happening. Here is what you need to do – transfer the Bitcoin equivalent of 850 USD to my Bitcoin account (that is rather a simple process, which you can check out online in case if you don’t know how to do that). Below is my bitcoin account information (Bitcoin wallet): 12nEVuGNtRFMVjeVmLtD4nt2sHX68S47yH Once the required amount is transferred to my account, I will proceed with deleting all those videos and disappear from your life once and for all. Kindly ensure you complete the abovementioned transfer within 50 hours (2 days +). I will receive a notification right after you open this email, hence the countdown will start. Trust me, I am very careful, calculative and never make mistakes. If I discover that you shared this message with others, I will straight away proceed with making your private videos public. Good luck!
The Aim of the Scam
The message is designed to generate fear and panic, in order to extort the money from the recipient. By using the recipient’s email address, as well as other personal information, the scammer can make the message appear more convincing.
How the Scam Works
- The scammer sends out a mass of spam emails to potential victims.
- The email contains a message claiming that the sender has compromising footage or information about the recipient.
- The email then makes a threat to expose the compromising information unless a ransom payment is made in bitcoin.
- The scammer uses the recipient’s email address and other personal information to make the message appear more convincing.
- The recipient is then required to make a ransom payment in order to avoid having the compromising information released.
How to Protect Yourself
In order to protect yourself from this kind of scam, it is important to be aware of the tactics used by scammers and to take a few simple steps to protect your online presence. These steps include:
- Never provide personal information to anyone you don’t know or trust.
- Be suspicious of any email or message that claims to have compromising information about you.
- Do not click on links or open attachments in emails from unknown senders.
- Check the sender’s email address to make sure it is legitimate.
- Be wary of any requests for money or personal information.
- Install and regularly update anti-virus software on your computer.
- Never respond to emails or messages from scammers.
If you believe you have been the victim of this scam, you can report it to the Federal Trade Commission.
Spotting an Extortion Email
Extortion emails are a form of cyberattack that has become increasingly common in recent years. Fortunately, they are relatively easy to identify. By understanding the typical characteristics of extortion emails, you can be better prepared to protect yourself and your organization against this type of attack.
Common Characteristics of Extortion Emails
Extortion emails typically contain threatening language, such as “I am a professional hacker”, and demand payment in Bitcoin. They also often contain personal information, such as the recipient’s email address, as well as other details that suggest the sender has knowledge of the recipient’s activities. Additionally, they may contain spelling and grammar errors, which are a tell-tale sign of a scam email.
Additional Indicators of Extortion Emails
In addition to the characteristics listed above, extortion emails may contain the following indicators:
- Demands for payment in a short period of time
- Threats to release sensitive data
- Requests to contact the sender at an unusual email address
- Links to malicious websites or documents
What to Do if You Receive an Extortion Email
If you receive an extortion email, the first step is to resist the urge to panic. Instead, take a deep breath and assess the situation. Immediately notify your IT security team and keep a copy of the email for future reference. Your security team can help you determine if the email is legitimate and how to respond.
It is also important to take steps to ensure that your systems are secure. This includes regularly updating your software and using strong passwords for all accounts. Additionally, you should consider investing in two-factor authentication for additional security. By taking these steps, you can help protect yourself and your organization from potential extortion attacks.
Protecting Yourself from the Professional Hacker Email Scam
The “I Am A Professional Hacker” email scam is a serious threat to your cybersecurity. It is important to take steps to protect yourself against this type of attack. Here are some recommended methods to help keep you safe:
- Delete suspicious emails: The first and most important step is to delete any suspicious emails. Do not respond to the email or click any links, as this may put you at further risk.
- Keep security software up to date: It is important to ensure that your security software is up to date. This will help protect you from malicious attacks.
- Use strong passwords: Make sure that all of your accounts have strong passwords and two-factor authentication enabled. This will help to keep your accounts secure.
- Report extortion emails: If you do receive an extortion email, it is important to report it to the authorities. This will help to protect other people from the same scam.
By following these steps, you will be better protected against the ‘I Am A Professional Hacker’ email scam. If you have any further questions or concerns, please contact a cybersecurity specialist for more information.
Installing and Using Gridinsoft Anti-Malware
Gridinsoft Anti-Malware is a powerful security tool for scanning and protecting your computer from viruses and other malicious software. It is easy to install and use, offering a comprehensive range of features to keep your computer safe.
Step 1: Download Gridinsoft Anti-Malware
Visit the Gridinsoft Anti-Malware site to download the software. Follow the instructions on the site to install the software on your computer.
Step 2: Run a Scan
Once you have installed Gridinsoft Anti-Malware, you can run a scan to check for viruses and other malicious software. To do this, open the Gridinsoft Anti-Malware program and click the Scan button.
Step 3: Review Results
Once the scan is complete, you will be presented with a list of any threats detected. You can review the results to determine the severity of the threats. If any of the threats are deemed to be serious, you can take the necessary action to remove them.
Step 4: Clean and Protect
Once you have reviewed the results, you can use Gridinsoft Anti-Malware to clean and protect your computer. To do this, click the Clean and Protect button. This will remove any threats detected and also protect your computer from future threats.
Step 5: Update Database
Gridinsoft Anti-Malware updates its virus database regularly, so it is important to ensure that your database is up to date. To do this, click the Update Database button. This will ensure that Gridinsoft Anti-Malware is always up to date and is able to detect the latest threats.

