PhoenixMiner is a legit cryptocurrency miner, which is used by hundreds of users. In some cases, however, various viruses use its name to hide in your system. In this post, you will see the description of a phoenixminer.exe, and also the method to understand if that is a coin miner trojan.
About “PhoenixMiner.exe”
PhoenixMiner.exe is a process created by PhoenixMiner – legit cryptocurrency mining software
PhoenixMiner is a coin mining tool, which is officially developed and distributed by PhoenixMinerDevTeam. The latest actual version of this program is 5.5c, published 03/08/2021. It allows you to use your GPU computing power to perform a so-called cryptocurrency mining. Under that term people mean the operation of calculation of the transaction block hash. That calculation requires significant amounts of time and hardware capacity. People who are engaged in crypto mining use PhoenixMiner to control that process through the various settings. With that app, you can do certain adjustments to the hardware elements, used in mining, as well as can control the mining process efficiency and resource consumption. That program is definitely benevolent and legit, and you have nothing to worry about, especially if you installed it by yourself.
PhoenixMiner.exe Technical Summary.
| File Name | PhoenixMiner.exe |
| Type | Trojan Coin Miner |
| Detection Name | Trojan:Win32/CoinMiner |
| Distribution Method | Software bundling, Intrusive advertisement, redirects to shady sites etc. |
| Similar behavior | Hostdl, Nmon, Xme64 |
| Removal | Download and install GridinSoft Anti-Malware for automatic PhoenixMiner.exe removal. |
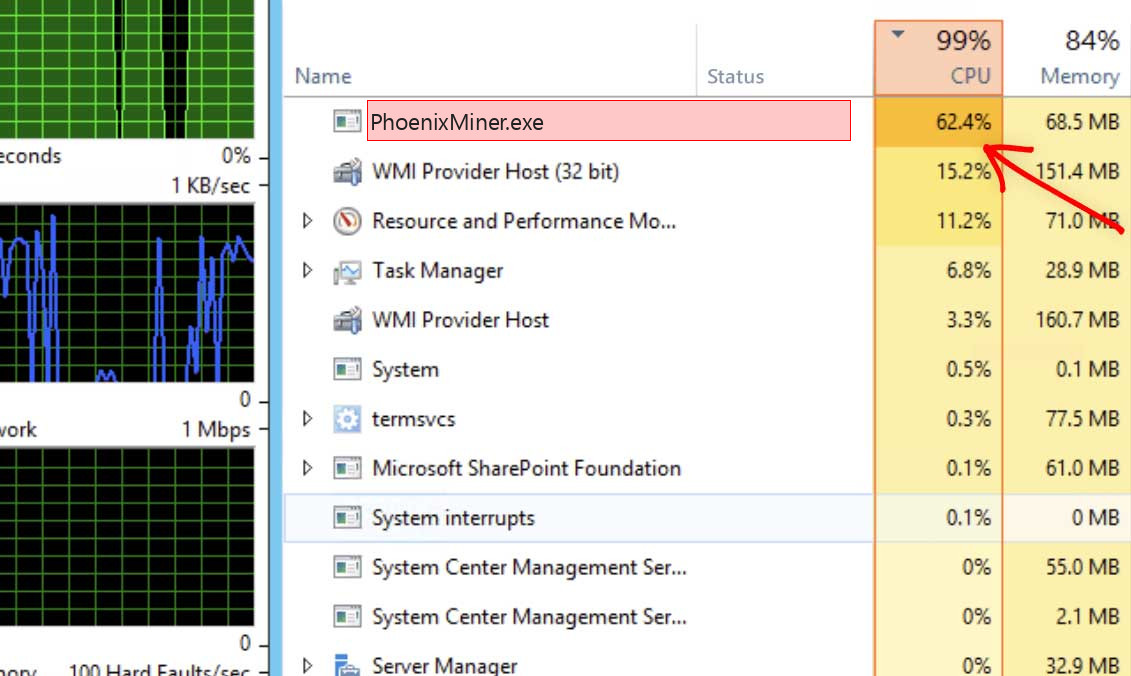
You can easily understand when the phoenixminer.exe process is a virus. GridinSoft Anti-Malware users can launch a full scan, and the security tool will give you the answer in less than 15 minutes. Another way requires you to remember the past several days. If you spectate that process in Task Manager, and sure you were not installing PhoenixMiner – it is a strong reason to scan your computer. Unlike the original coin mining tool, malicious counterfeit will also consume your CPU power. Processor utilization usually means that your PC is infected with a coin mining trojan. Viruses like spyware or stealers, that are used to steal your sensitive data and even important files from your computer, can also be a reason for the significant disk capacity consumption, and can use the phoenixminer.exe name, too. All of these cases are not pleasant. It is recommended to scan your computer as soon as possible.
How to detect PhoenixMiner.exe Coin Miner Trojan?
Unlike ransomware, coin miner trojans do not say openly about their presence.
Discovering PhoenixMiner.exe threat is quite easy. If the victim uses a GridinSoft Anti-Malware it is virtually particular to discover any kind of mining malware. Also without a protection service, the victim is most likely to presume there is something wrong due to the fact that mining bitcoin or various other cryptocurrencies is a very source extensive procedure. One of the most typical symptom is an obvious and also commonly constant decrease in performance.
This symptom alone does not tell the target what the specific trouble is. The user can experience comparable problems for a selection of factors. Still, malicious lolminer.exe malware can be extremely disruptive since it will use all available computing power. Even if you have a high-end PC, virus will squeeze all possible resources from your machine. You will struggle even to open the browser, but the crooks who distribute that virus have all your computing power. The increased electricity bills which you will receive after the virus activity must be paid, too.
How to Remove PhoenixMiner.exe Malware?
Once the sufferer has determined that their trouble is PhoenixMiner.exe risk, for the usual user there are a couple of services.
Primarily usage GridinSoft Anti-Malware would be the most effective option. There is no scarcity of available cybersecurity software program that will detect and also eliminate mining malware.
Conversely, if the infected device doesn’t have crucial information or the target has supported such information in a clean area, and also the individual has some experience, formatting the hard drives could work. This option may not suffice if the infection has infiltrated one or more networks the machine belongs of.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for PhoenixMiner.exe file and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
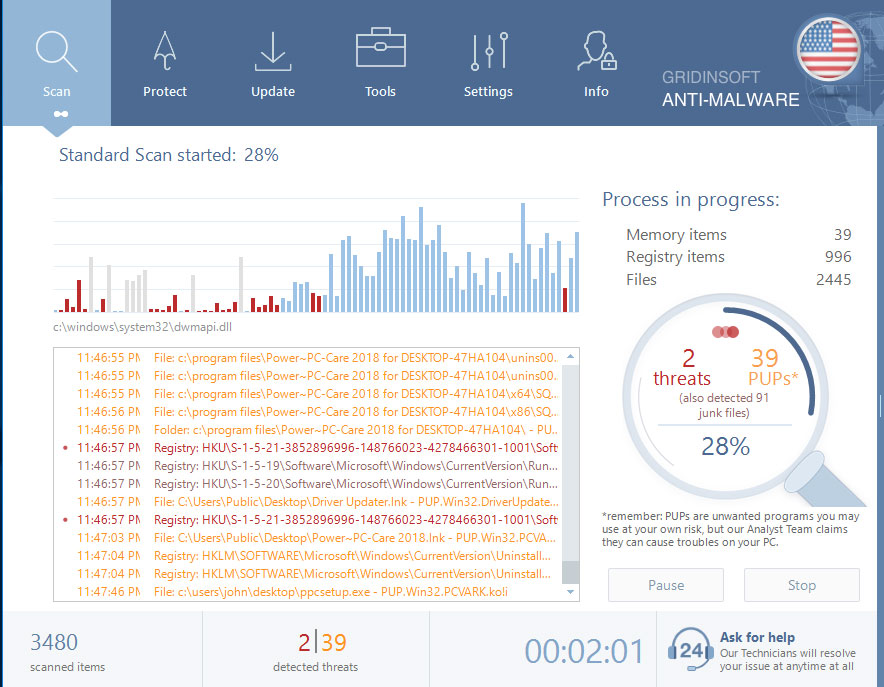
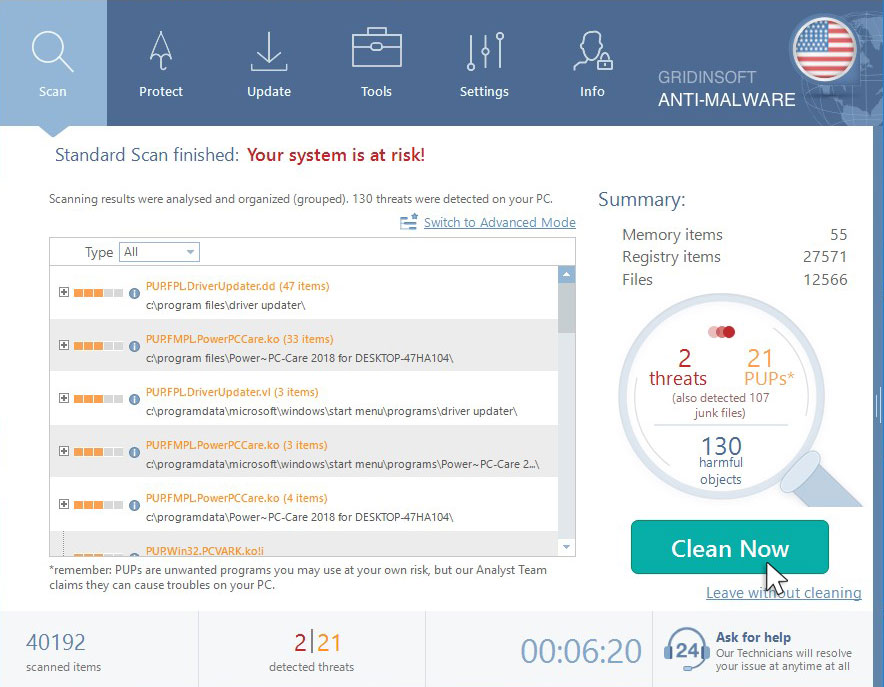
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
If the guide doesn’t help you to remove PhoenixMiner.exe infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help. Good luck!
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison


Hello, I ‘ve read your article with great interest but it does not address the question for users who are “Actually” using their PC for mining Etherium or other . Is this still a virus if they willfully installed the program on their PC. I find you answer only te question of “involuntary” installation. That may not always be the case.