While the whole world was summarizing the past year in the state of the pandemic, the cybersecurity world showed an unusual calmness. After the roaring 2020, which was a real trial for the security tools developers, January looked like a normal continuation. But in February a lot of things changed: several big groups of malware distributors were busted, so ransomware distribution became very slack. These events put a lot of influence on the further spreading of all malware. So, it is nothing extraordinary that there were only 3 things from cybersecurity world in March I want to tell you about.
Twitter bitcoin scammer got jailed for 3 years. Fair punishment for a young fraudster?
Almost a year ago, in June 2020, we could speculate a large speculation around Twitter accounts of Bill Gates, Elon Musk, Joseph Biden, Apple, and many others. In one day, all three accounts began posting the following messages:
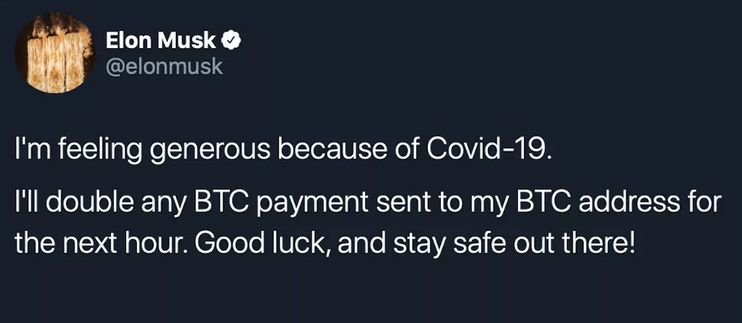
The bitcoin wallet was specified in a separate tweet. People couldn’t believe that the original accounts of these persons were hacked, so a lot of users trusted those messages and sent their bitcoins. In fact, all those posts were published by a 17-y.o. Graham Ivan Clark and two others. He got access to the account of Twitter employees through the phishing, and then posted the fraudulent messages using the Internal Twitter tools.
Graham Ivan Clark, Mason Sheppard and Nima Fazeli were captured soon after the short investigation. Before the fraudsters were uncovered, all Internal Twitter tools functions for posting as a verified account were disabled. Clark reportedly acted as a “chief” for this scheme, commanding the Sheppard and Fazeli. The total money stolen through this scheme is about $117,000 (in BTC equivalent).
Young fraudster was imprisoned at the moment of fraud uncovering, so he had already spent almost 8 months before getting a final sentence – 3 years in prison. Same terms were sentenced for his accomplices, however, they were house arrested for the whole term of investigation instead of being imprisoned.
New data collecting scandal with Google
Google was been blamed in stealing the users’ data, again. Now, the lawsuit is filed for data collecting in Chrome Incognito mode. The co states that only ISP is able to track the information you browse while being in Incognito mode. However, as the investigation showed, the tech giant was still able to get the details about your searches and opened pages.
“We strongly dispute these claims and we will defend ourselves vigorously against them. Incognito mode in Chrome gives you the choice to browse the internet without your activity being saved to your browser or device. As we clearly state each time you open a new incognito tab, websites might be able to collect information about your browsing activity during your session.”
—Google spokesperson Jose Castaneda in his interview to Bloomberg.
Google tried to throw out the case, appealing to the note displayed every time you open the Incognito tab in Chrome ( “…activity might still be visible to: websites you visit, your employer or school, your internet search provider”). Nonetheless, such a claim was not enough for the US District Judge to explain why the information is collected by Google, not only by the list of mentioned instances. The total amount of money the lawsuit seeks is about $5 billion.
FBI names the amount of money lost because of cybercrimes in 2020
2020 was a year of records and innovations. In cybersecurity, that year is remembered for a record malware activity. As the Federal Bureau of Investigations state, in 2020 cybercrime-related losses reached $4.2 billion. That sum is 700 millions bigger than in 2019, when the cybercrimes took $3.5 bln. The number of compliances for cybercrimes has also increased sharply: almost 800,000 fillings in 2020, which is 70% more than in 2019.
Will 2021 show us another malware wave? Barely. It already lags, since the malware distribution was struggling in February and March. Of course, crooks discovered other malware spreading methods, so the hazard is still there, it just changed the disguise. But the significant activity lag is already a sign that malware creators are less active than one year ago. At least, cybersecurity experts hope that 2021 will not be as crazy as 2020 was.
Why was malware so active in 2020? Pandemy forced a lot of people to work from home, and it is impossible to imagine the work from home without the use of a PC. More PC users – more infection cases, even if malware distributors do not make any additional movements. But they did, so we may have seen an exponential curve of malware cases all over the world. Adware, ransomware, coin miners, spyware, banking trojans – these malware types were pumping through 2020. And all of them except ransomware are still pumping, but with a less scale. Nowadays, impudent tricks that manipulate the pandemic theme do not work. People learned how to distinguish this scam, and it became harder to find a user who does not hear about ransomware. The total level of cybersecurity knowledge rises, but it is a Pyrrhic victory.
Checking the virus types and tricks; numbers from cybersecurity agency
The decision to disguise into government agencies was a very wise choice. Since a lot of people are in a blind trust to the governmental names, it is very easy to fool them. The fooling can lead to credentials loss, malware installation, or even money extortion. However, it is still not as dangerous as bank account hijacking. Fraudsters began hiding under the names of Citibank, Morgan Stanley and Bank of America to get the login and password from your bank account. Then, they just transfer all money you have on your account to their cryptocurrency wallet, transforming it into Bitcoin or altcoins.
Not only bank accounts were a point of increased interest. Successful hacking and infecting of the corporate network require an internal breach. And the stolen email of the company’s employee is a perfect key for malware injection. According to the IC3 report, 19369 email accounts were hijacked, both used in business and for users’ personal mailing. Total damage done with these actions reached $1.8 bln. The ways of email account hijacking are different: spyware activity is the most obvious way, but a lot of crooks use less rude methods. The perfect example of such a method is a Kaspersky email spam, which takes place right now.
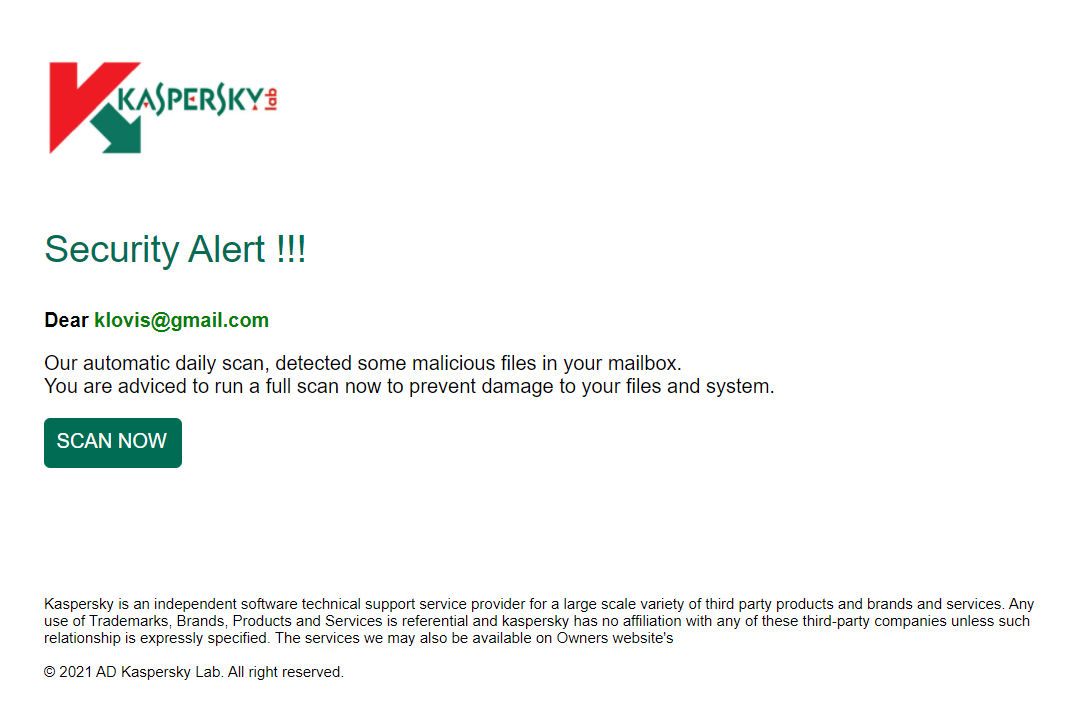
A lot of things which were seen in 2020 are still in use. The Microsoft Pornographic virus alert is a perfect example of this scam. Adware shows you the scary banner that offers to call the support. On the phone you are said to give remote access to your PC for the “support managers”. After getting control, they just block the Defender and install a malware which extorts the money and shows more and more disruptive ads. As a variant, they can offer you to install so-called scareware. That is a pseudo-antivirus, that shows you the fake detects and blocks the elements of programs you use. To make the programs back usable, you need to purchase a full version of this “antivirus”. In total, 15,421 cases of tech support scam was reported, with a total loss of $146 million.
User Review
( votes)


