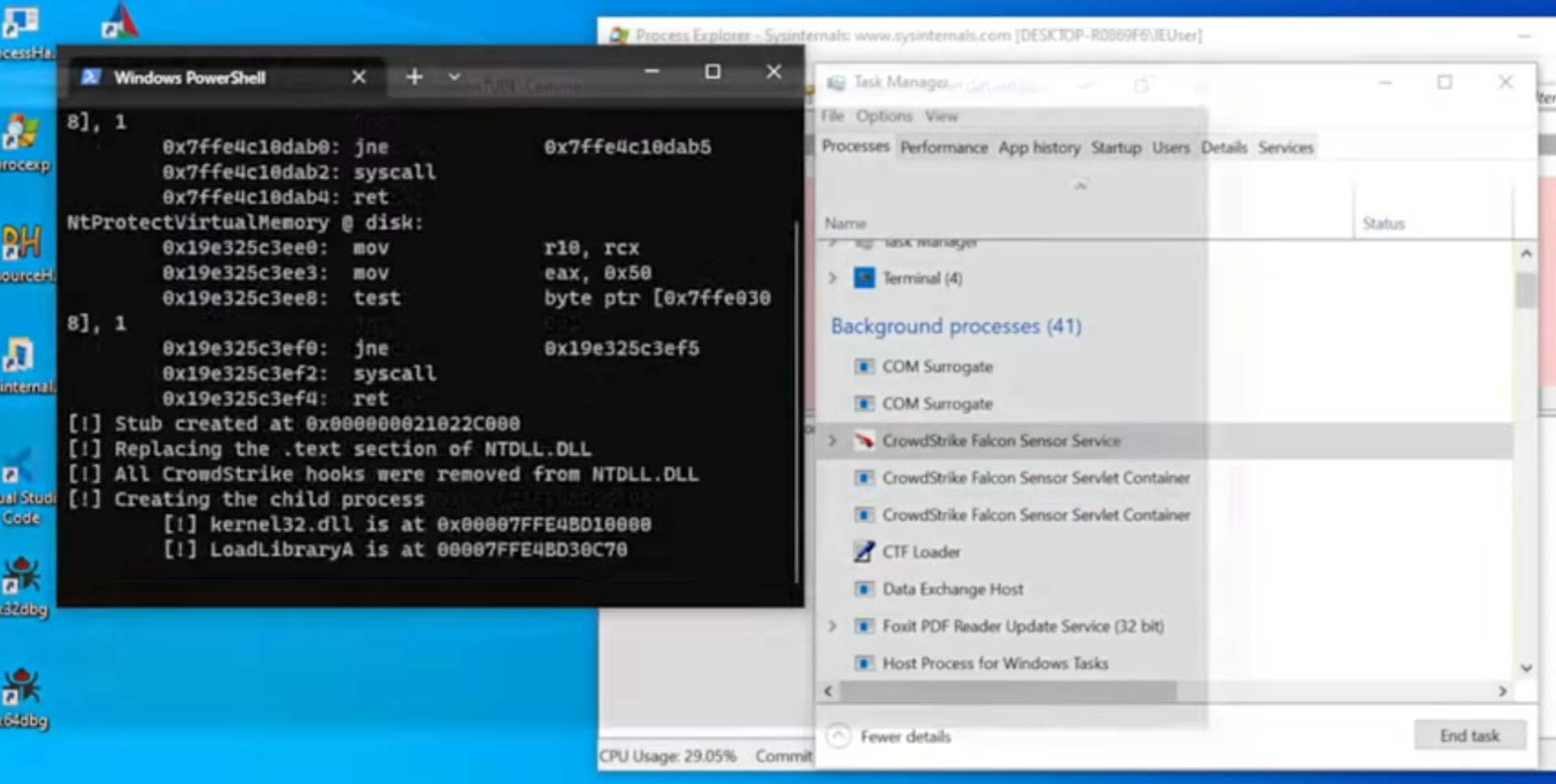
A groundbreaking process injection technique called Mockingjay has emerged, enabling threat actors to evade detection by security solutions and execute malicious code on compromised systems actively.
Security Joes researchers Thiago Peixoto, Felipe Duarte, and Ido Naor shared in a report that Mockingjay accomplishes injection without the need for space allocation, permission settings, or thread initiation. Instead, it relies on a vulnerable DLL and code replication to the appropriate section.
Notable process injection techniques include dynamic link library (DLL) injection, portable executable injection, thread execution hijacking, process hollowing, and process doppelganging, among others.
It is important to note that each of these methods requires a combination of specific system calls and Windows APIs. These requirements enable defenders to develop effective detection and mitigation procedures.
New Mockingjay Process Injection Technique
What sets Mockingjay apart is its ability to subvert these security layers by eliminating the need to execute memory block protected with Read-Write-Execute (RWX) permissions.
For this purpose, the technique utilizes msys-2.0.dll, which offers an ample 16 KB of available RWX space. This DLL serves as an ideal candidate for loading malicious code and evading detection. However, it’s worth mentioning that other susceptible DLLs with similar characteristics may also exist.
The Israeli company behind Mockingjay explored two different methods, namely self-injection and remote process injection, to achieve code injection while enhancing attack efficiency and evading detection.
In the self-injection approach, a custom application directly loads the vulnerable DLL into its address space and subsequently executes the desired code using the RWX section. On the other hand, remote process injection involves leveraging the RWX section in the vulnerable DLL to inject code into a remote process, such as ssh.exe.
These findings arrive shortly after cybersecurity firm SpecterOps unveiled a new method that exploits ClickOnce, a legitimate Visual Studio deployment technology. This technique enables adversaries to achieve arbitrary code execution and gain initial access.
User Review
( votes)

