The Internet is swarming with tamperers, fraudulent schemes, and malicious computer programs. Antivirus software developers do enormous work to keep track of all existent harmful pieces of code1. Security specialists around the world look to find and eliminate system vulnerabilities that hackers might exploit. Nevertheless, the efforts of engineers are not enough to maintain network security. Workgroup administrators, as well as rankers, are also responsible for the informational safety of their enterprise. It doesn’t matter how good the defenders and firewalls are when users keep them switched off. From this article, you will learn some crucial points of making workgroups closest to virus-proof.
Use antivirus software
First of all, you need a system-based antivirus program. You’ve most certainly heard the names of these AVs: Microsoft Defender, McAfee Total Protection, Kaspersky Anti-Virus, ESET NOD32, and others. Upon installation, these programs incorporate themselves within the operating system and provide broad-based protection of your PC. You have to choose the antivirus wisely because you can have only one installed. Different antiviruses conflict with each other, as they are supposed to occupy a special place designed for them in operating systems. Although AVs bring about a solid basis for the antimalware defense of your network, they are not sufficient for a workgroup.
Don’t forget about Antimalware software!
The definition of malware is broader than that of a virus. The latter refers to a relatively old type of harmful software with some particular attributes, while malware is any malicious program to be found today. Although most modern antivirus programs feature antimalware scanning, you have to be aware that all such programs have different bases of known malware. The “bits of knowledge” of various scanners only partly match 2.
Therefore, it is advisable to use a “big” system antivirus and conduct regular drive scans with one or more antimalware utilities. GridinSoft Anti-Malware, for example, is one of the best programs to be used alongside an antivirus system defense.
Update everything timely!
Keep all your updatable software updated. This rule is more crucial than it might seem. Updates often patch up holes in the code, dealing with vulnerabilities of the software you use. It is essential for operating systems and, needless to say, for antivirus programs too.
System back-ups and passwords
Take the trouble to schedule backing-up of your files and the state of your operating system. You will never regret the organizational efforts of this sort. If anything happens, you’ll be able to return to the last viable configuration. It is better to have more than one configuration to restore at the disposal.
Set operating systems and all communication applications of the network to require users to change their passwords regularly. Strong passwords essentially strengthen network security. Do not just suggest workers think of new passwords from time to time – this won’t work. Human beings can be lazy and forgetful. Make password change your operating system’s scheduled task.
Don’t neglect firewalls
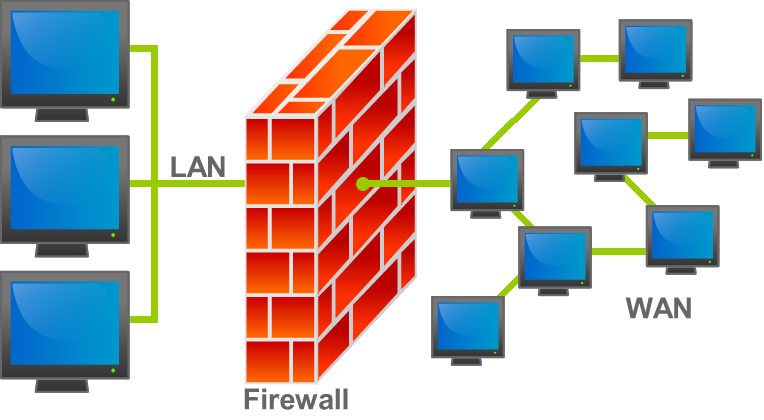
Schematic of how a firewall works. It separates a local area network (LAN) from the wide area network (WAN). Image via Wikipedia
A firewall is a software filter that separates a network it protects from the untrusted environment. It can be fencing a single machine or a network of computers. A firewall controls the incoming and outgoing traffic using the previously defined rules. Users often tend to consider firewalls redundant, or people sometimes switch them off temporarily to access some sites they trust but later forget to reactivate them. That might lead to irrecoverable damage to the network.
READ ALSO: 0x80070643 – an update error in Windows 10. Five ways to fix.
Benefits of segmented networks
Dividing your network into segments is probably the least convenient thing to do, but if malware starts spreading within your network, it pays well. Harmful programs travel from one machine to another, and it takes time. Having crucial data separated by severely set firewalls or even physically separated from the rest of the network can win just enough time to detect and eliminate the threat. How To Fix Guide has previously covered a story about a Chilean bank that was literally saved from total collapse after a ransomware attack thanks to the segmented network.
Hard Network Security
Remember that orchestrated hackers’ attacks usually exploit real-world incaution of the targeted network users. Unshuttered windows are a chance of someone’s hands getting filmed while they type their passwords. Neglected employee hard ID system allows some guy who just “got the wrong door” to insert a flashcard with self-deploying malware into one of the computers. And so forth! Also, don’t forget to keep your servers protected from any possible damage, regardless of menace from malefactors.
Awareness (conclusion)

Endpoints are the weakest links of any network. Stay vigilant!
We are segueing now to the general awareness of the reality of threats impending over businesses in the modern world. Hardly can this be overestimated. There are two components of this:
- Business owners’ part is to implement all the safety measures in compliance with the network security plan. That plan must exist in the first place. Executives must clearly and straightforwardly get the message to their subordinates: “The threat is real. Stay vigilant. Security procedures are not for nothing”. Have a network security plan. Implement a culture of digital security in the company.
- The employees’ part is to realize that digital security works just the same way health guard does. Device authentication should not irritate them, just like washing hands upon coming home doesn’t. The usage of the Internet and e-mails, following any links, etc., should be a matter of caution.
Endpoints are the weakest links of any network. Hackers often use human engineering to get what they want, but the vigilance of the team members can prevent them from succeeding.
Remember, if counter-virus measures work well – they always seem excessive. If you somehow fail to prevent infection – no action feels sufficient.
User Review
( votes)References
- How To Fix Guide website houses a vast, diversified, and constantly updated catalog of known malicious programs.
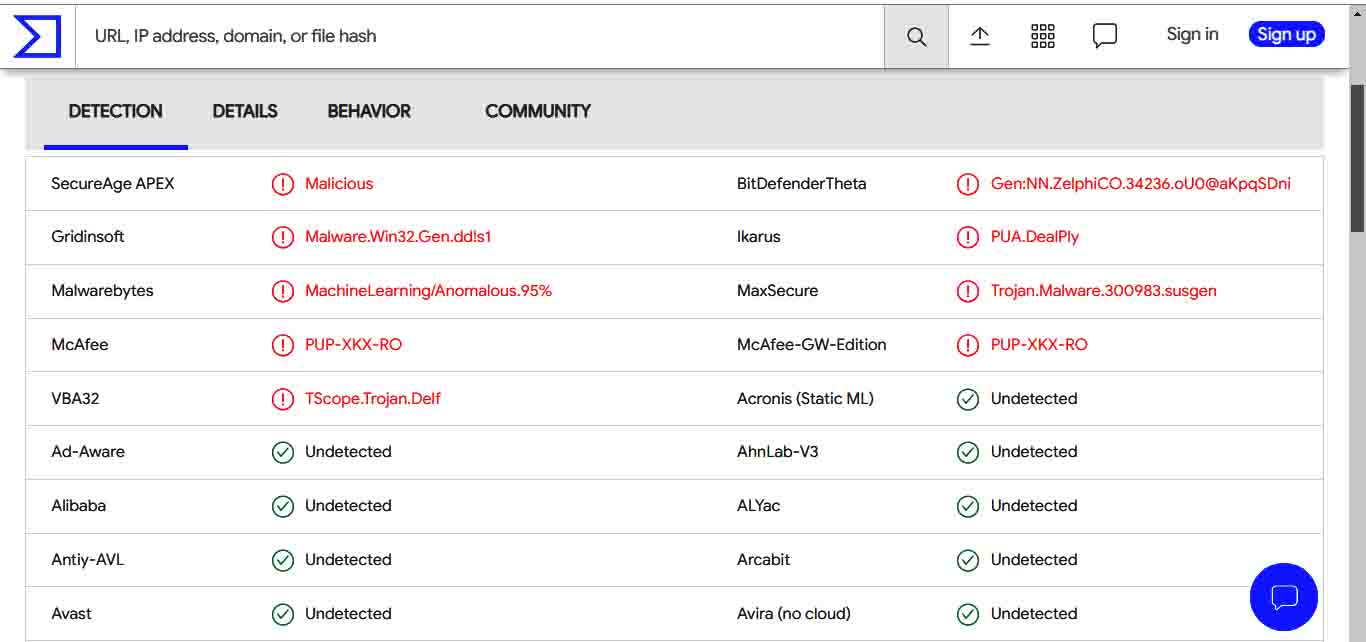
- Virus-checking sites like VirusTotal often show how various security vendors recognize threats differently. AVs’ quality does not directly determine that difference.