Microsoft warned admins today to immediately patch a high severity Exchange Server vulnerability that may allow authenticated attackers to execute code remotely on vulnerable servers.
The vulnerability (CVE-2021-42321) affects all supported versions of Exchange Server (2013 SP1 and later) and all supported platforms (physical, virtual, and cloud-based Exchange servers, e.g. Office 365) according to the advisory issued by the Microsoft Malware Protection Center.
The Microsoft Security Response Center published information on the vulnerability last week and recommends administrators patch and reboot affected servers.
The vulnerability can be exploited by attackers who have an active presence on the system where the Exchange server is running.
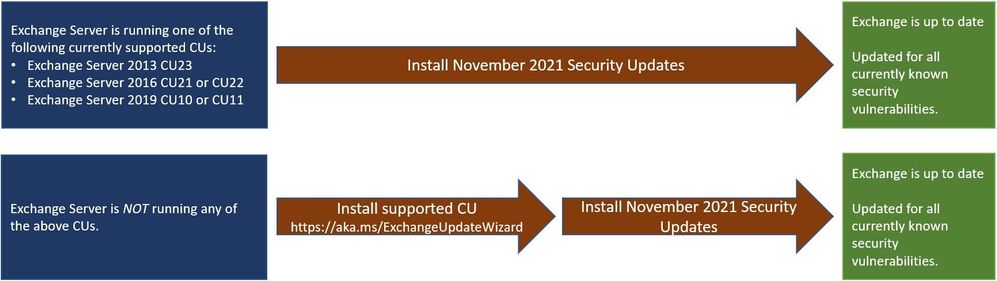
Exchange Server update paths (Microsoft)
The vulnerabilities can be exploited through insecure Exchange ActiveSync or ActiveSync Services.
Microsoft told The Register that the vulnerability is a four-stage attack vector where an attacker uses a malicious attachment in an email message to take control of a server running Exchange Server.
The attacker also has to be logged in with elevated privileges on the server, such as using admin rights, to perform the attack.
The security advisory contains a proof-of-concept exploit that can be executed by a Microsoft customer with a low-security posture. It can be accessed on GitHub here.
Fortunately for most Exchange customers, there are other measures that can be taken to mitigate the risk.
The first one is to ensure that Exchange ActiveSync and ActiveSync Services are disabled or switched off in Exchange server settings.
Second, customers should use a proper Exchange client to manage email messages. Other solutions are available in the marketplace like Thunderbird or Outlook Mobile.
Microsoft advises that clients that don’t meet its minimum requirements, such as no Exchange ActiveSync or ActiveSync Services or Exchange ActiveSync Manager, should not be installed in the first place.
Office 365 admins should also check and update all Exchange servers in the Office 365 Admin Center.
If you want to check and see if any of your Exchange servers were hit by CVE-2021-42321 exploitation attempts, you have to run the following PowerShell query on each Exchange server to check for specific events in the Event Log:
Get-EventLog -LogName Application -Source "MSExchange Common" -EntryType Error | Where-Object { $_.Message -like "*BinaryFormatter.Deserialize*" } Let me remind you that I also talked about the fact that New vulnerabilities in Microsoft Exchange have already affected tens of thousands of organizations.