If you ask yourself whether uTorrent is safe, you will have to specify what you mean. The point is that UTorrent is neither safe nor harmful by itself. It is just a peer-to-peer application to download information. To download files via a BitTorrent client, you must have a file with *.torrent extension, which contains information about the item you want to download or share.
Although trackers execute downloading in a specific way (bit by bit from equal sharers throughout the network), they are not much different from browsers by their inherent hazardousness. The question is: what are you downloading. Many antivirus programs, Microsoft Defender, for instance, consider uTorrent a potentially unwanted application. How To Fix Guide has even scrutinized the situation when an antivirus regularly reports on uTorrent as a security threat. However, the truth doesn’t change. Any malicious program that can intrude into your computer via BitTorrent tracker does not originate from the tracker itself.
In this article, you will find information on possible threats and sticking points. There are also hints here on how to use your BitTorrent clients as safe as possible.
Legality
Let’s make it clear: uTorrent, just like any other BitTorrent tracker, is legal. It’s nothing else but a client program for a BitTorrent file sharing and communication protocol. We are not delving deep into legal questions here, the purpose of the article being your information security. However, there is still something that you should know: the ISPs (Internet service providers) might be too overprotective about their clients using the BitTorrent trackers. That is due to some reputation of the protocol in question. People often use it to spread unlicensed materials indeed.
Virus Threats
You surely don’t want to end up with a virus on your machine. And yet malware can get into usual computers via BitTorrent clients like uTorrent, for instance. We have previously published the news about a torrent-spread malware aimed at Chinese and South Korean users.
What might seem an accident to you could be a well-planned operation. Hackers gladly use torrent files to infect network peers with one of the most wicked types of malware – ransomware. There is a decent informative article on How To Fix Guide about ransomware, which you can attend later. Shortly speaking, such programs allow criminals to encrypt the data on your hard drive and then racketeer you for ransom. In a better case, you will get the password to decipher your data back after you pay. So the profit for the plotters is evident.
You may ask, how do the malefactors find people who are likely to pay? Of course, it is a bit of a hit or miss, but social engineering is always a part of hackers’ work. They either know that their exact target is going to look for something particular on torrents in the first place, or they know what kind of people search for certain sorts of files.
Measure 1: Controlled Folder Access
In Microsoft Windows 101 and 11 There is a Controlled Folder Access feature. It can block the folders you choose from unauthorized access. It is a good defense from ransomware, but it might be inconvenient since CFA might block some good programs’ access to the protected folders. You can switch it on when you download and keep it on for some time after that until you make sure you haven’t caught anything malicious. There is more useful information on CFA on Microsoft website.
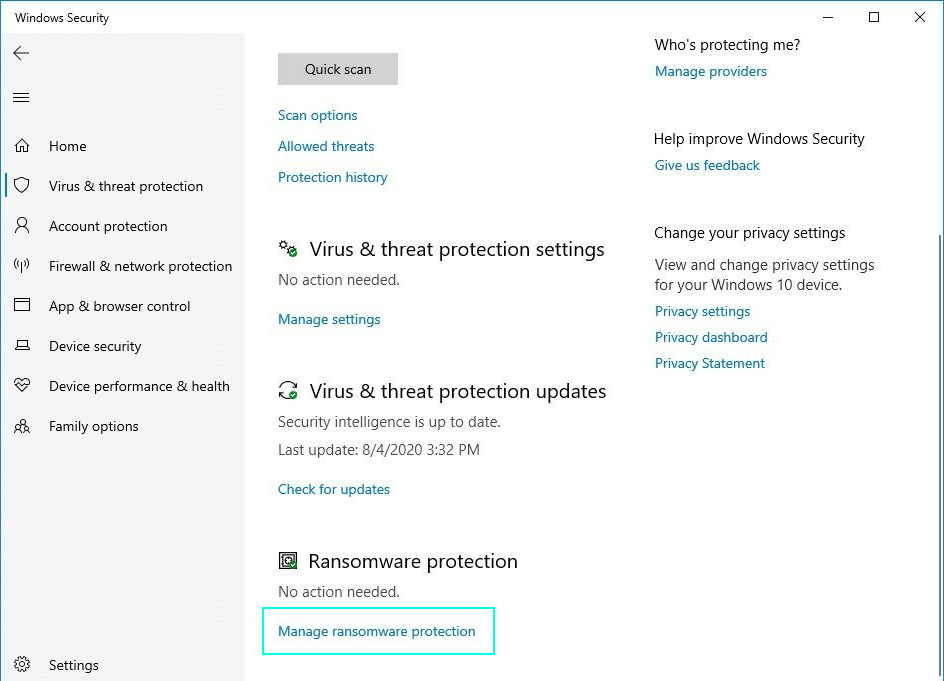
To switch the CFA on (in Windows 10 or 11) use the search bar and look for Virus & Threat Protections Settings. Open the found item and press a blue text line Manage Ransomware Protection in the lower part of the window, in the Ransomware Protection section.
In the Ransomware Protection window that will open, make sure the switch in the Controlled Folder Access is in “On” position. Under the switch you will see three main options of the feature: Block History, Protected Folders, and Allow an App Through Controlled Folder Access. With the help of these three, you can easily define which folders you want to be protected and which programs are allowed to access the protected data. Block history will show which programs have already attempted to access the protected folders.
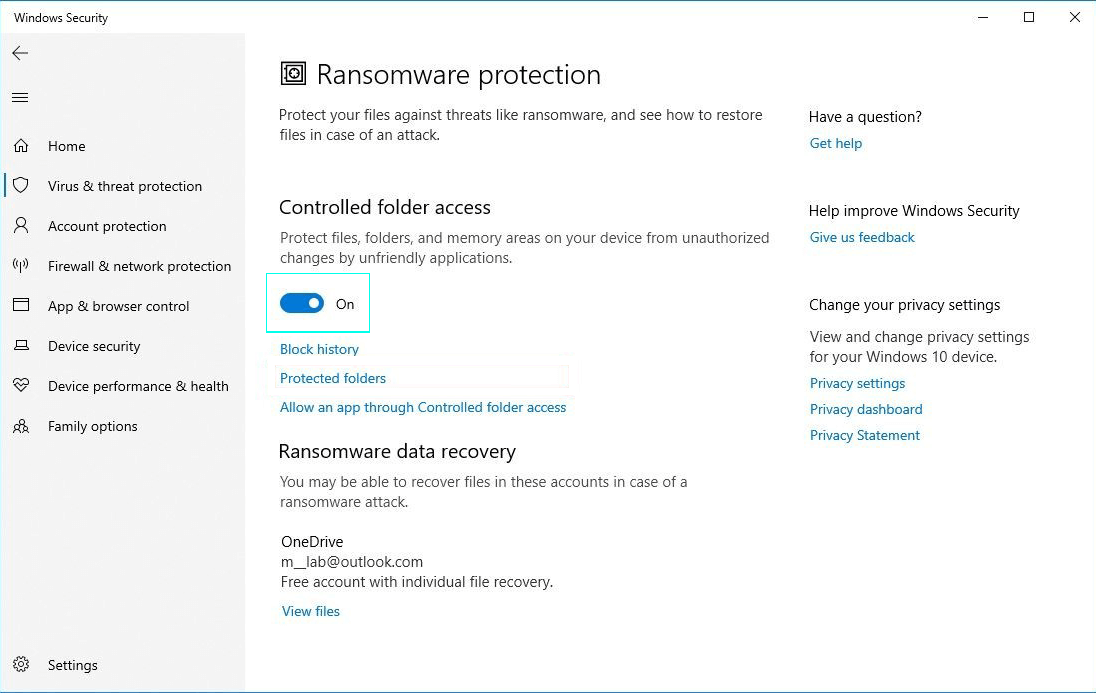
In the Ransomware Protection window that will open, make sure the switch in the Controlled Folder Access is in “On” position. Under the switch you will see three main options of the feature: Block History, Protected Folders, and Allow an App Through Controlled Folder Access.
Measure 2: Antivirus software
There are many ways of protecting your computer that is not antiviruses as such. We will get to them in the next section. However, it is crucial to have a good antivirus program. Although ransomware can be auto-deploying so that its victim has no time to do anything about it, there are still many extortion viruses that need you to download and subsequently open them.
That’s where the antivirus software comes in: it detects and deletes malicious programs from your computer and blocks (or at least gives you a warning) suspicious downloads. It is reasonable to combine your background antivirus program, for example, Windows Defender, and an auxiliary antimalware utility, like GridinSoft Anti-Malware. The point is that various antimalware products have different virus card files, and they might treat the same object differently.
What depends on you
The following safety measures might be as crucial as having antimalware software.
- Make a research on Internet resources where torrent files are shared. Find trustworthy ones. You can attend forums like Reddit to delve deeper into this. But it is crucial to do it before you start torrenting.
- Have your Controlled Folder Access on.
- Have the most critical data backed up and stored somewhere safe. It can be cloud storage or an external drive.
- Don’t neglect the firewall of your antivirus software. It might slow down the BitTorrent downloading, but it can prevent criminals from accessing your data if they have managed to inject a malicious file into your system.
READ ALSO: About Windows 11. What’s new in this operating system?
User Review
( votes)References
- How To Fix Guide features big information section dedicated to useful Windows 10 features and security novelties. Consider browsing it to keep your system fully protected.