ZDNet reporters discovered that hackers are attacking the Lenovo NAS after during investigation of users’ complaints, appearing on the BitcoinAbuse website. This site reports bitcoin addresses that use ransomwares, scammers and all kinds of cybercriminals.
As it turned out, about a month ago, the Cl0ud SecuritY group began to hack into old LenovoEMC network drives (formerly Iomega). Attackers erase all files from them and leave a ransom note, demanding from 200 to 275 US dollars.Hackers didn’t rely on a complex exploit, targeted devices that were already wide open on the internet, and didn’t bother encrypting the data”, — Victor Gevers, a security researcher with the GDI Foundation, told ZDNet.
Let me remind you that Lenovo stopped working on the LenovoEMC and Iomega NAS lines in 2018, and most of the network drives in these series are no longer supported and are outdated.
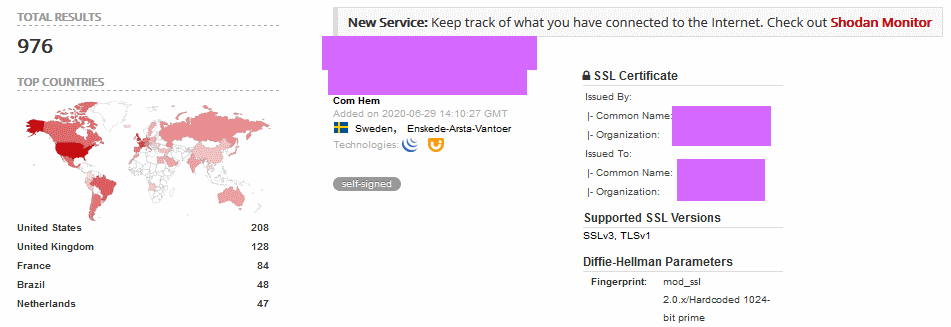
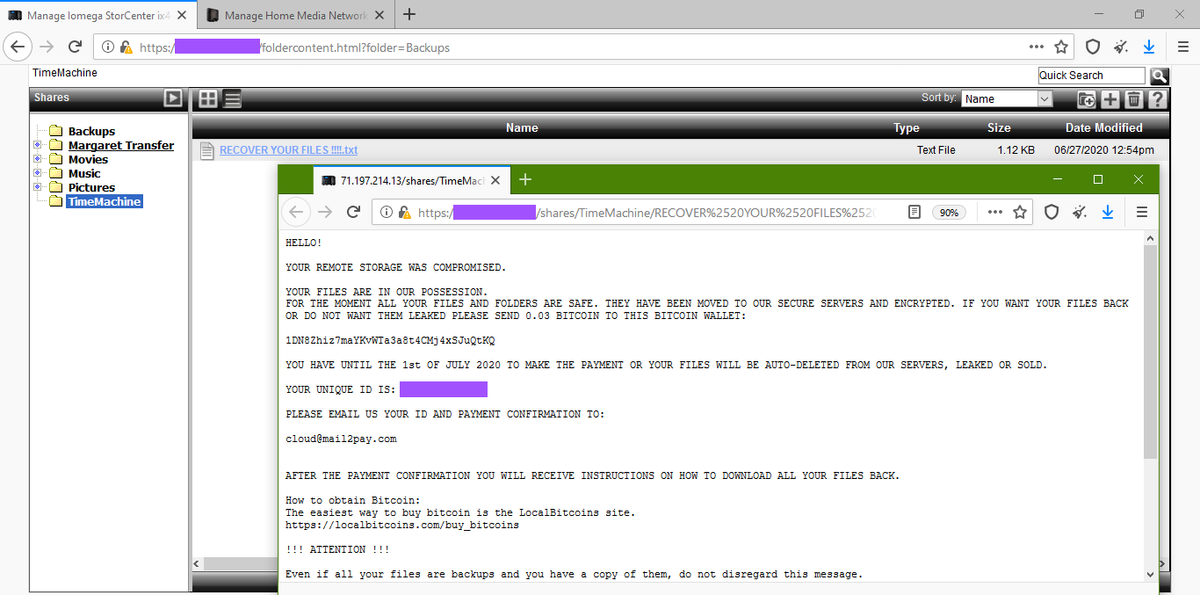
Apparently, the attacks are aimed only at unprotected LenovoEMC devices that are accessible via the Internet without passwords. Journalists were able to detect about 1000 of these devices using the Shodan IoT search engine. Moreover, many of these NASs have already been attacked and contain a ransom note – the RECOVER YOUR FILES !!!!.txt file.
All extortion messages are signed by Cl0ud SecuritY and also contain the email address [email protected].
Cl0ud SecuritY claims that before the deletion they copied the victim’s files to their servers and threaten to publish them in the public domain if the ransom is not paid within five days.
However, there is no evidence that cybercriminals store victims’ data, and the specialists are not aware about precedents of publishing such information in the public domain.
Based on current evidence, the ransom notes carry only empty threats, and their role seems to be to scare victims, forcing them to pay a ransom demand for data hackers have already wiped”, – write ZDNet reporters.
It seems that the attackers are simply trying to intimidate their victims, while user information has already been completely and irreversibly destroyed.
This malware campaign seems to be a continuation of last year’s series of attacks on Iomega and Synology NAS. Although hackers did not sign their messages like Cl0ud SecuritY last year, and used a different email address, the ransom note text is very similar and suggests the same people are behind these incidents.