Google developers have fixed a serious vulnerability in gmail that also affected G Suite.
In fact, the problem allowed an attacker to impersonate any Gmail and G Suite user and send emails on behalf of someone else, bypassing security mechanisms such as SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting, and Conformance).Allison Husain discovered this vulnerability in April of this year, and Google had more than 130 days to fix the bug.
However, Google developers decided to postpone the release of the patch, planning to fix the problem only in the fall, and Hussein agreed that she had waited long enough. Yesterday, the specialist published information about the issue on her blog, attaching a PoC exploit to the report.
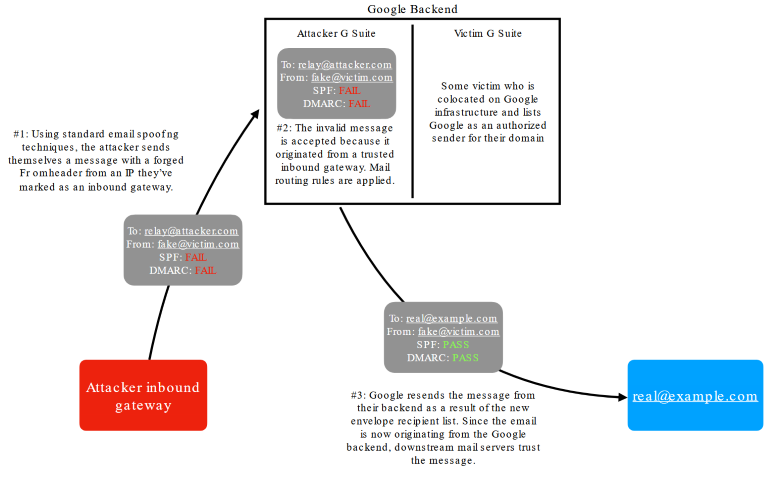
The researcher says that vulnerability has two parts. The first part of the problem is a bug that allows an attacker to send fake emails to the Gmail and G Suite backend gateway.
For example, an attacker can launch or rent a malicious mail server in the backend of Gmail and G Suite, pass an email through it, and then take advantage of the second component of the problem”, – says Allison Husain.
The second part of the vulnerability allows an attacker to configure his own routing rules that will accept incoming email and redirect it, spoofing the identity of any Gmail or G Suite client using the built-in Change envelope recipient feature. At the same time, the forwarded letter is checked for compliance with the security standards SPF and DMARC, which only helps the attacker confirm the authenticity of the fake message.
Hussein demonstrated the problem by using her G Suite custom domain and posing as [email protected].
In addition, there is a possibility that such messages will have a lower spam rate since they come from the backend of Google, which means that filters will respond to such messages less often”, — says Hussein.
Just seven hours after the vulnerability was disclosed, Google engineers said they had taken all the necessary measures to prevent possible attacks. Now, users can safely wait for the patch scheduled for September.
Let me also remind you that recently Google experts reported that they are blocking in Gmail 18 million phishing emails related to COVID-19 over the week.