The hacker group behind the Genesis marketplace infrastructure said the platform was sold to an unnamed buyer. Interestingly, just three months ago, US authorities sanctioned Genesis Market, confiscated some of its domains, and claimed to have gained access to the backend.
Genesis launched at the end of 2017 and by 2020 has become one of the most popular marketplaces.
Genesis mainly sold credentials (including for Gmail, Netflix, Spotify, WordPress, PayPal, Reddit, Amazon, LinkedIn, Cloudflare, Twitter, Zoom, Ebay and so on) cookies and so-called fingerprints (digital fingerprints, bots, and to put it simply – ready-made virtual personalities) for various devices.
Genesis provided customers with its own Genesis Security browser, which criminals could use to import purchased fingerprints and impersonate victims using their IP addresses, session cookies, OS information, and installed plugins.
Law enforcement believes that marketplace administrators have earned more than $8.7 million since 2018.
As of April 2023, more than 1.5 million fingerprints have been sold on Genesis (with more than 2,000,000 stolen identities).
At the end of June, several messages about the sale of Genesis appeared on hacker forums at once, written by the GenesisStore account, which had previously published posts on behalf of the marketplace administration.
These messages said that “everything is being sold, including the complete database (except for some details of the client base), source codes, scripts”, and with “certain agreement” even server infrastructure.
Last week, the same account stated on the Exploit hack forum that the deposit has been made, the marketplace has been sold and “will be transferred to a new owner next month.” The message also notes that the accounts on the forums will not be transferred to the new owner, and he will create new ones “if necessary.”
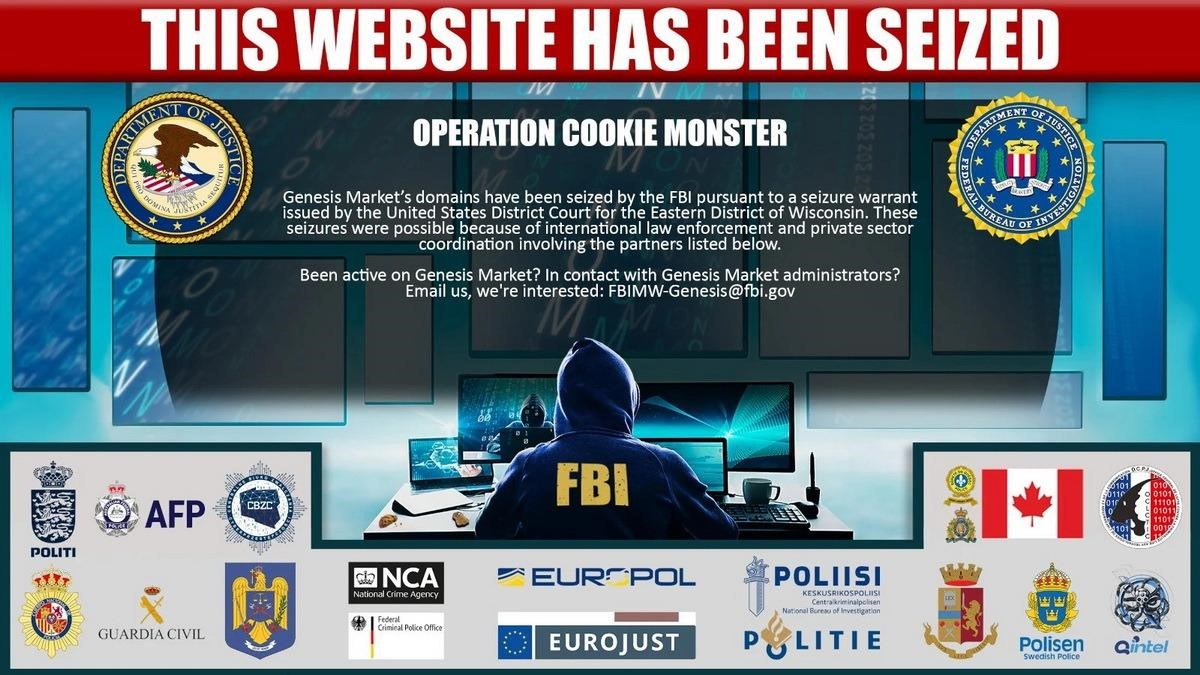
The Genesis sale comes just a few months after the massive Cookie Monster operation, which involved law enforcement agencies in 17 countries and was coordinated by the FBI.
In April of this year, Europol, the FBI and the US Department of Justice reported that they were able to access the backend of the resource and the data of 59,000 user accounts, revealing the real identities of many of them. As a result, during this operation, 119 arrests and 208 searches were made.
At the same time, all three Genesis domains on the open Internet were replaced with a special “stub”, informing users that the domain is now under the control of the FBI. Also, all domains (along with the .onion domain, which did not come under the control of the authorities) were included in the sanctions list of the US Department of the Treasury, in which Genesis is listed as based in Russia.
Do you hate Russian cybercriminals as much as we do? For example, we wrote that the FBI eliminated the Russian spyware, but Microsoft warns of all new attacks.

