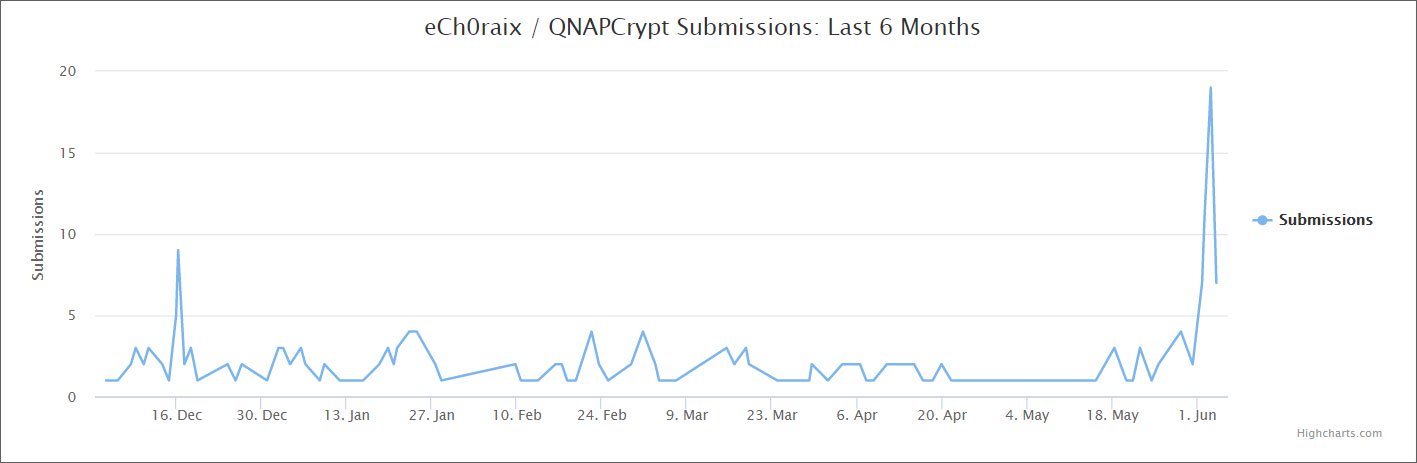
The Bleeping Computer magazine warned that the eCh0raix ransomware operators have noticeably intensified and again quite successfully attacking QNAP NAS devices.
Let me remind you that in July 2019, researchers at several information security companies discovered the eCh0raix ransomware (also known as QNAPCrypt), which since 2018 has attacked QNAP NAS devices, encrypted victim files, and demanded a ransom of 0.05-0.06 BTC or more.At the time the malware was discovered, there was no way to decrypt the data without paying the ransom to the attackers”, – report Bleeping Computer journalists.
Later, at the end of the summer of 2019, an information security expert known under the pseudonym BloodDolly published a special utility on the Bleeping Computer forums for decrypting the affected information. In fact, this tool allowed brute force victims to pick up the decryption key and save their data.
However, when eCh0raix has returned, this utility no longer works – the malware developers have corrected the flaws in the encryption code.
A new surge in malware activity occurred on June 1, 2020: many new victims appeared on the Bleeping Computer forums and the ID-Ransomware ransomware identification site.
Apparently, hackers gain access to QNAP devices through known vulnerabilities or by cracking weak passwords. As soon as the attackers gain access to the NAS, they install their ransomware on the device, which encrypts the files, adding the .encrypt extension to them.
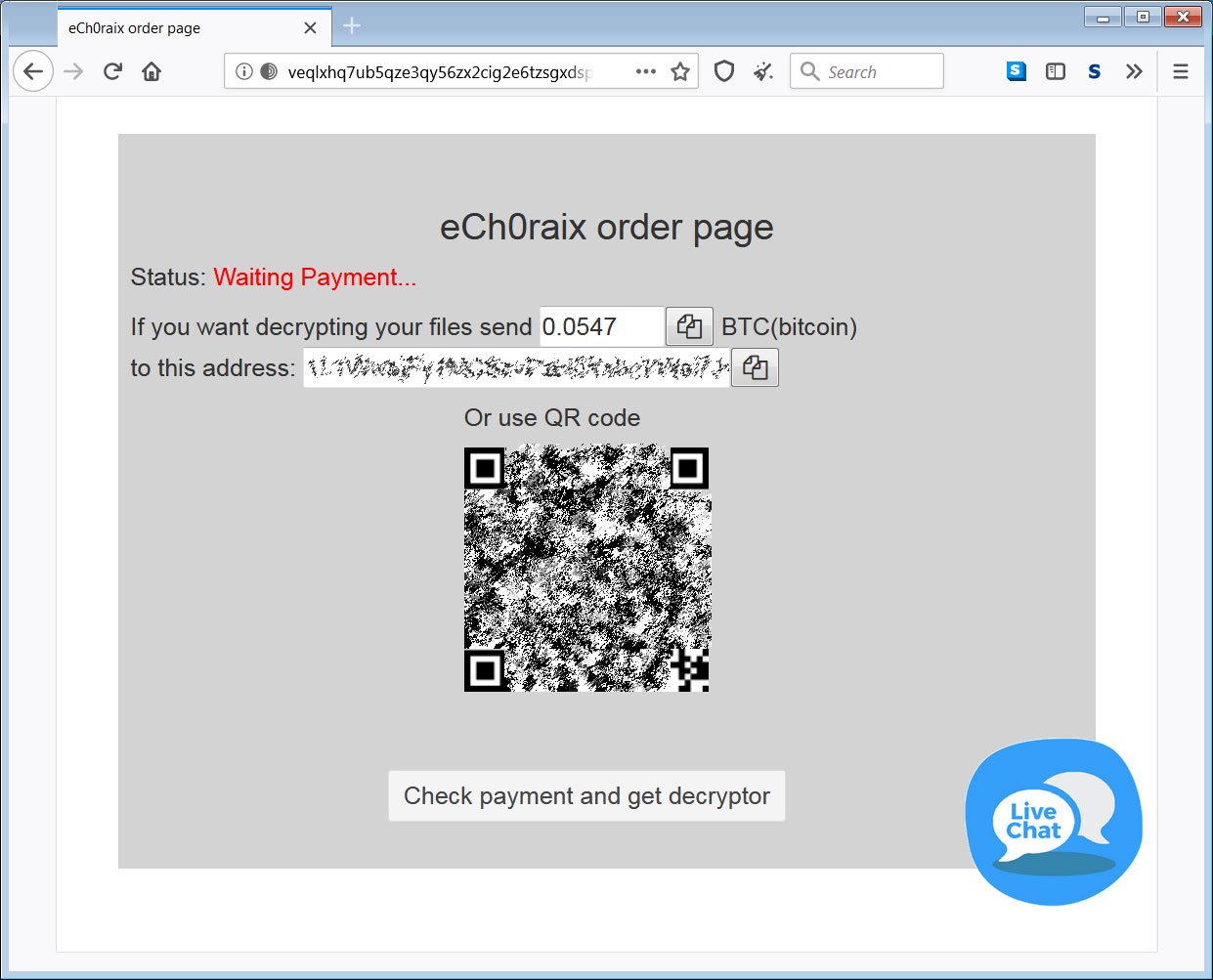
Also, victims have left a note demanding a ransom README_FOR_DECRYPT.txt, which contains a link to the onion-site for payment. On this site, hackers require approximately $ 500 from victims to obtain a decryptor.
In addition, one of the victims reported that after hacking, he found strange applications on his QNAP device. It is not yet clear whether they are associated with malware and are malicious packages installed by cybercriminals, or these are ordinary user packages that were encrypted and the device cannot read them correctly.
There is currently no way to recover files for free unless the user has QNAP Snapshot enabled on the device”, – told in Bleeping Computer.
Researchers remind that owners of QNAP NAS should remember and follow simple safety rules:
- update QTS to the latest version,
- install and update Security Counselor,
- use strong passwords,
- disable SSH and Telnet (if not used),
- enable Network Access Protection and brute force attack protection,
- avoid default ports (443 and 8080), enable QNAP Snapshot.
Overall, it is not recommended to connect the NAS device to the Internet without urgent necessity.
Howeve, not only eCh0raix should be afraid of QNAP NAS devices, let me remind you that QSnatch malware infected thousands of QNAP NAS devices.

Great article and summary of current situation. Lets hope there’s a fix for loyal QNAP users. Limited help online provided so far by Qnap – putting the blame back on the user is a cop out.