Bleeping Computer reports about an unusual hacker campaign launched this month – a certain group of hackers under the name CyberWare attacks various financial fraudsters.
Last week, an information security specialist, known by the pseudonym GrujaRS, noticed the emergence of the not-so-ordinary cryptographer MilkmanVictory. As it turned out, hackers from the CyberWare group created this malware, and the main task of this malware is not to extort ransom for decrypting data, as it usually happens, but to destroy information. The fact is that the ransomware was created for attacks against scammers.Representatives of the CyberWare group first announced news on Twitter, and then agreed to answer questions from Bleeping Computer journalists. The hack group explains that the main target of their campaign are the companies, involved in the so-called credit fraud.
The victims say that they were promised to give a loan, but it turned out that at first it was necessary to pay [the scammers] in order not to get anything in the end”, — say the hackers.
In particular, the group attacked the German company Lajunen Loan, website of which is currently unavailable. CyberWare members launched a DDoS attack on the resource, and also sent phishing emails to the company’s addresses that infected MilkmanVictory. These messages contain links to malicious executable files disguised as PDF files.
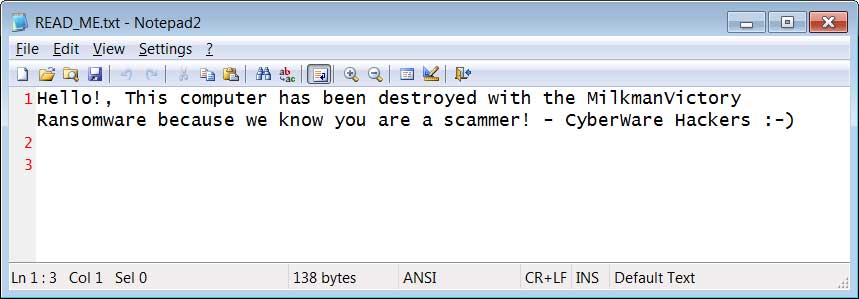
The cryptographer MilkmanVictory was conceived as a wiper. This malware intentionally does not save the encryption key and does not offer victims to contact hackers to pay the ransom. Instead, the message that the malware leaves behind says:
Hello! This computer was destroyed by the MilkmanVictory ransomware because we know that you are a scammer! CyberWare Hackers 🙂 ”.
CyberWare emphasized that they did not demand money from scammers, since criminals that steal funds from innocent people do not deserve this.
Bleeping Computer journalists note that MilkmanVictory was built on the basis of the famous open-source cryptographer Hidden Tear, which for a long time investigated information security experts. This means that even if the encryption key has not been saved, the affected data can still be restored. For example, for this you can use the free tool Hidden Tear Decryptor, created by the famous information security expert Michael Gillespie.
However, let’s remember that criminals who hide behind noble goals are criminals anyway. For example, a ransomware named RobbinHood has already done a lot of damage, and the Maze cryptographic operator promised not to attack medical facilities during the COVID-19 epidemic, but quite soon broke their promises.

ecryptor for STOP Djvu not working on .covm