Csrss.exe process is a legitimate Windows process. It belongs to Client Server Runtime Subsystem, that carries several important functions in the operating system. The peculiarity of that process is that it is often counterfeited by viruses, primarily – by coin mining trojans1. If you see in Task Manager that this process consumes more than 10% of your CPU, it is not ok. Read the article to know how to figure out the malware, and how to remove it from your PC.
Why does the csrss.exe process consume so much CPU capacity?
The legitimate process never takes more than 10% of your system power. Moreover, the functions csrss carries are usually performed when the user will likely not admit this. This process is responsible for correct data saving at the moments of logout/shutdown of the PC. Another, and less needed function is providing the console access for the apps at the moment of their startup2. During the operations, the access is granted by another system process – conhost.exe.

If you have a performance problem and see that the csrss process has the lion’s share of CPU consumption, there is bad news for you. Your PC is likely infected with the coin miner virus or another dangerous malware that tries to stay unseen. Trojan-miner is a specific type of malware that performs quite a small amount of functions – it only mines cryptocurrency coins using your CPU and GPU. While you have no programs running, you will not fill any suspicious moments. But when you even try to start a browser – the troubles begin.
How dangerous csrss virus is?
csrss.exe process will make use of more than 70% of your CPU’s power and also graphics cards resources
The biggest damage can be dealt to mobile devices, i.e. laptops. This type of device is not designed to constantly cool the system if it works at 100% of its capacity. In a typical (for most laptop users) situation, when you have your device on your lap, you can unintentionally close the air intake holes, so the cooling will not serve properly. With luck, your laptop will just turn off due to the CPU throttling3. But some outdated systems, can have no throttling prevention mechanism, and such a strong overheating will surely lead to further CPU issues.
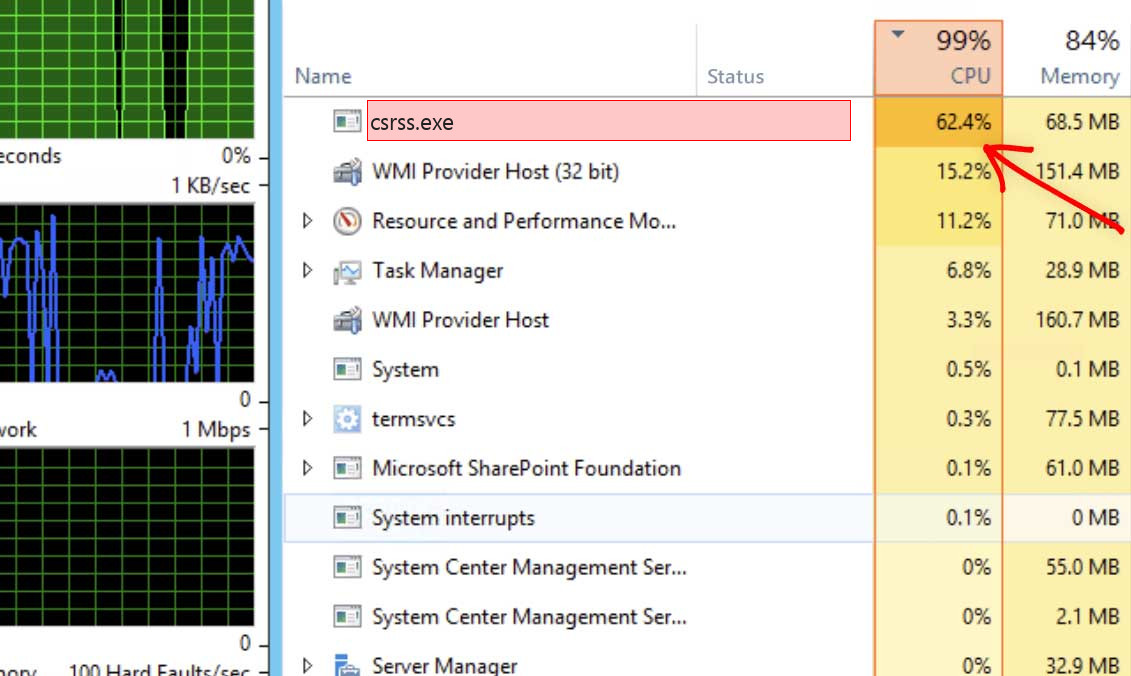
Desktop users will likely have less problems. But it is still an unpleasant experience to struggle with opening a browser window or to wait for a minute while Photoshop attempts to create a new layer. CPU miners don’t care about the user. Their target is to squeeze all possible coins from a single computer. The legit and familiar (at first sight) csrss process can spontaneously start to consume up to 90-95% of CPU power.
| File Name | csrss.exe |
| Type | Trojan Coin Miner |
| Detection Name | Trojan:Win32/CoinMiner |
| Distribution Method | Software bundling, Intrusive advertisement, redirects to shady sites etc. |
| Similar behavior | Seed, Sheedscannerservice, Ie |
| Removal | Download and install GridinSoft Anti-Malware for automatic csrss.exe removal. |
Csrss virus distribution ways
There are three main ways of malware spreading used by coin miners developers. Malvertising is the most popular one, second by its share is software bundling, and the worst among the best is email spamming. Let’s check out each of them to understand how to detect that you will trap and how to evade it.
Malicious advertisements on the web, however, is an old-timer of malware distribution. And the advice to stop clicking the blinking advertisements on untrustworthy websites exists as long as the ads are on the Internet. You can also install ad-blocking plugins for your web browser – they will deal with any ads. However, if these ads result from adware activity already present on your PC, ad blockers will be useless.
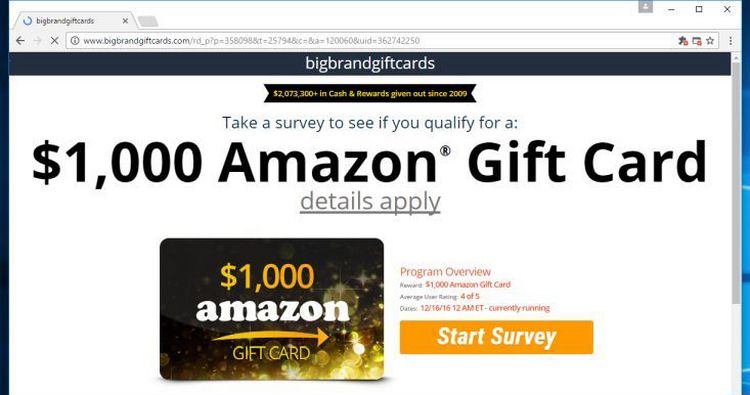
Example of malvertising
Software bundling is a widespread practice among the virus developers. Users who hack the programs to make them usable without purchasing a license approve any offer to include another program in the pack because they are gaining money in such away. Check precisely the installation window for signs like “Advanced installation settings” or so. The ability to switch off the malware installation often hides under such items.
The users do not raise suspicion on notifications from DHL or Amazon about the incoming delivery. Hence, it is straightforward to make the user believe that he opens a legit attachment from an accurate delivery report. Till he is not raising suspicion, the virus can do whatever it wants. However, it is pretty easy to distinguish the nasty email from the original one. One sent by cybercriminals has a strange sender address – something like [email protected]. Simultaneously, the actual email address has a specific domain name (@amazon.com or @dhl.us) and can also be seen on the official website in the “Contact us” tab.
How can I know that the csrss process is a legit or malicious one?
Unlike ransomware, cryptocurrencies extracting hazards are not meddlesome and are most likely to remain undetected by the target.
It is quite easy to check if the Client Server Runtime process is a real system task or a malicious copy. The first way is to check the thread the process belongs to. By default, csrss.exe is a system process, so it is listed together with other Windows processes in the thread with the same name. You can spectate two instances of that process running simultaneously. That is nothing strange until both of them are among Windows processes:
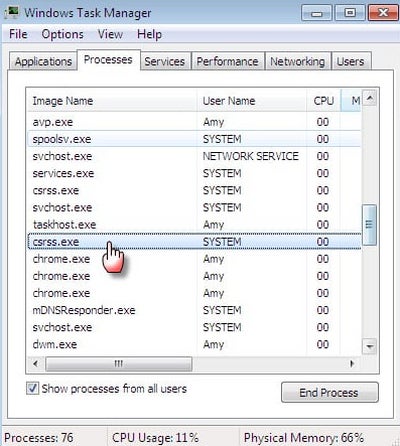
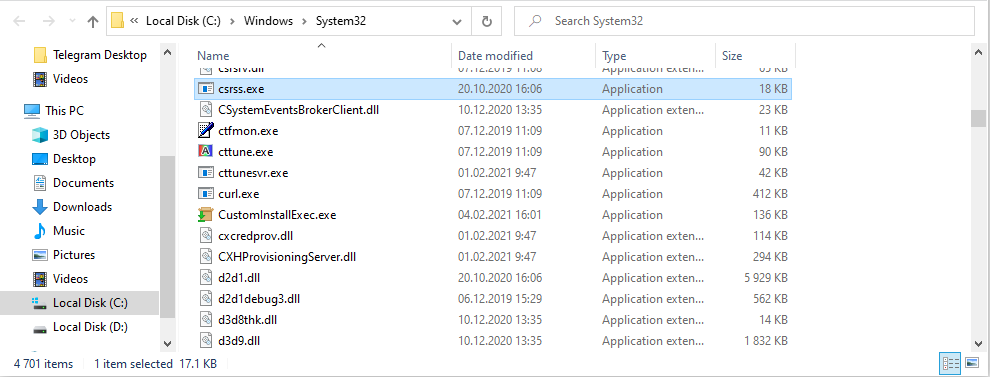
If the csrss runs as a user process – it is time to raise suspicion. Check the location of this process by clicking the right mouse button. Then, choose the “Open file location” option. The legit process is stored in the C:/Windows/System32 folder. All other locations mean that this process is fake, created by malware programs.
How to remove the csrss virus?
As I promised, here is a removal guide for the case if the csrss.exe process is a virus. It is likely impossible to delete this virus manually since it changes the registry and system settings. It is better to use antivirus software because it will revert all changes in one click.
Microsoft Defender, which looks like an obvious solution, has several significant troubles, which makes it impossible to be used for malware removal. First, users often disable this antivirus program because it consumes many hardware resources while being active. Turning it back on is a tough task. Another problem is that trojan viruses can disable that antivirus solution and block all attempts to enable it back while staying active. That’s why it is better to use a separate antivirus. My choice for that case is GridinSoft Anti-Malware.4
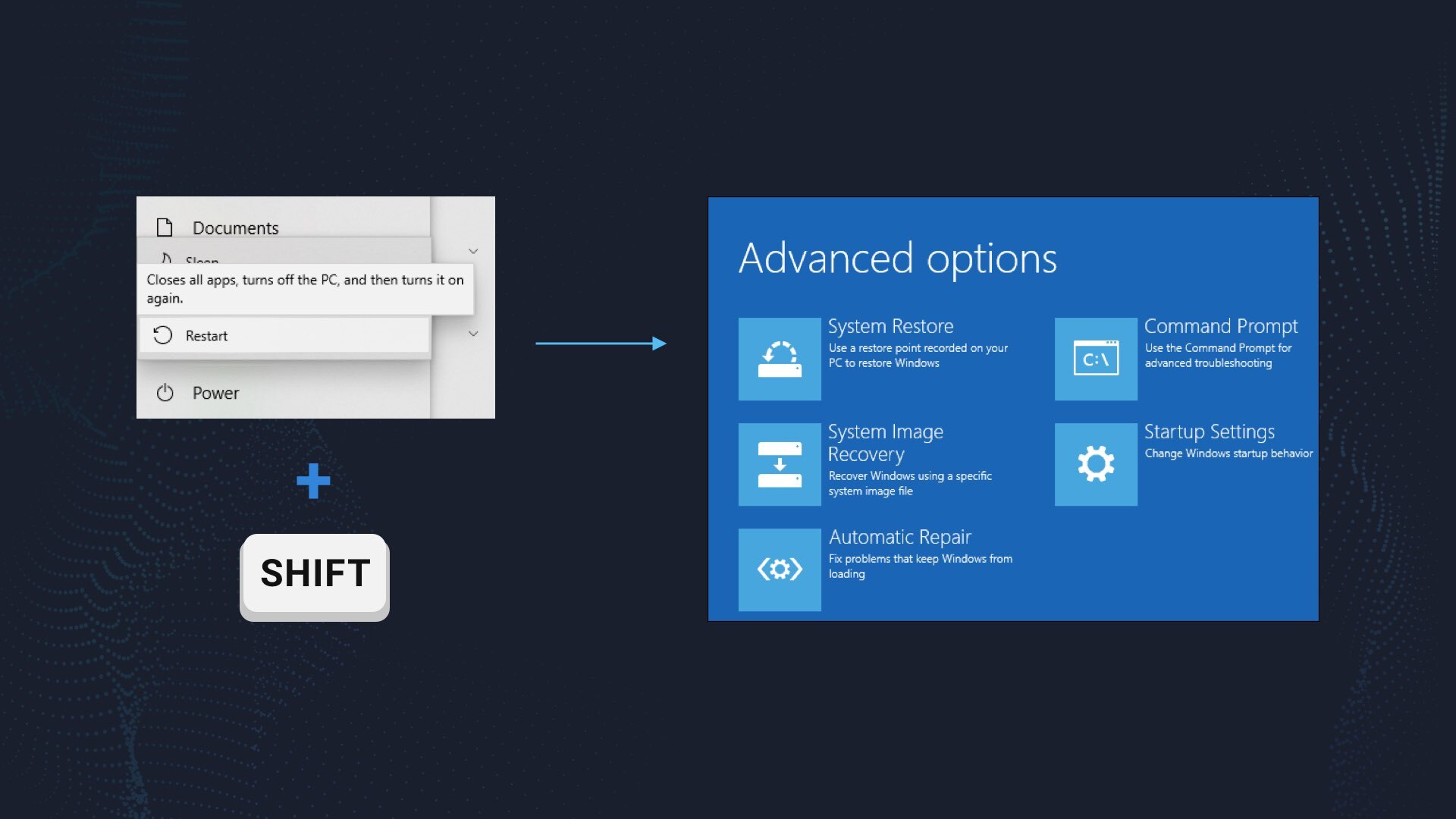
Enable the safe mode with networking
Before the removal process, it is recommended to boot your Windows into the safe mode with networking. Go to Start, click on the Power button, press on Shift button on the keyboard and choose the “Restart” option. You will boot your PC into troubleshooting mode.
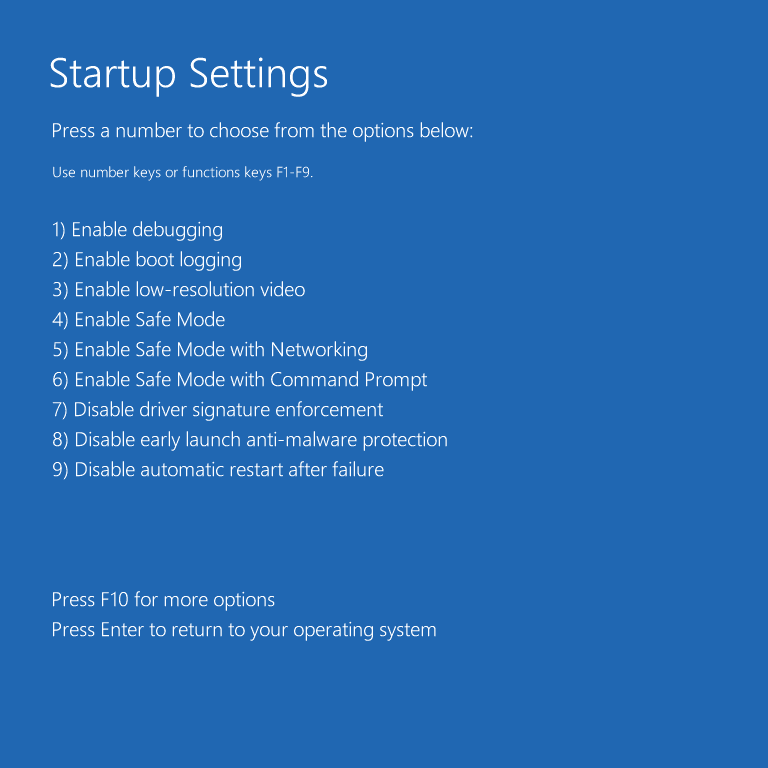
In this menu, choose the Startup Settings. On the screen appeared, press F5 to activate the Windows safe mode with networking. This mode disables the launch of all programs despite the initial Windows processes. Hence, the malicious copy of csrss.exe will not be running and consuming so much CPU power.
Remove the viruses with GridinSoft Anti-Malware
Download the GridinSoft Anti-Malware installation file (install-antimalware-fix.exe). Double click it to run the installation.
When the program is ready, it will offer you to activate a 6-day free trial. Then, you can start scanning. For the csrss virus, it is better to use a Full scan.
This scan may last for up to 20 minutes. You are free to do everything you want because GridinSoft Anti-Malware is very friendly to the PC resources.
When the scan is over, click “Clean it” to get rid of the viruses. This operation is usually done in less than a minute, but you may need to wait a little bit if there are many viruses.
User Review
( votes)References
- Article about trojan-miners.
- More information about csrss.exe process on HowToFix website.
- About CPU throttling on Wikipedia.
- Reasons why I recommend GridinSoft Anti-Malware for virus removal.

