Rapid7 researchers have reported about bugs that can help hackers to remotely disable Fortress Security Store’s home security systems.
Fortress Security Store is an American security solutions provider. The company claims that its products are used by thousands of consumers and companies.Researchers have found vulnerabilities in the Fortress S03 WiFi security system, which connects to an existing Wi-Fi network or telephone line. This system can be integrated with CCTV cameras, window and door sensors, motion sensors, glass break and vibration sensors, as well as smoke, gas and water sensors.
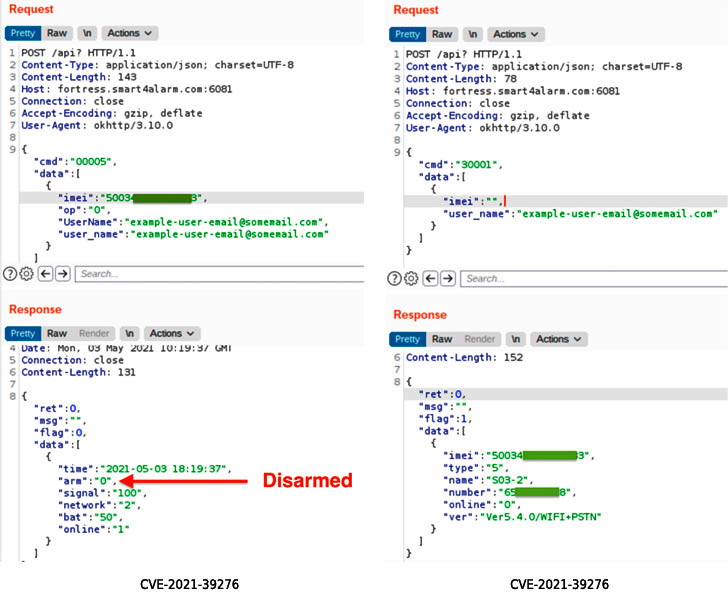
The product was exposed to two vulnerabilities that could be exploited remotely. They are rated as medium severity bugs on the CVSS scale (5.3 and 5.7, respectively).
The first bug (CVE-2021-39276) is the problem of accessing the API without authentication.
The second bug (CVE-2021-39277) can be used to launch an attack with an RF signal.
In this case, the attack does not require any prior knowledge of the target system, but can only be carried out within the range of RF signals.
Rapid7 reports that it notified the Fortress Security Store of bugs back in May 2021, but the company closed the ticket after 11 days and stopped responding to researchers.
Apparently, the vulnerabilities have not yet been fixed, so experts advise owners of vulnerable security systems to use unique and specially registered e-mail addresses (so that attackers do not find out the email address and IMEI), and also avoid using special key fobs and other RF- devices connected to security systems.
Let me remind you that we also wrote that Millions of IoT Devices are at Risk due to Bugs Found in Realtek Wi-Fi SDK.