A bug in the IndexedDB API in the Safari WebKit engine can be used by malicious sites to track users’ online activity and reveal their identity.
The vulnerability was dubbed IndexedDB Leaks and was discovered by FingerprintJS, a company that develops anti-fraud software. Researchers notified Apple developers about the problem back in November 2021.IndexedDB is a widely used browser API that provides a general-purpose client-side storage system (with no capacity limits). The API is typically used to cache web application data for offline viewing. In addition, modules, development tools and extensions can use it to store information.
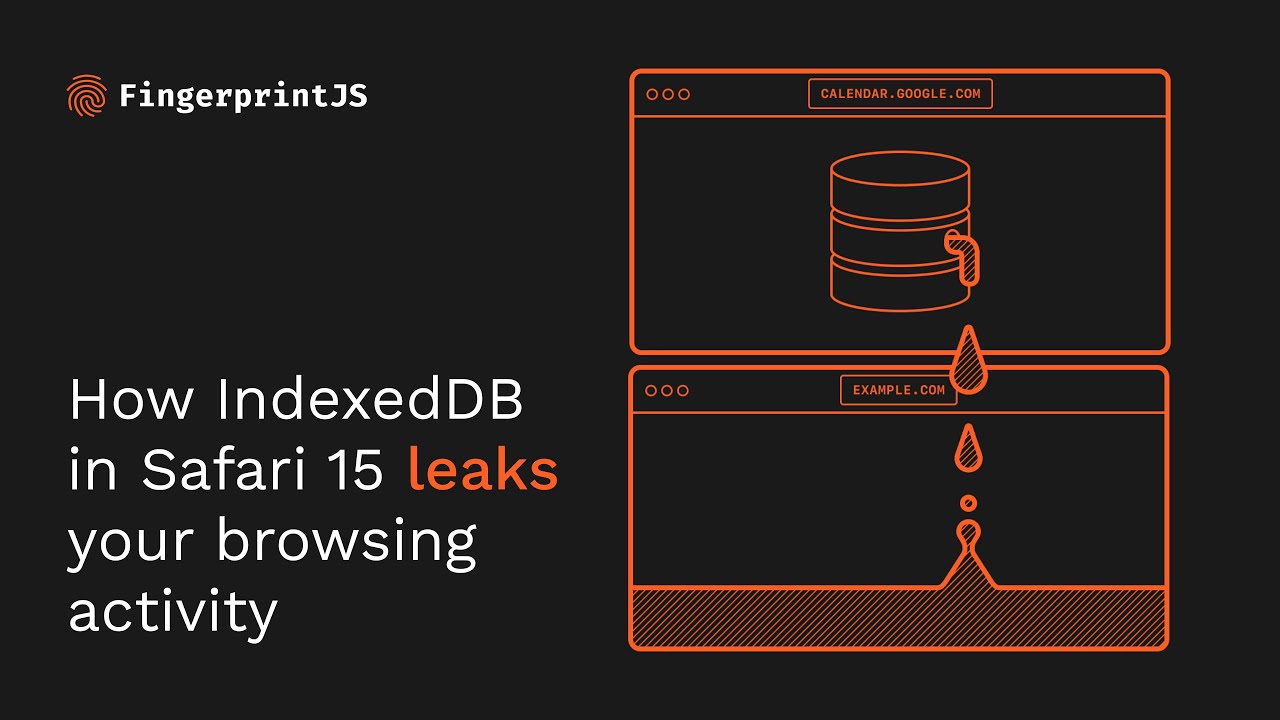
To prevent potential data leaks through XSS attacks, IndexedDB adheres to the Same Origin Policy, controlling which resources can access certain pieces of data. However, FingerprintJS analysts have found that IndexedDB does not follow the SOP in Safari 15 on macOS, resulting in the disclosure of sensitive data.
Browsers that use the same engine in the latest versions of iOS and iPadOS are also affected by the bug. In addition, the root of the problem lies in WebKit, which means that any browser that uses this engine (for example, Brave or Chrome for iOS) is also vulnerable. To check your browser for leaks, you can visit a special page created by FingerprintJS analysts.
Experts explain that the bug allows any site to find out the names of databases created within a single session. Since the database names are unique and site-specific, the bug actually provokes a leak of a browsing history. Worse, some database names contain user IDs, so a leak can lead to user identification as well.
According to analysts, to identify a person using this vulnerability, you need to log in and visit popular sites such as YouTube and Facebook, or services such as Google Calendar and Google Keep. When you sign in to these resources, a new database, IndexedDB, is created with the user’s Google ID appended to its name. When using multiple Google accounts, separate databases are created for each of them.
Although Apple reported the vulnerability as early as November 28, 2021, the bug is still unresolved. One way to temporarily mitigate this problem is to completely block JavaScript, but this can cause problems for many sites.
Let me remind you that not only Safari browser has issues. We wrote that Firefox has fixed the “evil cursor” problem, and also that Google Chrome developers fix conflict with antiviruses in Windows 10.