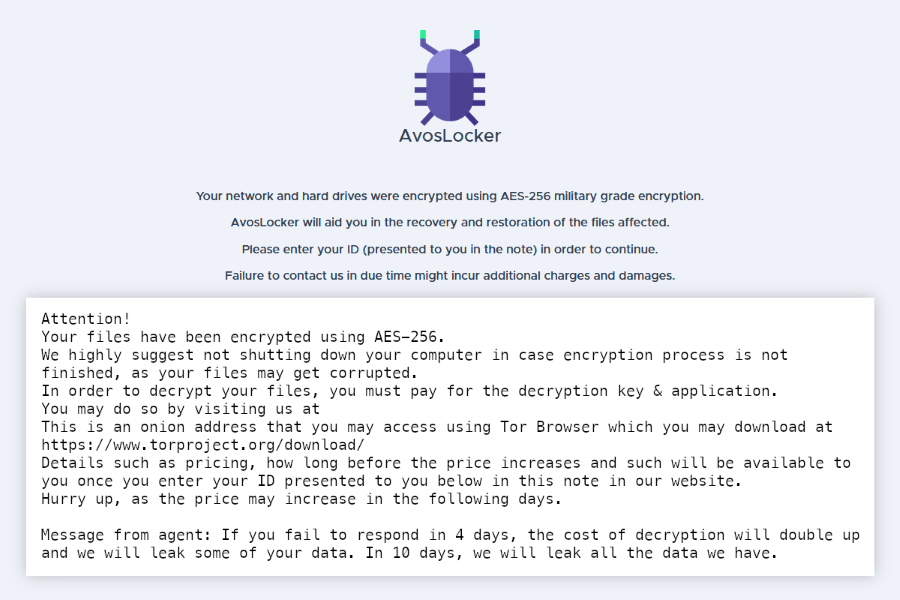
AvosLocker ransomware, a rising star on the ransomware market, conducted another attack at the edge of 2022. However, they soon discovered that their target is one of the US police depts. After such news, they quickly gave up the decryptor and vanished.
AvosLocker ransomware – the newbie
The first mentions of AvosLocker ransomware group appeared in July, 20211. Almost immediately after their first attacks, cybersecurity experts uncovered their main “feature”. The ransomware variant this group uses has a pretty interesting method of bypassing the anti-malware programs shield. After the injection, AvosLocker ransomware reboots the system in a Safe Mode and launches the AnyDesk remote connection tool.
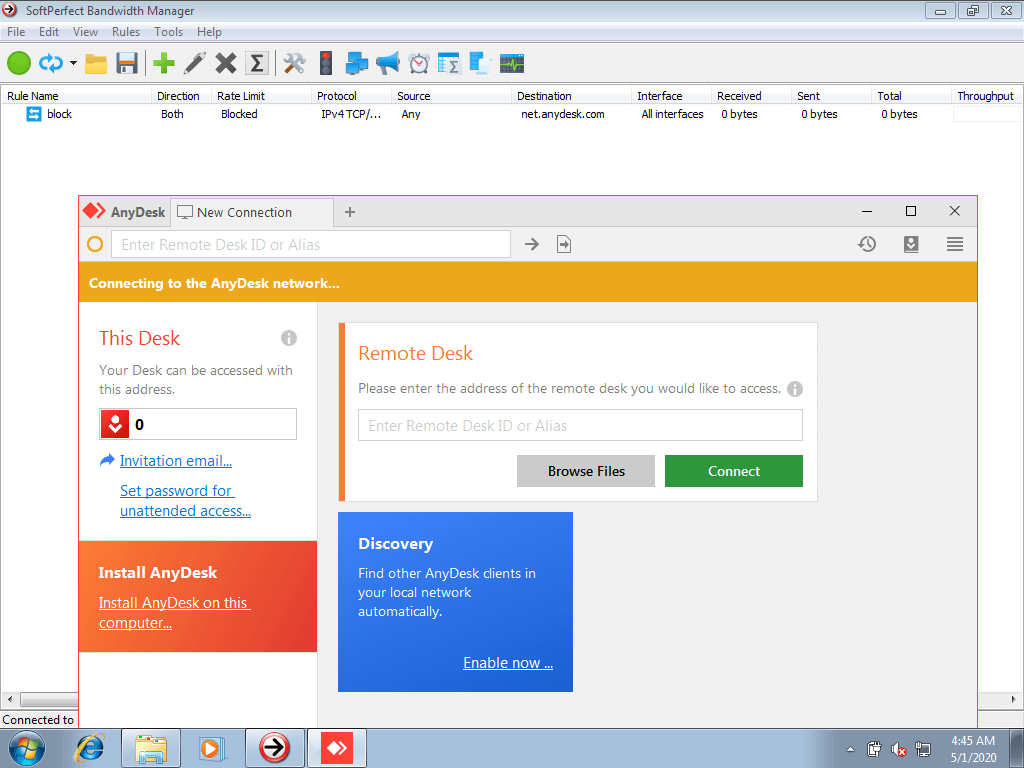
The window of AnyDesk – the program that AvosLocker uses to complete the attack
Such a trick allows this ransomware family to effectively defeat any kind of endpoint protection. It does not matter if you use antivirus software at all, if it will likely be disabled even before it can spot the intruder. At all, the idea to boot the PC into a Safe Mode is not new – it was successfully used by REvil, BlackMatter and Snatch families.
AvosLocker operators gave up the decryptor
Not only small thugs are afraid of the police. AvosLocker claimed several times that they are not afraid of the executive authorities, despite the chain of loud capturings of the members of different gangs. However, the last incident has shown clearly that at least some of their operators are afraid of attention from U.S. law enforcement. It is obvious that all these claims were just a bluff, but all other groups usually follow the “codex” completely, or completely ignore it. This “codex” is a bunch of rules that predetermine the list of sectors that must be avoided. And police departments are right inside of the “governmental structures” paragraph, which is almost #1 in all possible list editions.
When the operators who managed the attack understood that their target was a police department, they likely strong feeling in the pit of one’s stomachs. It is not clear if they understood the error on their own, or someone said it to them. But the fact is still there – they gave up the decryptor in less than several hours after the attack. The cybersecurity researcher under the nickname pancak3 published the screenshot that proofs their reaction:
AvosLocker RaaS operators trying to avoid heat after hitting a US government entity by providing them the decryptor for free. pic.twitter.com/zFg7Idj9Zs
— панкейк (@pancak3lullz) December 29, 2021
The characteristics of one of the AvosLocker samples
| Hash | 92d3d898bbc3e53d869e4d8670cf7f40bfb77a5598f44f03aa54ebad2c3c99113933 |
| Loader name | serfz34 (same as previous AvosRansomware variants) |
| Sample name | avosqr3.exe |
| Summary | Ransomware, present on the system on 2021-14-12 |
| Company | “ValetR” |
| Decryption method | kexec |
| License | GPLv2 |
| Signature | From: Paolo Perrone |
What is ransomware?
Ransomware is a kind of malware that encrypts files and asks a ransom for their “return”. The procedure is pretty simple: after the initial infection (usually done with scripts), ransomware connects to the command server and gets the instructions for this certain target. These instructions generally include the encryption key, extension that is assigned for this victim, and the ransom note. Afterwards, the malware starts the encryption of stored files or data, and releases the ransomware message.
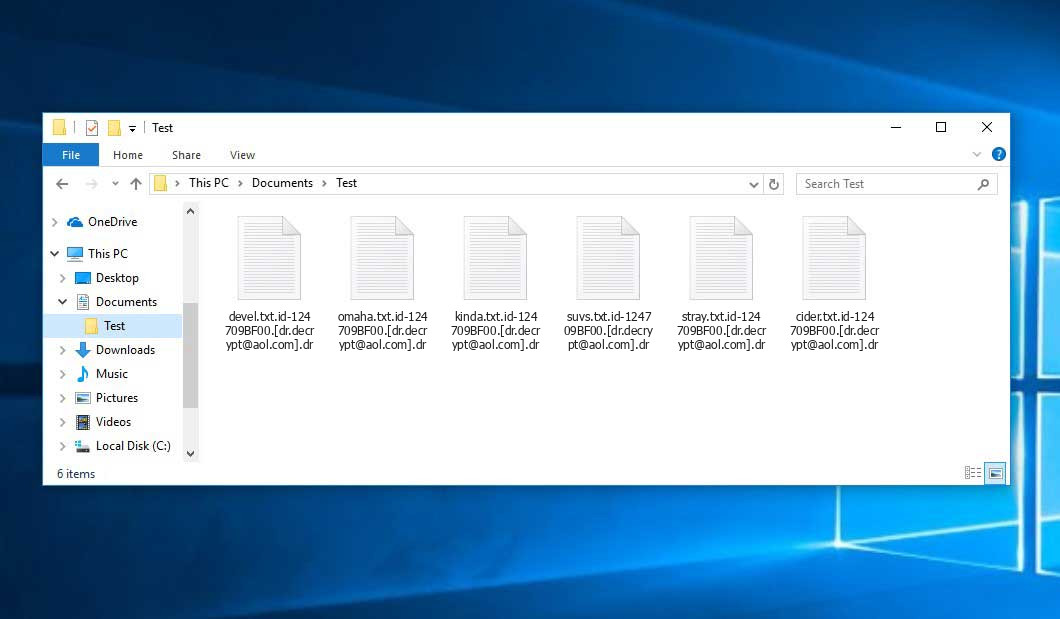
This malware type appeared in 2012 when Bitcoin was first introduced as a payment method. In 2014, it completely squeezed out screenlockers – viruses that block your desktop and ask for the ransom to unlock it. In 2020, after the beginning of the coronavirus pandemic, the cybersecurity world witnessed another pandemic. Massive ransomware strikes on thousands of companies from all over the world happened, and keep happening even after almost 2 years. The overall losses from ransomware activity already reached $20 billion.
User Review
( votes)References
- “Dossier” for AvosLocker ransomware group on PaloAltoNetworks site.