Appyrinceaskeda.com is a Command & Control (C&C) server that plays a crucial role in the distribution and management of VenomSoftX malware. This highly dangerous malware is a JavaScript-based remote access trojan that is primarily designed to steal cryptocurrencies and hijack them. The malware also carries out various other malicious activities such as fingerprinting the infected machine, capturing clipboard content, and executing additional payloads or commands.
| Name | Appyrinceaskeda.com |
| Hosting | AS13335 Cloudflare, Inc. United States, San Francisco |
| IP Address | 172.64.139.9 |
| Malware type | Command & Control (C&C) for VenomSoftX RAT |
| Effect | Remote Access Trojan that is primarily designed to steal cryptocurrencies and hijack them |
| Hazard level | High |
| Malware source | Apps from third-party websites, ads on dubious websites |
| Removal method | To remove possible virus infections, try to scan your PC |
What are Appyrinceaskeda and VenomSoftX?
VenomSoftX is capable of achieving full access to every page that the victim visits by leveraging malicious browser extensions. The malware masquerades as a legitimate-looking extension such as “Google Sheets 2.1” or “Google Docs 1.0” to evade detection by victims. Once installed, these extensions give the malware complete control over the victim’s browser, enabling it to siphon off sensitive information such as login credentials, personal data, and even cryptocurrency wallet addresses.
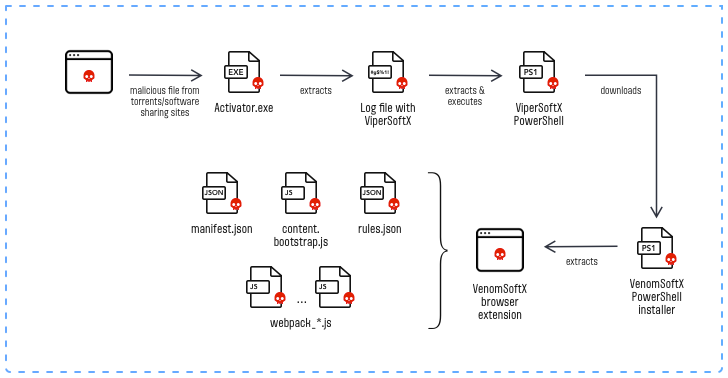
VenomSoftX RAT infection chain
One of the most dangerous aspects of VenomSoftX is its ability to carry out man-in-the-browser attacks. These attacks involve tampering with API requests’ data on popular cryptocurrency exchanges, allowing the attacker to perform cryptocurrency address swapping. By swapping out the victim’s legitimate cryptocurrency wallet address with the attacker’s address, the attacker can effectively steal the victim’s cryptocurrency holdings. Additionally, VenomSoftX can also capture clipboard content, steal login credentials, and manipulate crypto addresses on visited websites.
If you suspect that your computer is infected with VenomSoftX malware, it is crucial to take immediate action. To detect and remove this dangerous malware, we recommend following our guide below. Our guide provides step-by-step instructions on how to check your computer for VenomSoftX malware and remove it safely and for free. By following our guide, you can protect your computer from this highly dangerous malware and keep your sensitive data and cryptocurrency holdings safe.
How to remove Appyrinceaskeda VenomSoftX?
Fortunately, VenomSoftX and Appyrinceaskeda removal is not very complicated. They parasite in the web browser and can’t hide themselves deeply on a disk. Nonetheless, as I stated above, some pop-ups may introduce malicious software to your system. It is nearly impossible to show all of the cases, and manual attempts to remove malware is a poor idea. Thus, after removing the source of the pop-up advertisements it is recommended to use anti-malware software. That is especially recommended in the case when you have never allowed pop-up notifications, and they still appeared. This situation can be a sign of malware activity. GridinSoft Anti-Malware will perfectly fit both system recovery and malware scanning and removal purposes, thanks to its abilities of system recovery and advanced detection system.
Initially, you should reset your browser settings. You can do that in manual or automated way. The former, obviously, requires more time to complete and can be somewhat complicated if you have never done that. Automated supposes the use of anti-malware programs that can reset all browser settings at once.
Reset your browsers with GridinSoft Anti-Malware
To reset your browser with GridinSoft Anti-Malware, open the Tools tab, and click the “Reset browser settings” button.
You may see the list of options for each browser. By default, they are set up in a manner that fits the majority of users. Press the “Reset” button (lower right corner). In a minute your browser will be as good as new.
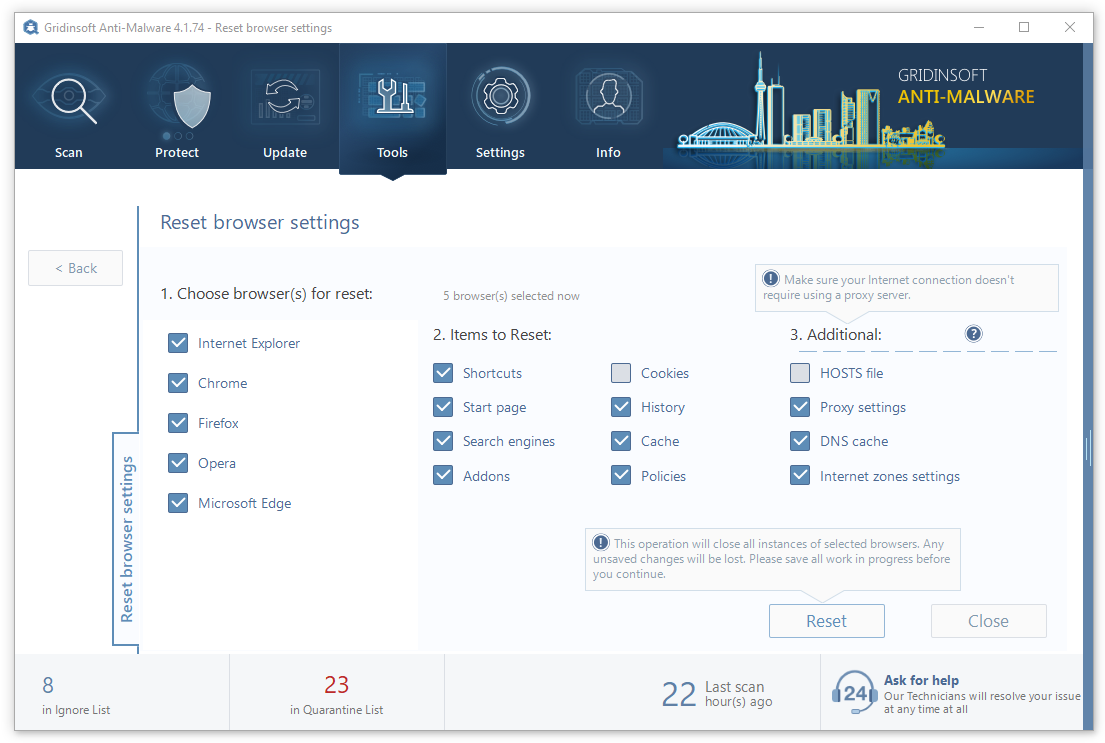
The browser reset is recommended to perform through the antivirus tool by GridinSoft, because the latter is also able to reset the HOSTS file without any additional commands.
Reset your browsers manually
Manual method of browser reset
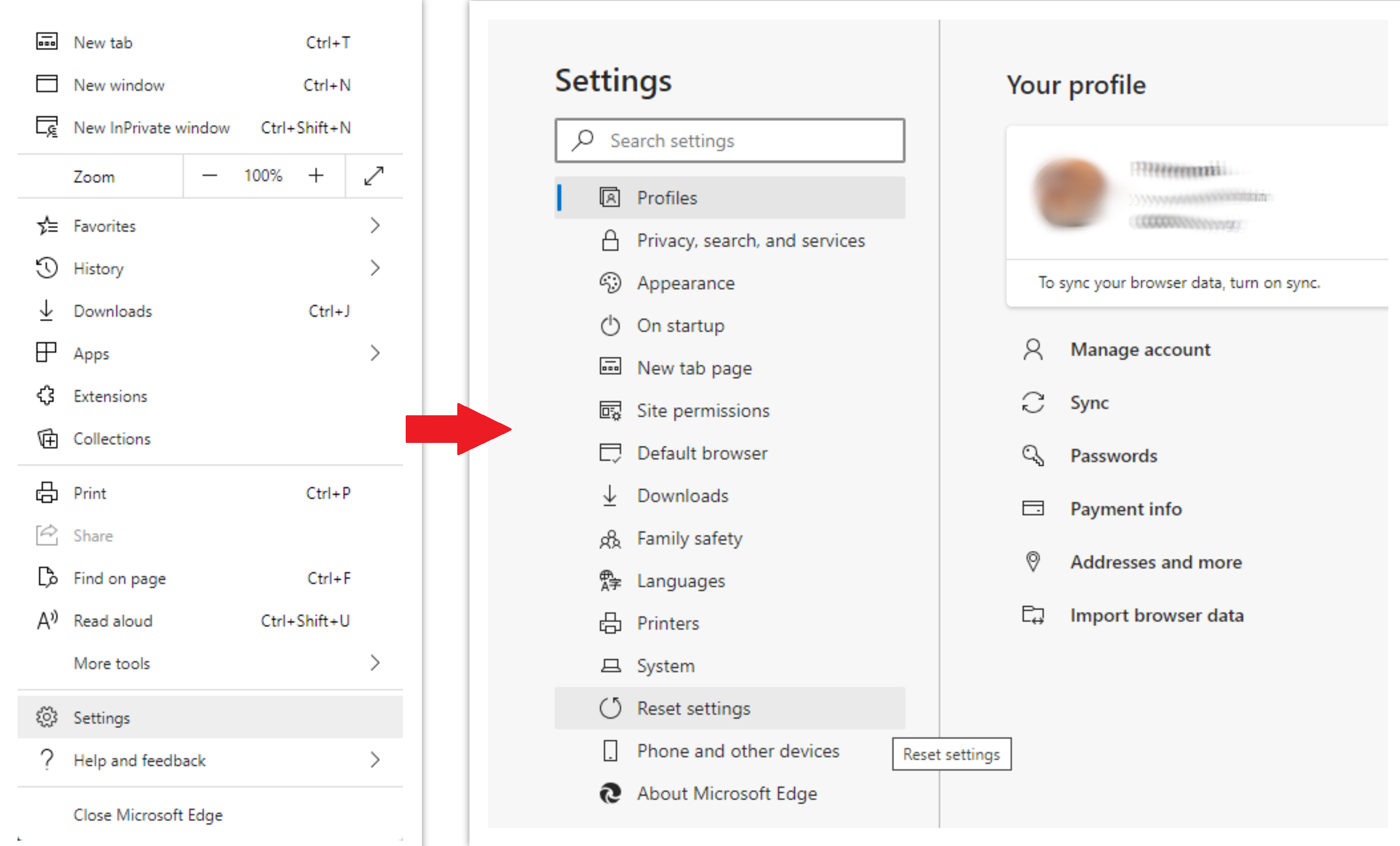
To reset Edge, do the following steps:
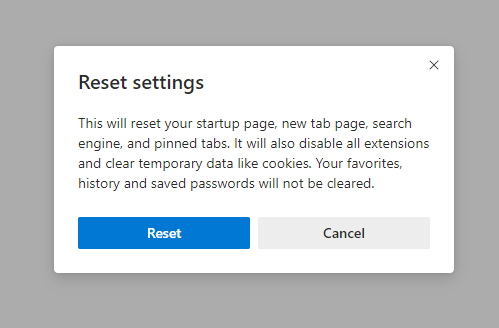
- Open “Settings and more” tab in upper right corner, then find here “Settings” button. In the appeared menu, choose “Reset settings” option:
- After picking the Reset Settings option, you will see the following menu, stating about the settings which will be reverted to original:
For Mozilla Firefox, do the next actions:
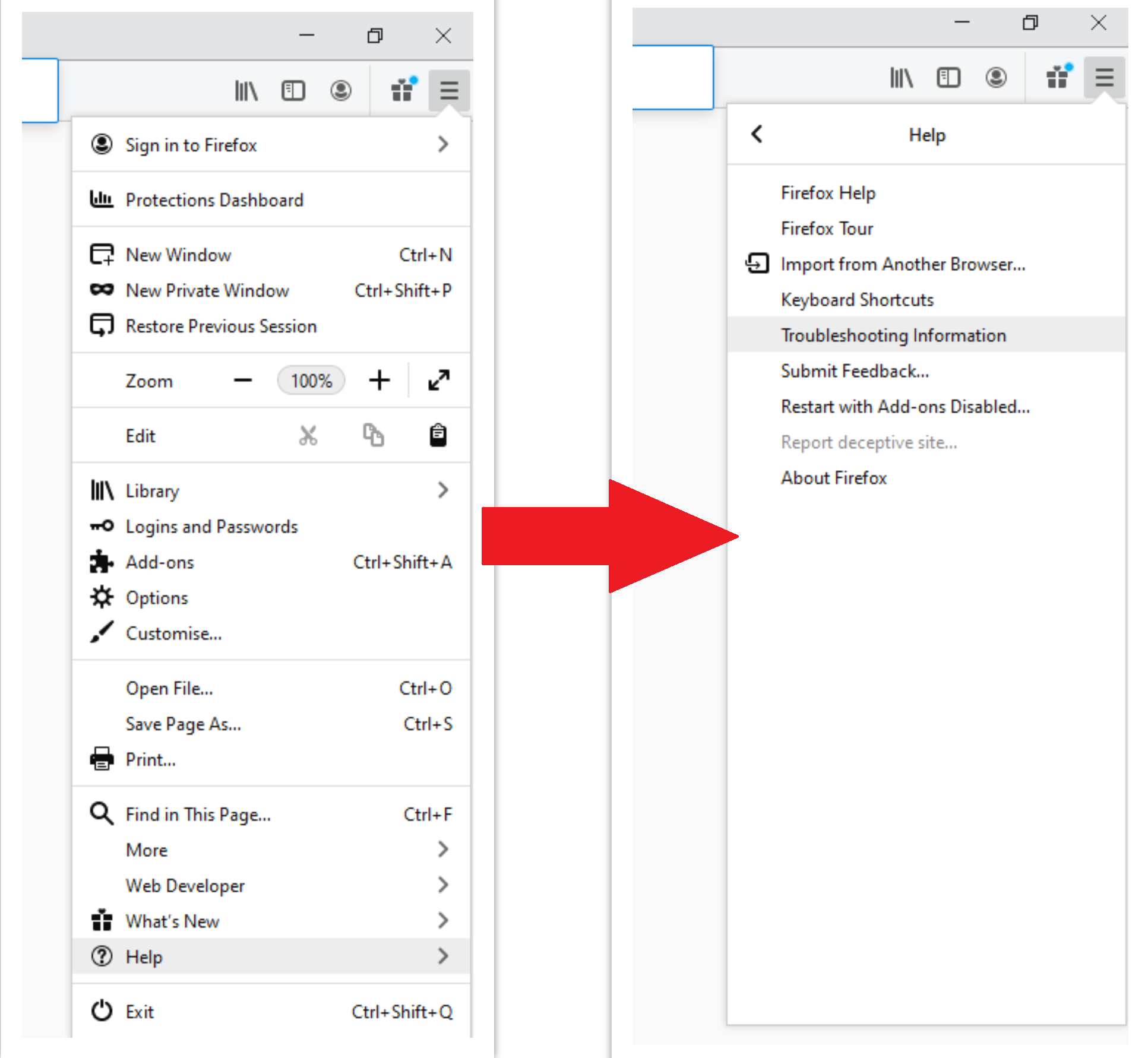
- Open Menu tab (three strips in upper right corner) and click the “Help” button. In the appeared menu choose “troubleshooting information”:
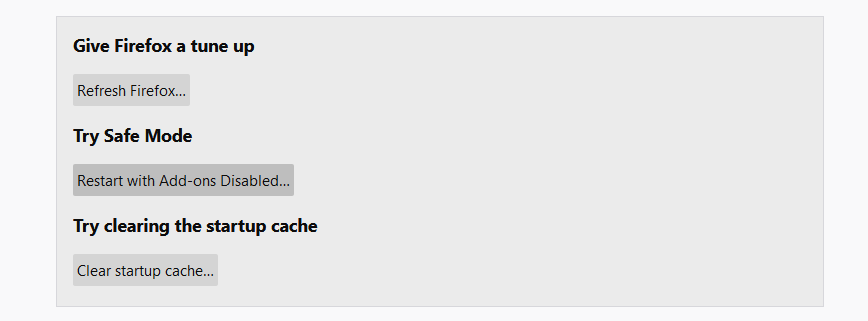
- In the next screen, find the “Refresh Firefox” option:
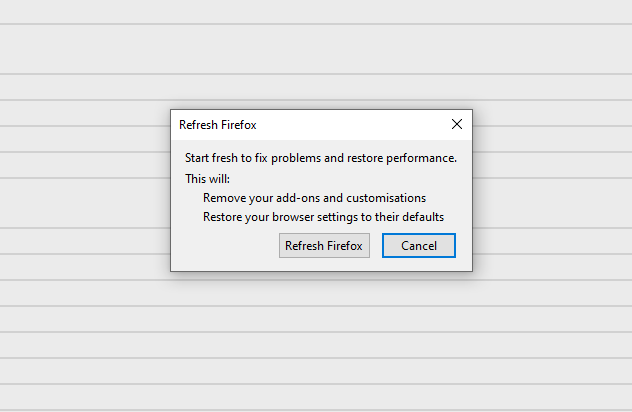
After choosing this option, you will see the next message:
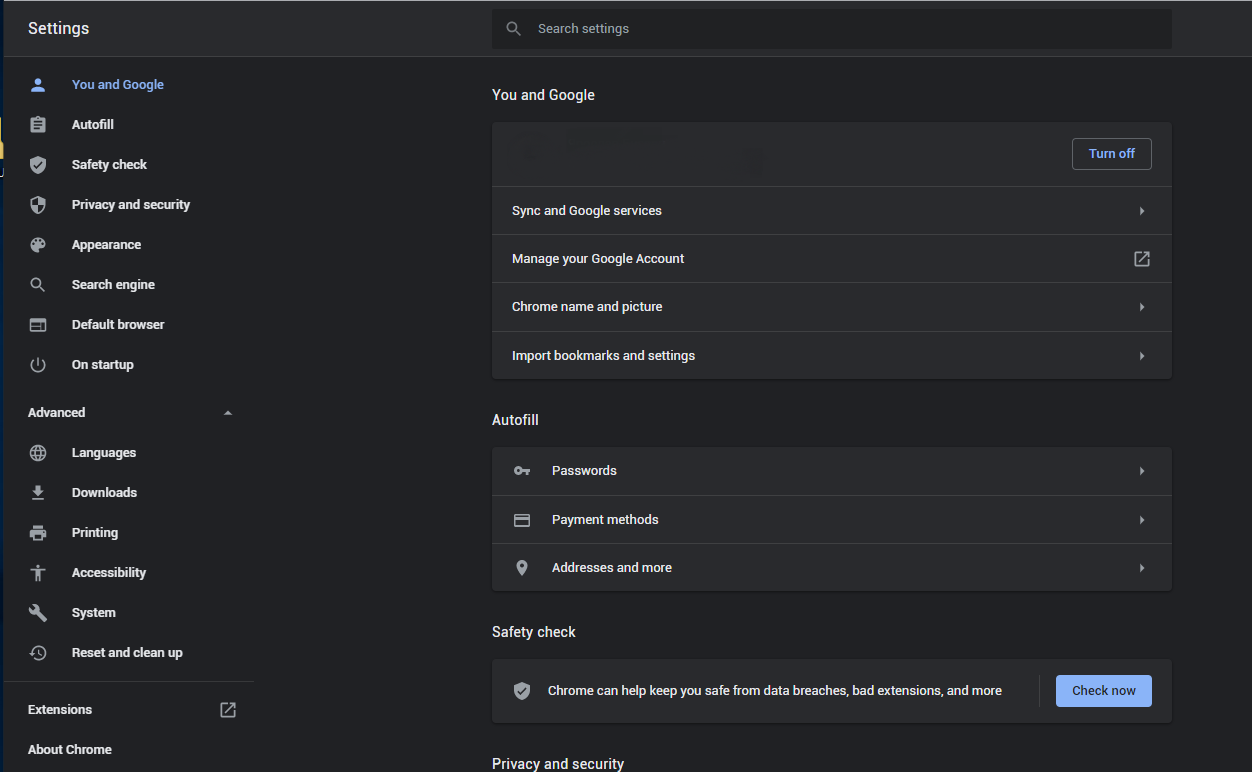
If you use Google Chrome
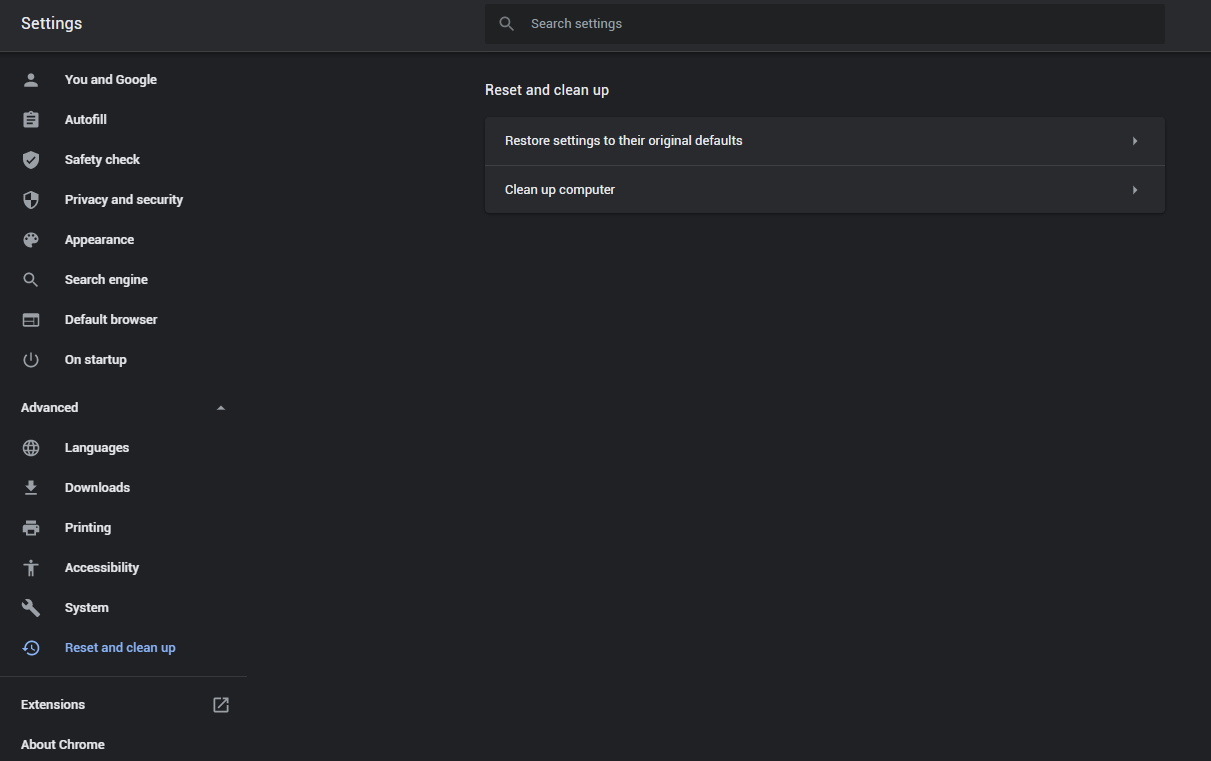
- Open Settings tab, find the “Advanced” button. In the extended tab choose the “Reset and clean up” button:
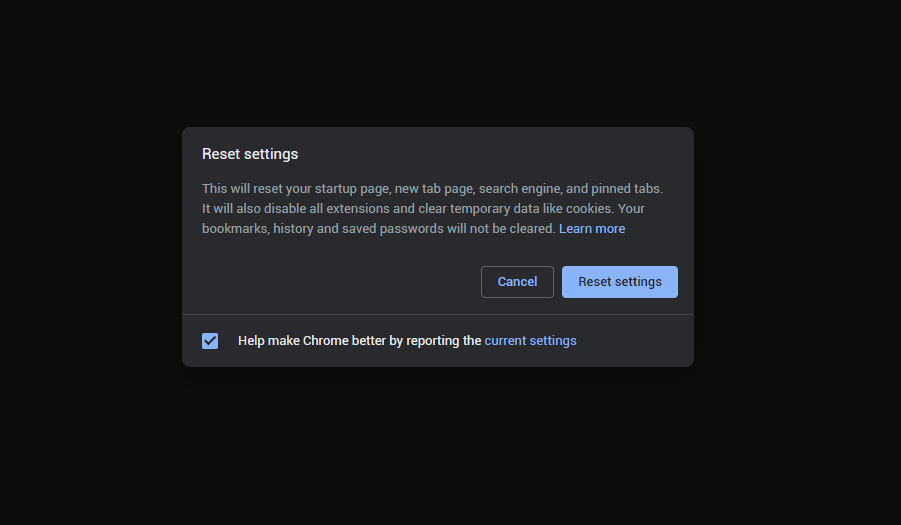
- In the appeared list, click on the “Restore settings to their original defaults”:
- Finally, you will see the window, where you can see all the settings which will be reset to default:
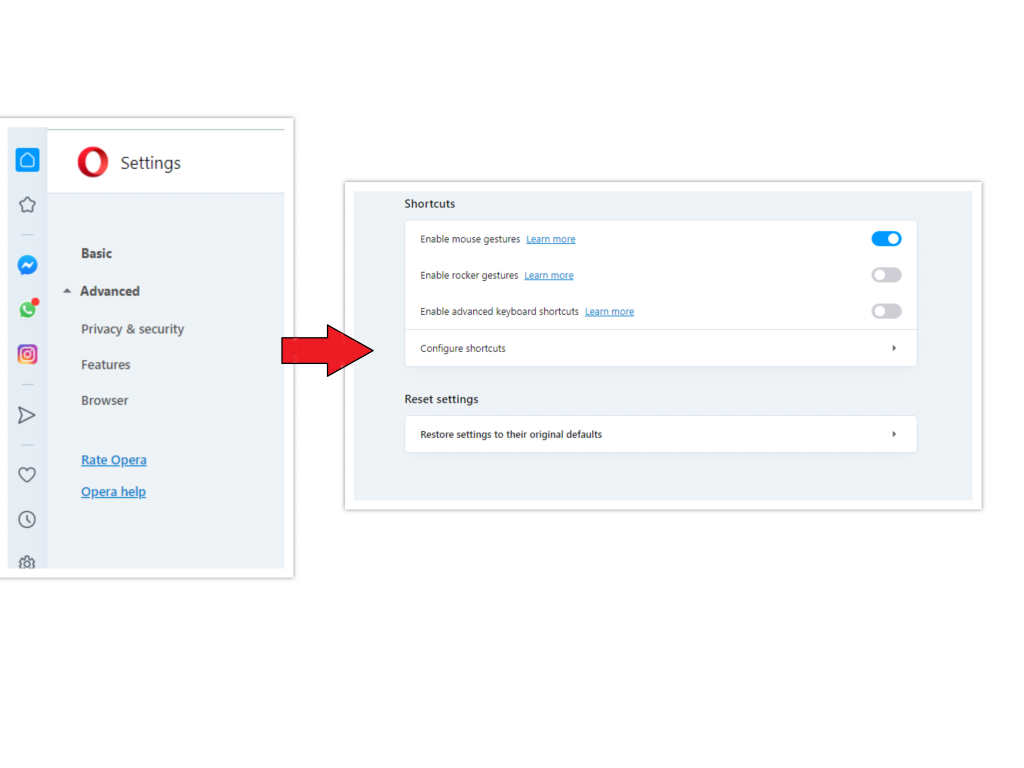
Opera can be reset in the next way
- Open Settings menu by pressing the gear icon in the toolbar (left side of the browser window), then click “Advanced” option, and choose “Browser” button in the drop-down list. Scroll down, to the bottom of the settings menu. Find there “Restore settings to their original defaults” option:
- After clicking the “Restore settings…” button, you will see the window, where all settings, which will be reset, are shown:
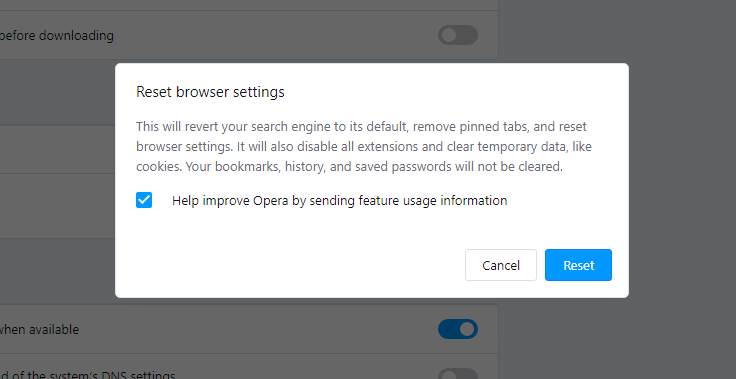
When the browsers are reset, you need to ensure that your browser will connect the right DNS while connecting to the web page you need. Create a text file titled “hosts” on your pc’s desktop, then open it and fill it with the following lines1:
# Copyright (c) 1993-2006 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handle within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
Find the hosts.txt file in C:/Windows/System32/drivers/etc directory. Rename this file to “hosts.old.txt” (to distinguish it from the new one), and then move the file you created on the desktop to this folder. Remove the hosts.old from this folder. Now you have your hosts file as good as new.
Scan your system for possible viruses
After removing the Appyrinceaskeda push notifications, it’s time to see if these pop-ups brought any threat to your system. Launch GridinSoft Anti-Malware, and then click on Standard scan. It will be enough in most cases to find and remove malware. The scan will last 5-10 minutes; you are free to use your system during that process.
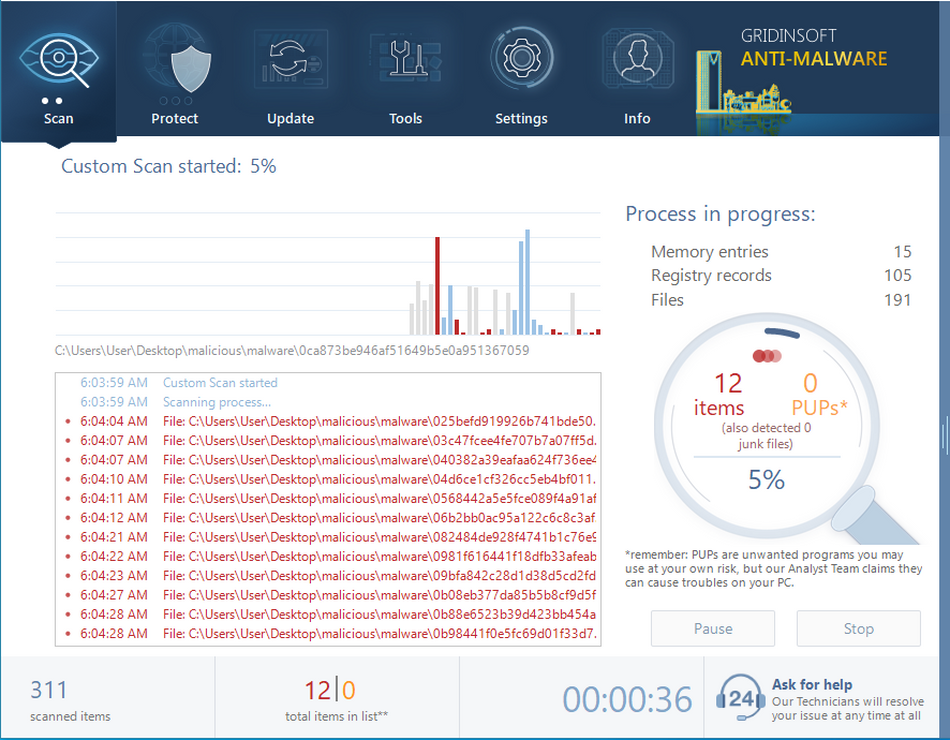
Once the scan is complete, you will see the detections or a notification about a clean system. Proceed with pressing the Clean Up button (or OK when nothing is detected).
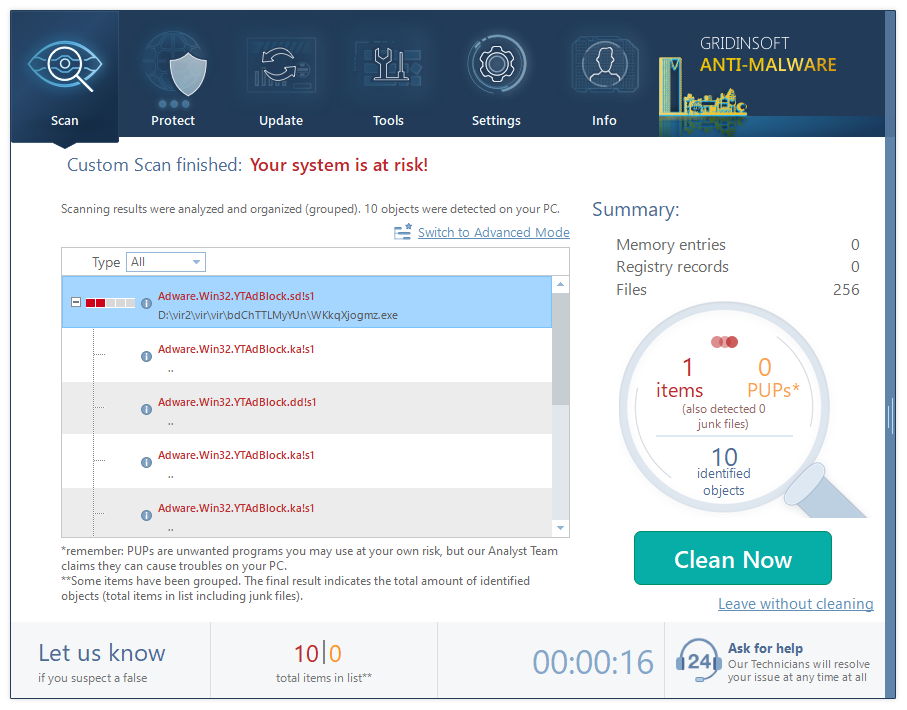
Appyrinceaskeda Removal Guide
Name: Appyrinceaskeda
Description: Appyrinceaskeda.com is a Command & Control (C&C) server that plays a crucial role in the distribution and management of VenomSoftX malware. This highly dangerous malware is a JavaScript-based remote access trojan that is primarily designed to steal cryptocurrencies and hijack them. The malware also carries out various other malicious activities such as fingerprinting the infected machine, capturing clipboard content, and executing additional payloads or commands.
Operating System: Windows
Application Category: Adware
User Review
( votes)References
- Official Microsoft guide for hosts file reset.

