AMTEmu is a well-known tool utilized for activating Adobe products, but it necessitates users to disable their antivirus software, rendering it susceptible to malware injection. Malicious actors can exploit this vulnerability and exploit AMTEmu as a carrier to distribute malware. This article examines the associated risks of using AMTEmu and how it can be misused for malicious intents.
What is AMTEmu?
As previously mentioned, AMTEmu is a widely used tool that allows users to activate Adobe products without the need for purchasing a license key. The activation process can be intricate, and performing it manually may be challenging. This is why such tools are highly sought after. In addition to its primary purpose of activating Adobe products, AMTEmu may also offer additional features or functions related to activation.
Most anti-malware software identifies AMTEmu as a hack tool or crack and takes automatic measures to block it upon detection. In order to use AMTEmu, users are typically required to either disable their antivirus software or whitelist the application. This introduces a vulnerability that can be exploited by malware distributors, allowing them to inject malware through the application. Consequently, the risk of infection through the utilization of AMTEmu is very high.
The main reason for the tool’s vulnerability is its core functionality. It connects to the Key Management Service and sends one of the leaked activation keys for OEM PC manufacturers, receiving an individual key for the device from the server and completing the activation process. However, changing AMTEmu’s configurations to connect to a server controlled by malware distributors is easy. After such manipulation, it becomes effortless to send back a pack of viruses instead of the individual key. If a user tries to activate the system multiple times, they may end up with new and new viruses.
There is also a much more clumsy but the same effective method. When downloading the AMTEmu, you don’t get the same program – there is an executable file of the trojan virus instead of the offered app. The problem is that the anti-malware program with working on-run protection will start notifying you about the malware presence (this time – about the trojan virus), so the user who has such a good security tool will stop at this point. Nonetheless, many people ignore this information and run the virus under the guise of the Adobe activation tool.
AMTEmu may also be dangerous in another way. Using the hacked Windows is a prosecuted action. And if the executive authorities detect such usage, you (or your corporation) will be fined a large sum of money. Keep this fact in mind if you have a cracked version of Windows on your home computer and are going to develop the program or to do any other activities which may uncover the fact of license hacking.
Which viruses may I get with the AMTEmu?
Generally, most viruses you may get through the AMTEmu and similar KMS-hacking apps are trojans of different categories. Usually, it is a trojan-downloader that will inject a lot of other viruses after getting launched, or Adrozek trojan, who has similar behavior with adware. A rare case is ransomware injection through the ransom-trojan – a specific type of trojan-downloader, which can make several system changes that make the ransomware activity much easier.
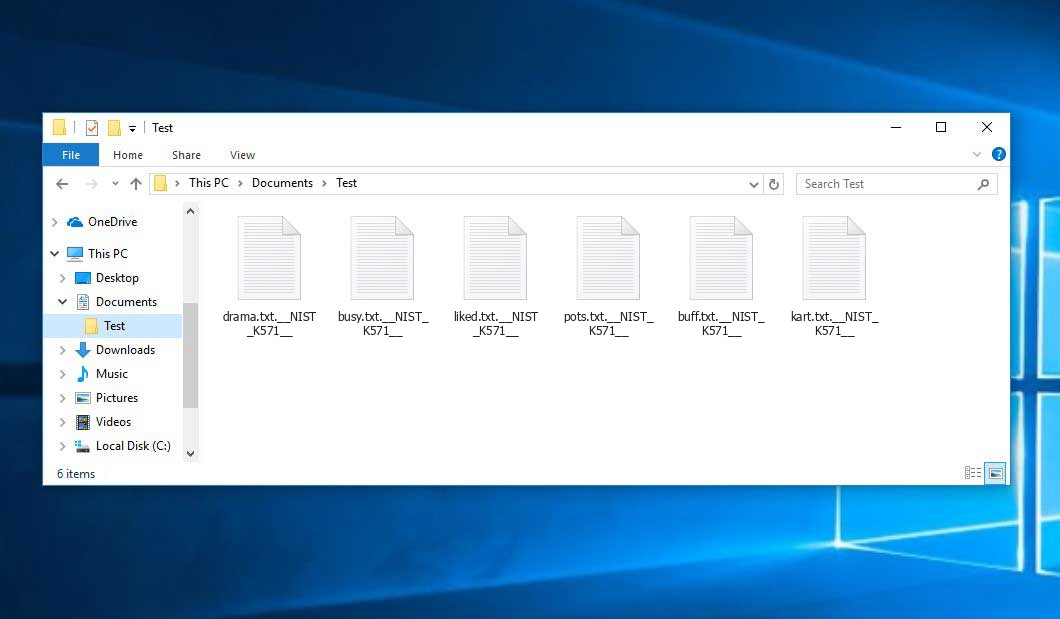
All of these viruses significantly influence the infected PC’s performance. And besides the usability harm, this malware may also damage your confidential data, especially when we talk about ransomware. It is recommended to remove this malware as soon as possible.
How can I understand that my version of AMTEmu was a counterfeit?
The sign of the false program is the absence of its efficiency. Check your PC with an antivirus program if it does not show the results it was promoted with. The correct functioning of the AMTEmu does not guarantee that there are no viruses onboard. However, if you are going to use such questionable programs, using anti-malware software must be like washing your hands during a pandemic.
If the malware from the AMTEmu-related bundle was successfully injected into your system, you will see the common symptoms typical for trojan virus activity. System slowdown, blinking windows on the desktop, and many unknown apps running in the background and launched as user processes are the clearest signs of trojan presence.
How to wipe the trojans out of my PC?
Manual trojan removal is likely impossible due to the wide range of changes implemented by this type of virus. It is better to use anti-malware software. But the Microsoft Defender1, that is present on each computer with Windows 11, has a lot of vulnerabilities, and may be easily disabled by the trojans via Group Policies editing. Moreover, a lot of users disable it manually due to the consumption of computer resources. Hence, it is not the most reliable solution.
GridinSoft Anti-Malware is a perfect solution for such a case. It has an On-Run Protection option, which allows it to detect & block the viruses before the start of their activity. And the perfect efficiency of its scans will surely help you to deal with the malware that is already present on your PC.
Install and launch GridinSoft Anti-Malware. Start the Full scan: it will check all logical disks in your system, so the malware will surely be found.
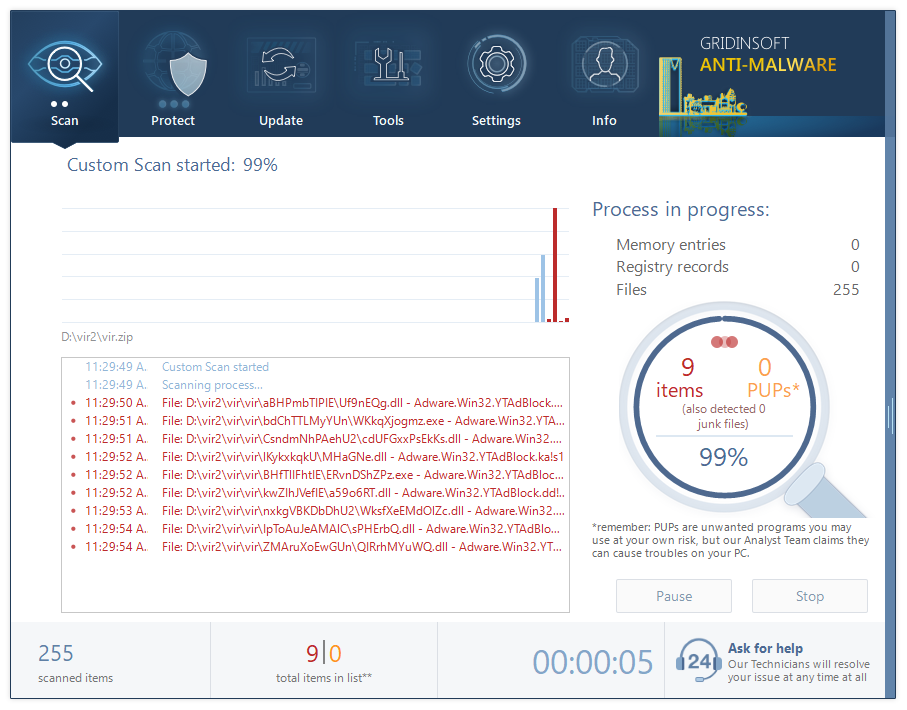
When the scan is over, press “Apply” to delete the detected malware.

User Review
( votes)References
- Perfect Defender comparison with one of the top-tier antimalware programs