Ad Avenger is a pseudo-adblocking plugin that appears in your browser spontaneously. It offers you the ability to cut the banners on the websites, but in fact, it just adds new ones. Because of its malicious nature, it can easily be used to spread additional viruses.
What is Ad Avenger?
It can be correctly described as an unwanted browser plugin. Such thighs appeared a long time ago, but their peak popularity happened in 2021. Usually, they contain the elements of browser hijacker, adware, or both simultaneously. In particular, Ad Avenger has strict elements of adware. It is promoted as an alternative to AdBlock – one of the most popular extensions for Chrome.
Instead of blocking advertisements, it causes their more massive appearance. But the additional banners on all websites you visit is not the only effect. Ad Avenger also opens additional pages which contain various ads, generally – the promotions of rogue software, unwanted applications or other malicious plugins. This sort of annoying behavior makes the browsing process pretty unpleasant.
How did I get the Ad Avenger plugin?
Ad Avenger is usually promoted on the redirect web pages. That looks like an additional page that is opened just after your click on the link. On that page, you are lured to press the Download button with different and controversial offers. One of the most widely met site says “Browser update” at its tab header, but also says “Recommended plugin for your browser” on the site body. So update or recommendation?
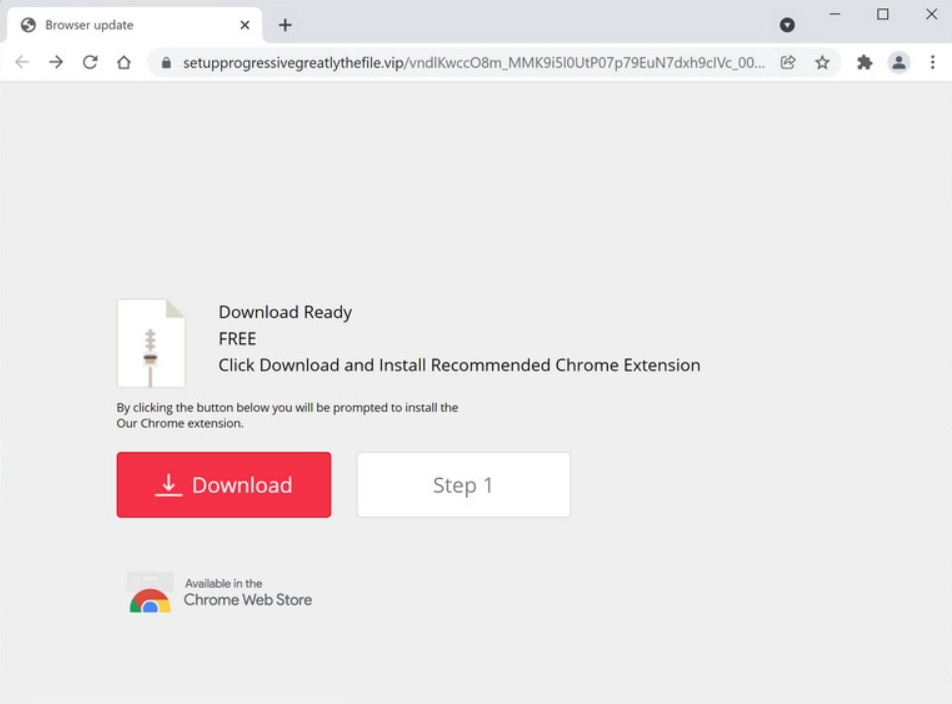
The page which offers to install Ad Avenger
Some adware (and adware plugins) may cause the appearance of that page. If adware is a separate program, it may easily install it without your permission – just because it has already got this permission when you have installed it. But luckily, such cases are pretty rare. Ad Avenger spreading is more about inattentive and reckless behaviour. But that does not make it less dangerous.
What is the danger of malicious plugins?
Just like adware or browser hijackers they usually play the role of, unwanted browser plugins showing you a lot of annoying ads. These banners are filled with pretty dubious content – offers to buy a thing you don’t need, ads of pornographic websites, or banners of betting companies. But all of these things are just baby talk compared to the scam pages it can show to you.
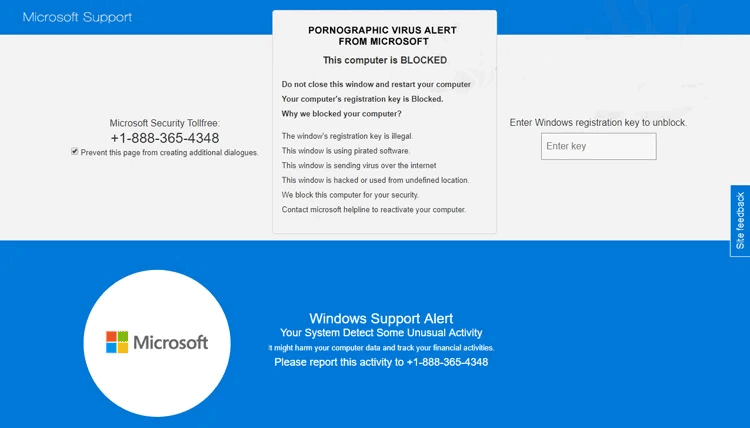
Microsoft Pornographic virus alert – the example of scam shown by Ad Avenger
In particular, Ad Avenger reportedly displays various support scam pages as well as pseudo-giveaways. Microsoft Pornographic virus alert and Amazon $1000 gift card scam are just among them. For the experienced user, such banners usually call nothing but a laugh, but low-skilled people may easily be involved in a scam. Losing the credentials from your banking account, installing rogue software or even spyware – the risks are pretty high. It is not about recommendation – it is essential to remove it as soon as possible.
How to remove the Ad Avenger plugin?
Luckily, Ad Avenger, just like any other browser plugin, can be deleted from the Chrome settings tab. There are two problems with such an easy removal method. First one is that you need to fix the changes in browser configurations this thing did. That is pretty easy to solve: just reset your browser settings, and you are good to go. The second is more serious: possibly, Ad Avenger appearance is related to the activity of adware, which is present on your PC. Thus, it is essential to check your PC for possible other threats.
For this purpose, I will recommend you GridinSoft Anti-Malware. It is a perfect anti-malware solution that is capable of removing any kind of viruses. Even the freshest malware is not a problem – it gets database updates each hour, so malware will not pass. Moreover, it does not have such vulnerabilities as Microsoft Defender does. That makes GridinSoft Anti-Malware perfect for cleaning compromised systems.
Removing the viruses with GridinSoft Anti-Malware
To detect and eliminate all malicious programs on your PC with GridinSoft Anti-Malware, it’s better to use Standard or Full scan. Quick Scan is not able to find all the malware, because it scans only the most popular registry entries and folders.
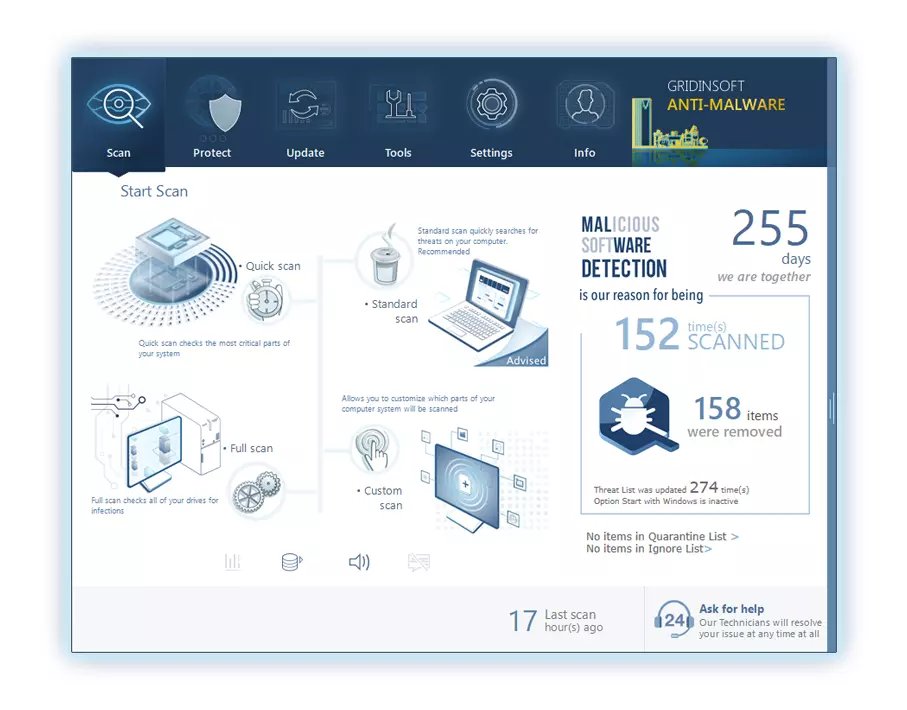
You can observe the detected malicious apps sorted by their possible harm during the scan process. But to choose any actions against malicious programs, you need to hold on until the scan is over, or to stop the scan.
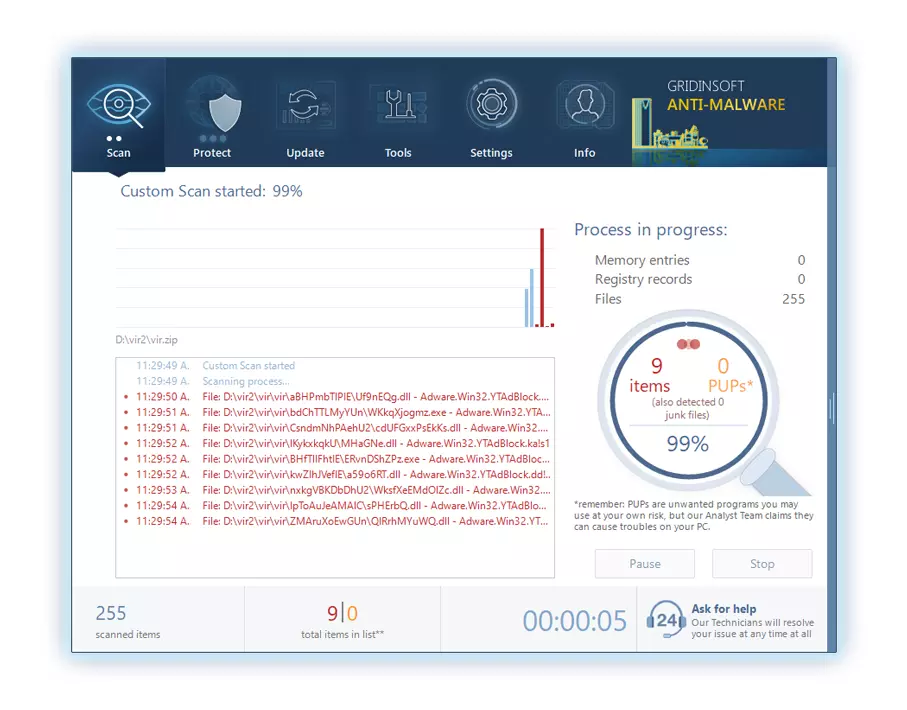
To set the action for each spotted malicious or unwanted program, click the arrow in front of the name of the detected malicious app. By default, all malware will be removed to quarantine.
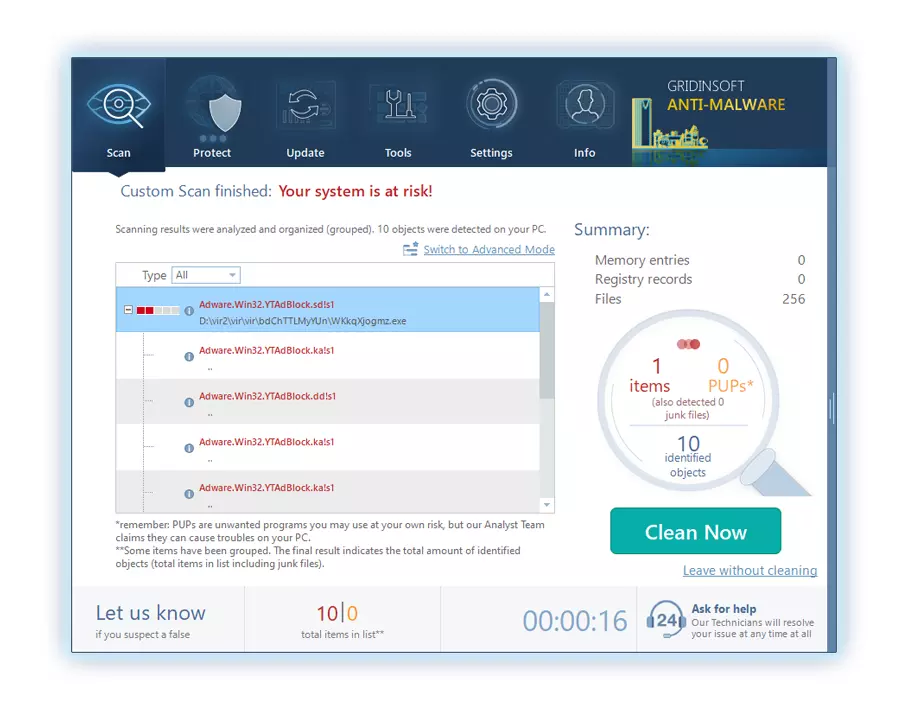
Reverting browser settings to original ones
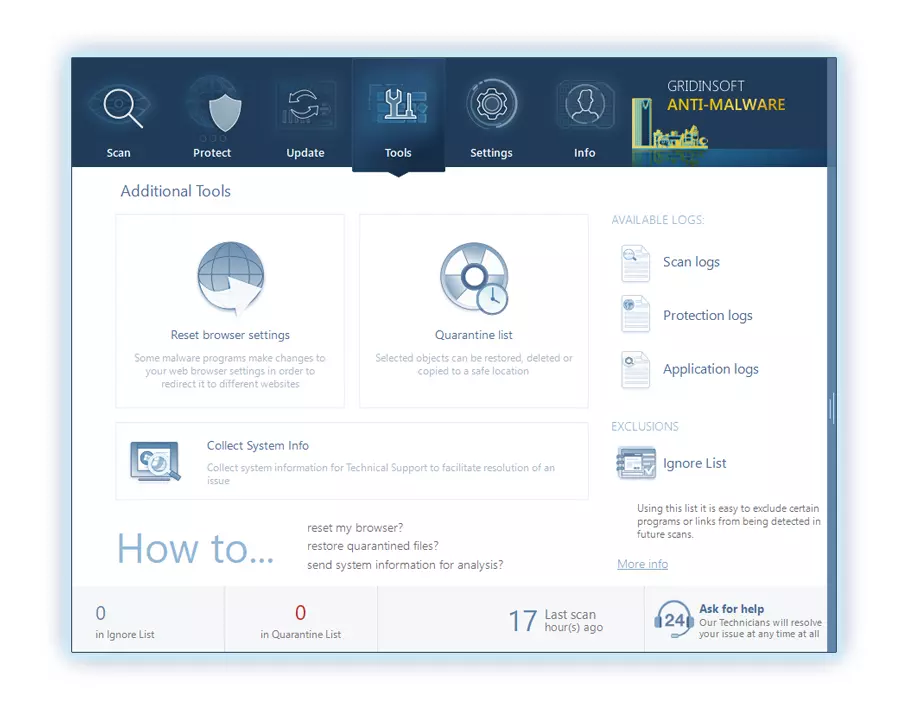
To revert your browser settings, you need to use the Reset Browser Settings option. This action cannot be intercepted by any malware, hence, you will surely see the result. This option can be found in the Tools tab.
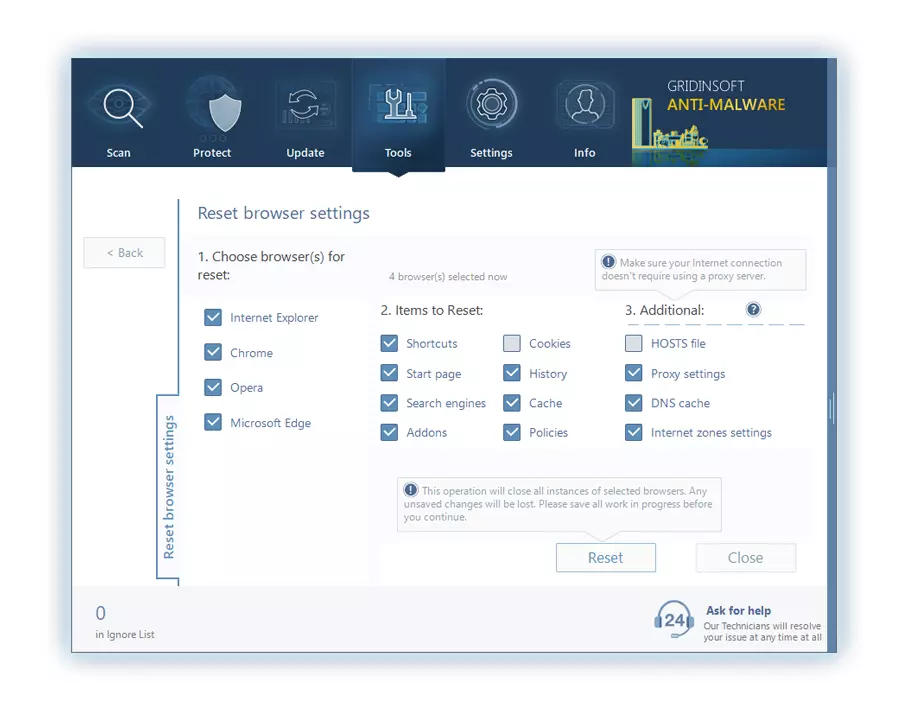
After choosing the Reset Browser Settings button, the menu will be displayed, where you can choose, which settings will be reverted to the original.
User Review
( votes)





