Y2meta is a website that promotes itself as a page where you can download any video from YouTube. Besides the fact that the action this site offers is illegal, it also has been reported for malware spreading and some other malicious activity.
What’s wrong with the Y2meta site?
I couldn’t say that Y2meta is a malicious website. The ability to download videos from YouTube is sometimes needed, but it is absent on the exact service. Y2meta is not a single example of a website that allows you to get videos from YouTube. Y2mate is another page that offers the same functions. Besides the fact that the sites’ functions are illegal, there is also a risk of getting infected with different malicious items.
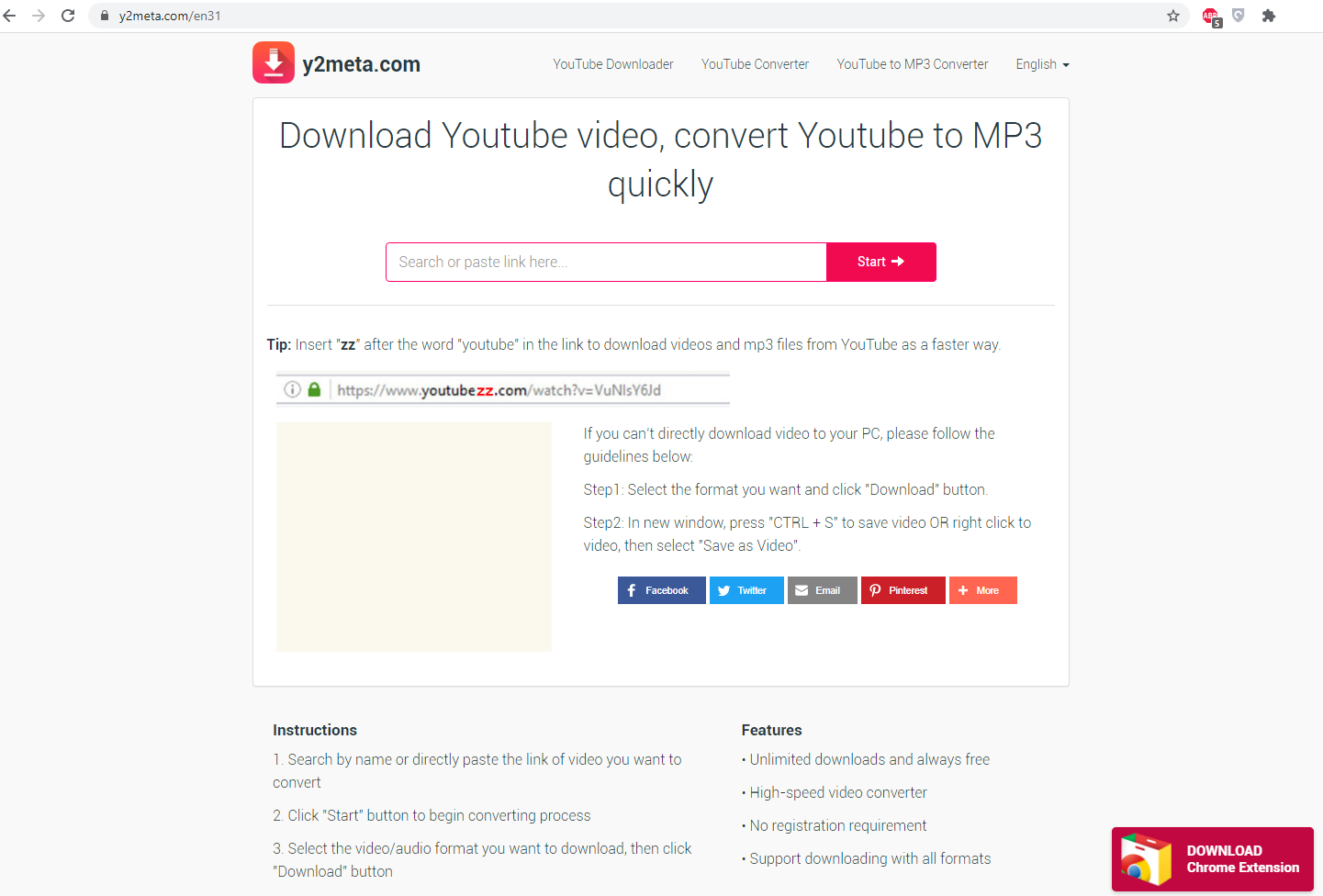
First of all, let’s figure out what is illegal about the Y2meta site. As you likely know, copyright policies are spread everywhere nowadays. Even YouTube, which was created as a video hosting, is full of licensed content nowadays. If you play the music video with the contents that are under copyright, your video will be at least demonetized. The worst thing that may happen is an account ban. And you have not even downloaded this song from the site. If the executive authorities examine your PC for some reason and find the licensed video you have downloaded from YouTube, you will likely be charged with a huge fine. Or even imprisoned – in the case when you have a lot of illegally copied content on your disk.
Is Y2meta malicious?
Y2meta site holds pretty big traffic. To deal with all this traffic, its maintainers must take on a lease a pretty big server. Another way to solve this problem is to establish their own server. Whatever they choose, they need a lot of money for server maintenance. Ads on their page are likely not enough to pay for the server (or electricity bills) and have something for themselves. Thus, boys are likely getting money in other ways, and the answer hides exactly in the ads they show to you.
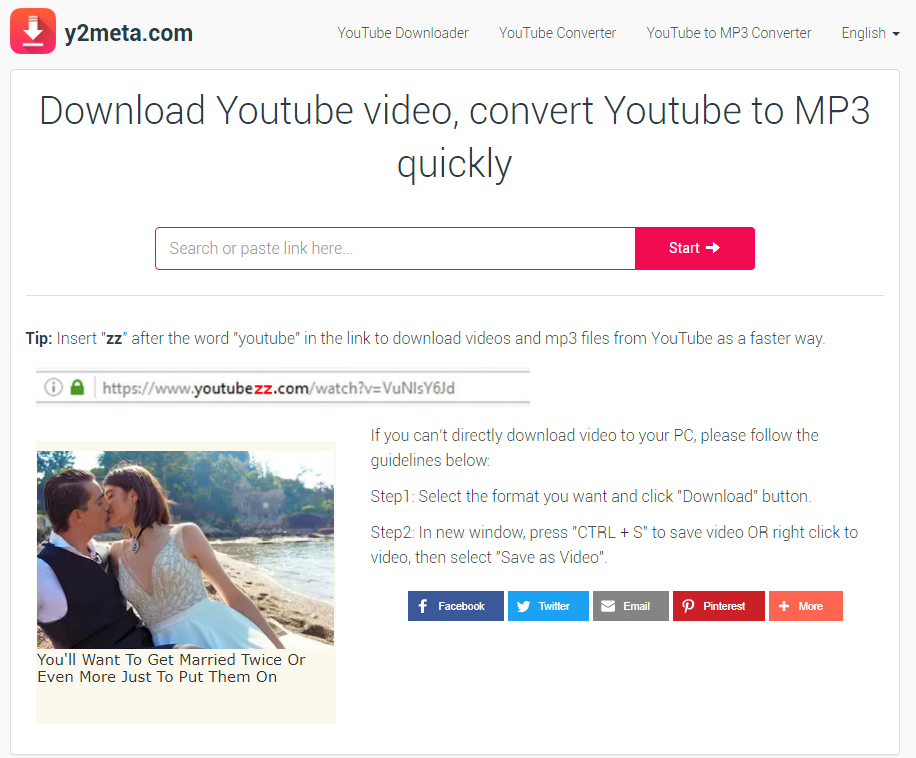
Here is how this site looks without the AdBlocker plugin. You can see that there is only a single banner on this page. But how can they earn money by showing only one ad per user? Even if this advertisement was a pay-per-install, it is not enough to cover the aforementioned spendings. That’s why I suppose the malware-related earning ways.
There are three ways this site can provide malware to its users. Those are pop-up notifications, the exact banner you can see in the middle of the window, and the browser plugin it offers you to install. Of course, no one forces you to do this, but if Y2meta is still running without any shutdowns and donation offers. Suspicious situation, isn’t it?
How can browser plugins and pop-ups be dangerous?
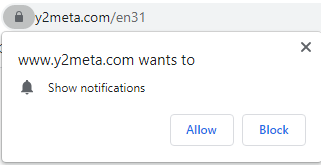
Offer to enable pop-ups from Y2meta site
Pop-up notifications are a perfect advertising tool. They show the user interested in some news the most actual updates on the website they read. However, since there is no limit for pop-up messages from one website for a certain period of time, pages like Y2meta can easily commit a pop-up storm in your browser. And, exactly, that’s how they will earn their penny – each of the banners you see inside the pop-ups from Y2meta is paid through a pay-per-view scheme. It is also pretty easy to predict what you will see on these ads – some unacceptable ads or even malvertising. The last thing can easily deliver adware or unwanted programs to your system.
Browser plugins are also beneficial things that allow you to modify the browser for your needs. But crooks found a way to make money even there. The plugin Y2meta offers you to install modifies your starting page and can alter any page you are opening. Developers state that this plugin will change only YouTube, adding the download button to each video. Nonetheless, the Y2meta plugin can still modify any other page – and add advertisements on them, for example.
What do I need to do?
I recommend you avoid using this site. Sure, it may be needed sometimes, but try to check other possible sources when you need to get something from YouTube. It is better to use something not so risky – for example, contacting the content maker. Y2meta is about to be the last – and the riskiest option. There is no safe malware, so risking getting infected while using this site is a bad choice.
If you have already used this page and are not sure if your computer is clean of malware now, it is better to check your computer with an antivirus program. This step is especially needed when you have applied the pop-ups or browser plugin (or even both) from the Y2meta site. GridinSoft Anti-Malware will be the best choice: it is capable of both system cleanup and resetting your browsers to default. The last step is highly recommended after using the mentioned plugin or pop-ups.
Scanning the system with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. Press “Apply” to finish the malware removal.



Now, when the computer is clean of viruses, we can proceed to the browser reset. You can do this step manually, as well as with the use of GridinSoft Anti-Malware.
Reset browser settings to default
Manual method of browser reset
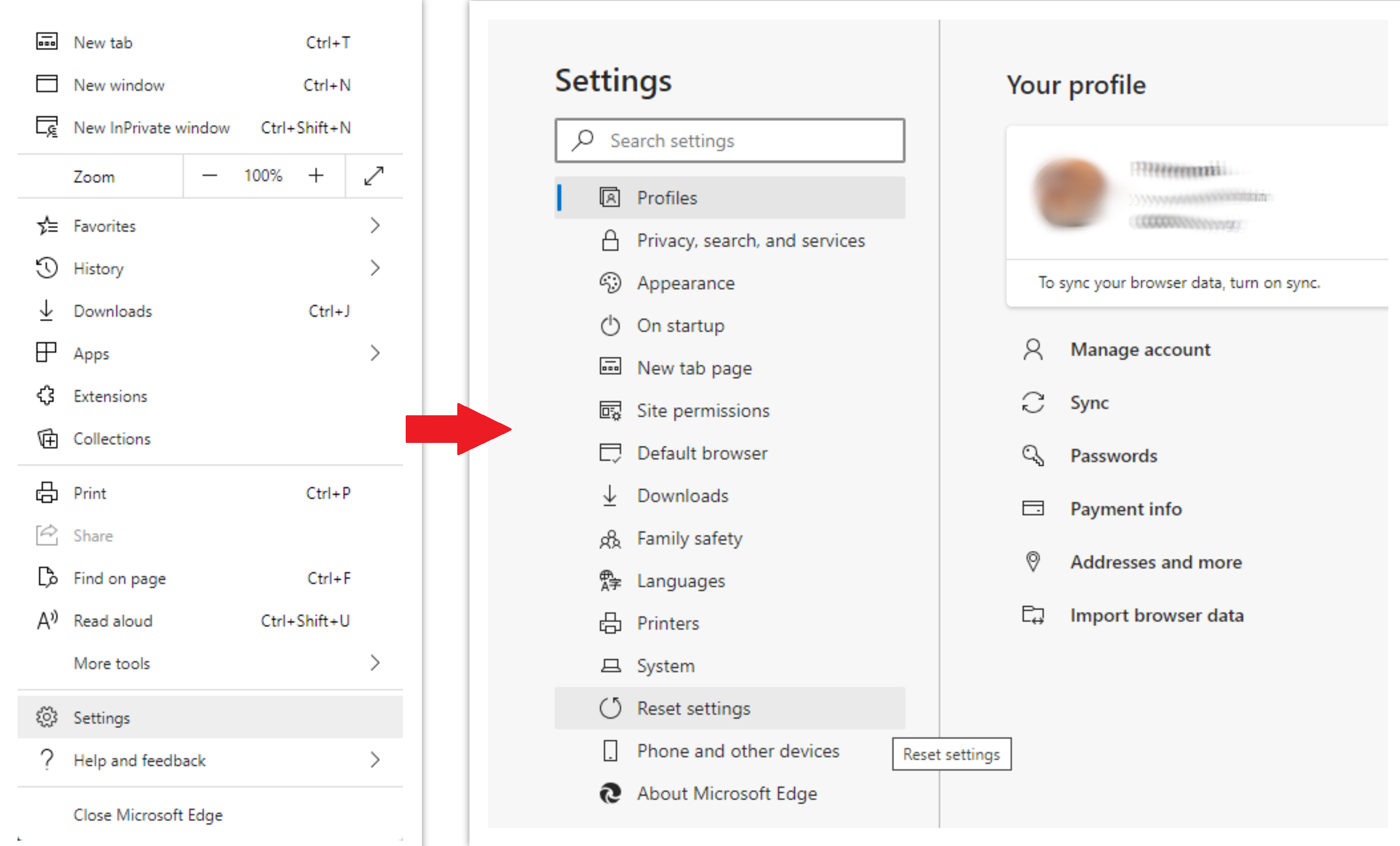
To reset Edge, do the following steps :
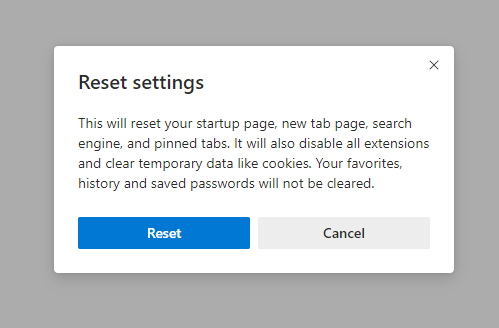
- Open “Settings and more” tab in upper right corner, then find here “Settings” button. In the appeared menu, choose “Reset settings” option :
- After picking the Reset Settings option, you will see the following menu, stating about the settings which will be reverted to original :
For Mozilla Firefox, do the next actions :
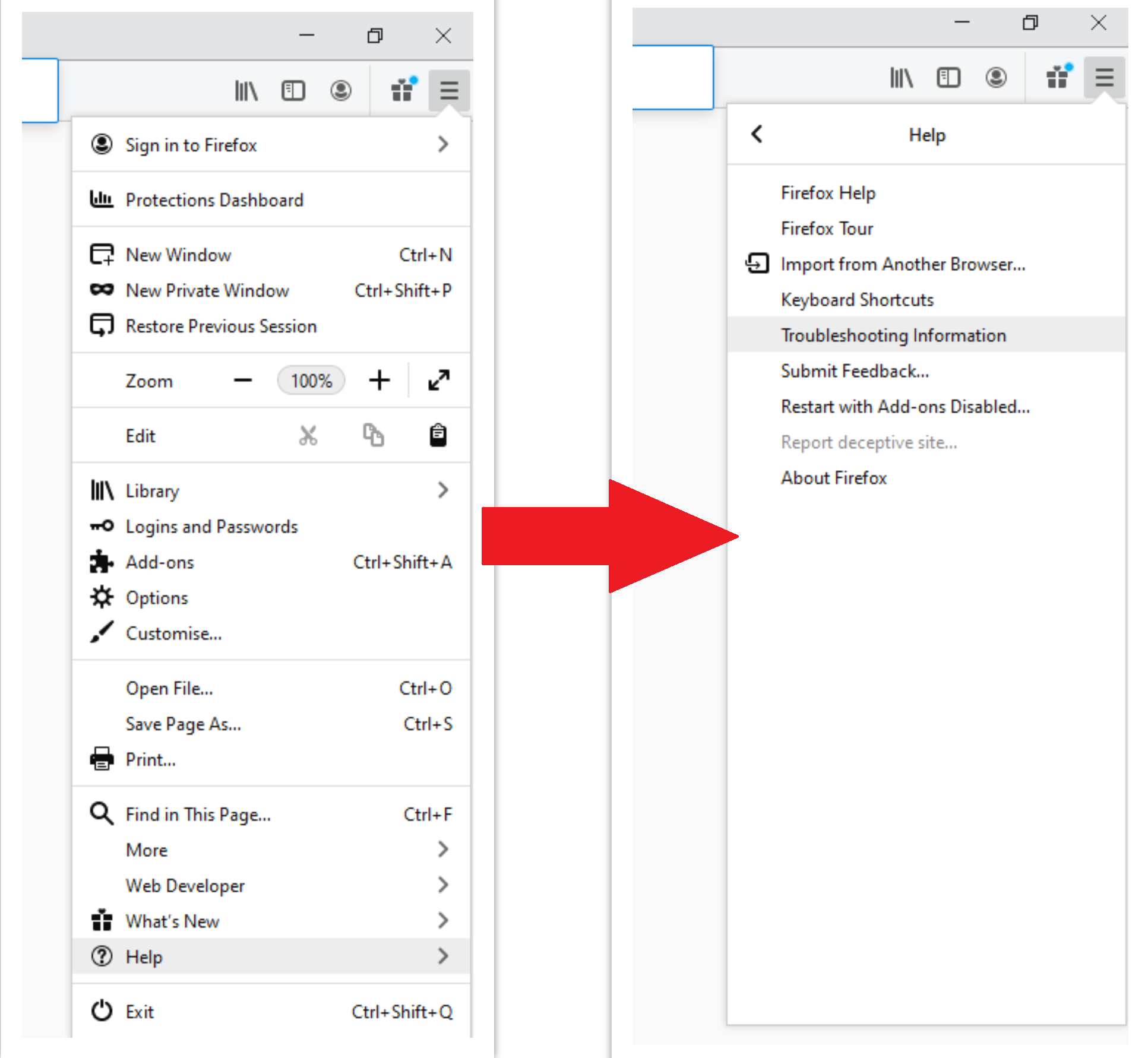
- Open Menu tab (three strips in upper right corner) and click the “Help” button. In the appeared menu choose “troubleshooting information” :
- In the next screen, find the “Refresh Firefox” option :
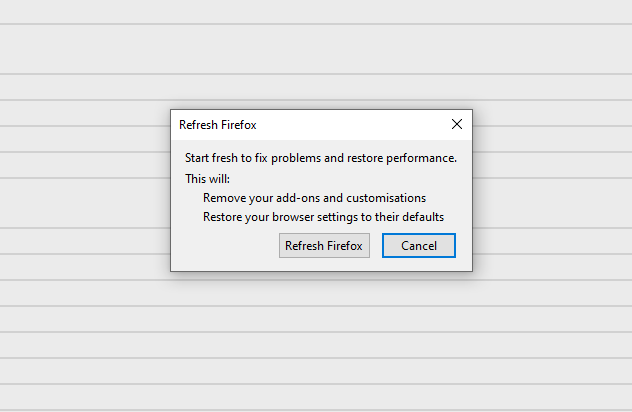
After choosing this option, you will see the next message :
If you use Google Chrome
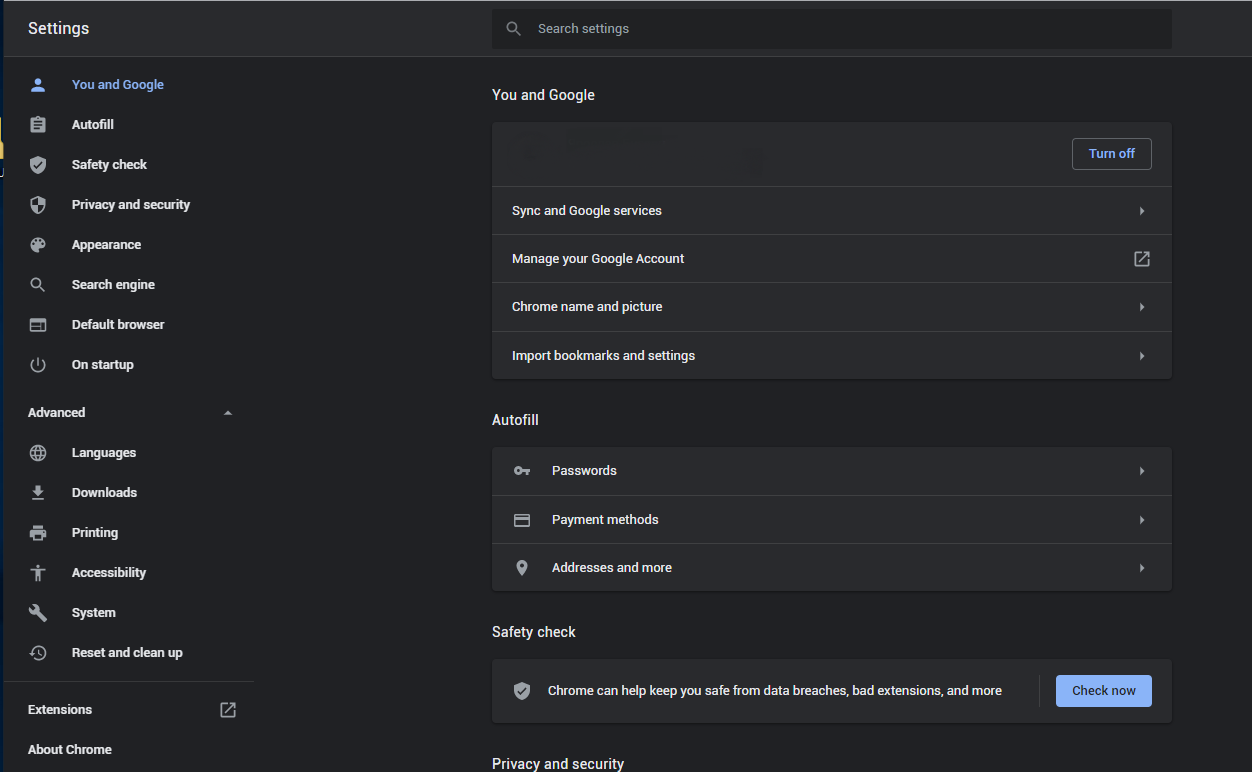
- Open Settings tab, find the “Advanced” button. In the extended tab choose the “Reset and clean up” button :
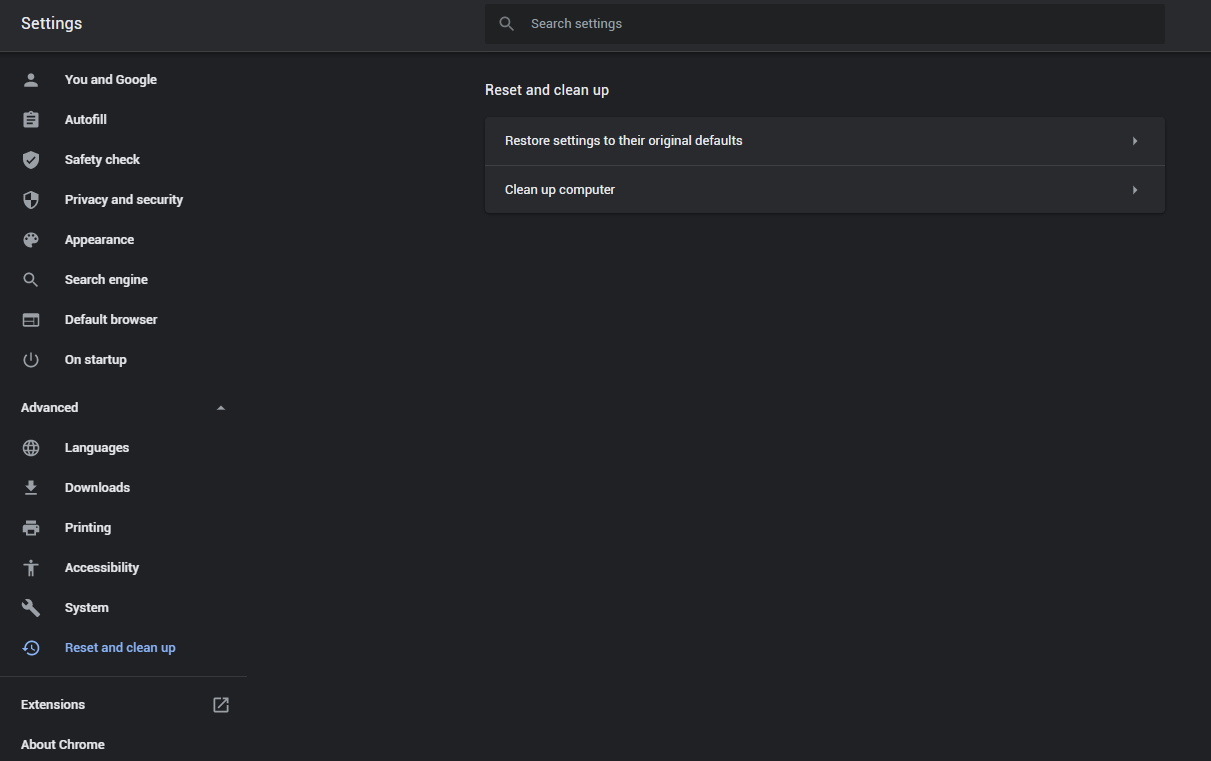
- In the appeared list, click on the “Restore settings to their original defaults” :
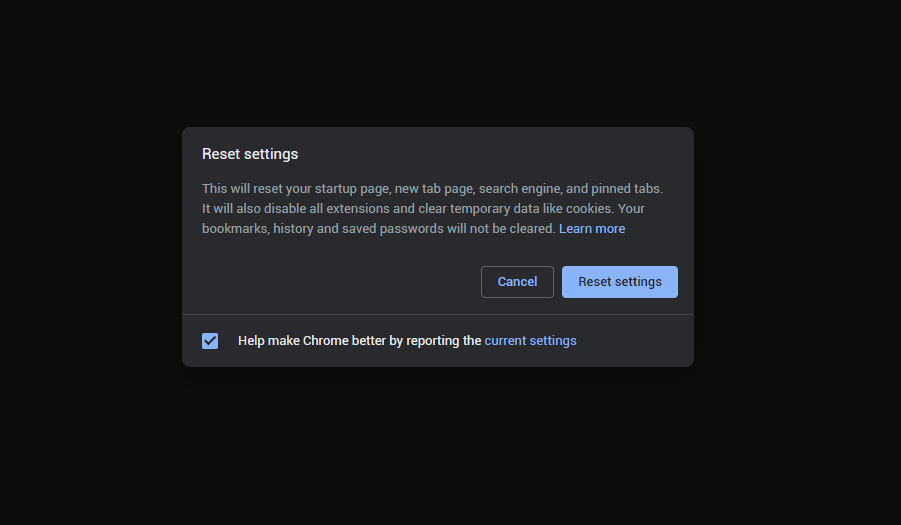
- Finally, you will see the window, where you can see all the settings which will be reset to default :
Opera can be reset in the next way
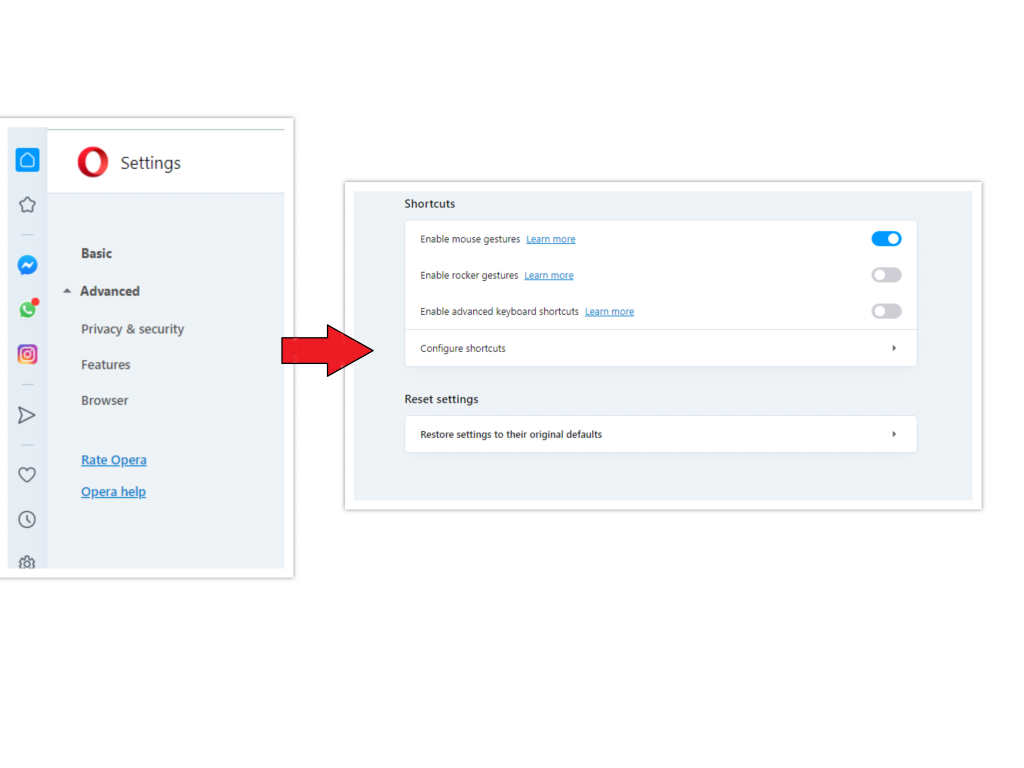
- Open Settings menu by pressing the gear icon in the toolbar (left side of the browser window), then click “Advanced” option, and choose “Browser” button in the drop-down list. Scroll down, to the bottom of the settings menu. Find there “Restore settings to their original defaults” option :
- After clicking the “Restore settings…” button, you will see the window, where all settings, which will be reset, are shown :
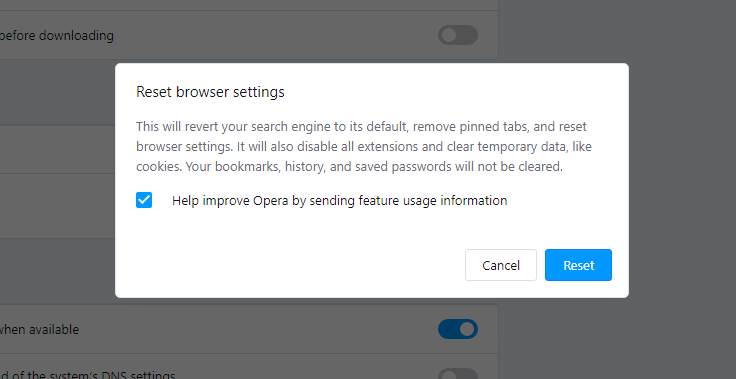
Reset your browser settings with GridinSoft Anti-Malware
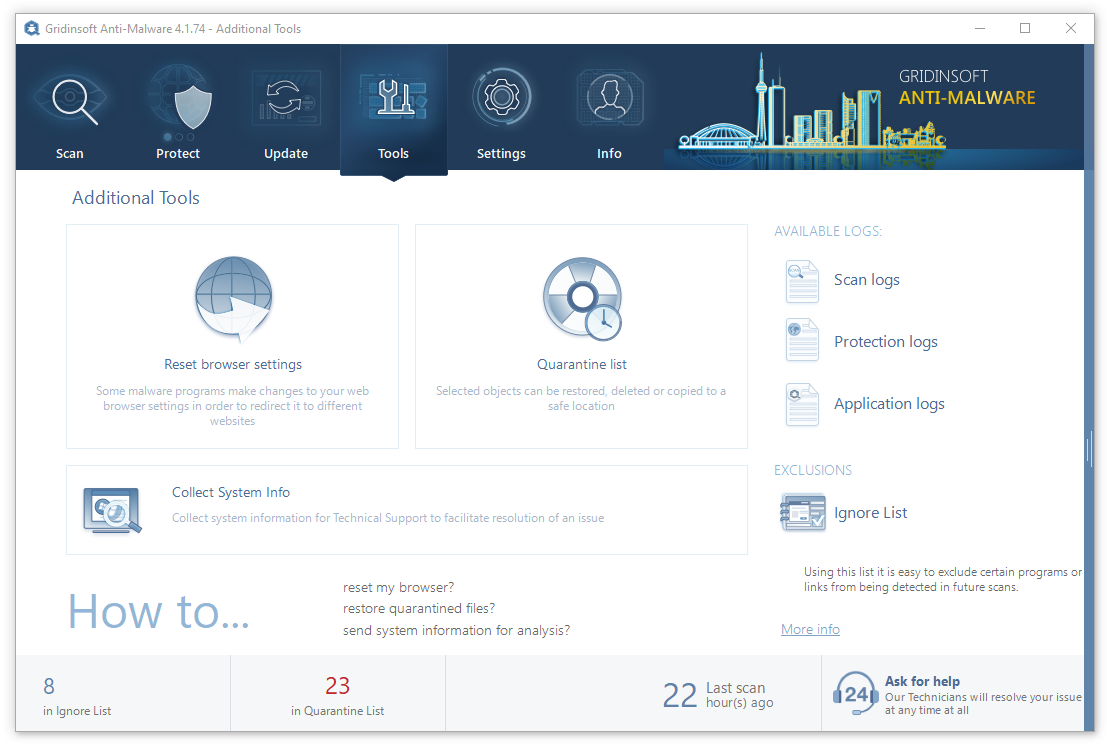
To reset your browser with GridinSoft Anti-Malware, open the Tools tab, and click the “Reset browser settings” button.
You can see the list of the options for each browser. By default, they are set up in a manner that fits the majority of users. Press the “Reset” button (lower right corner). In a minute, your browser will be as good as new.
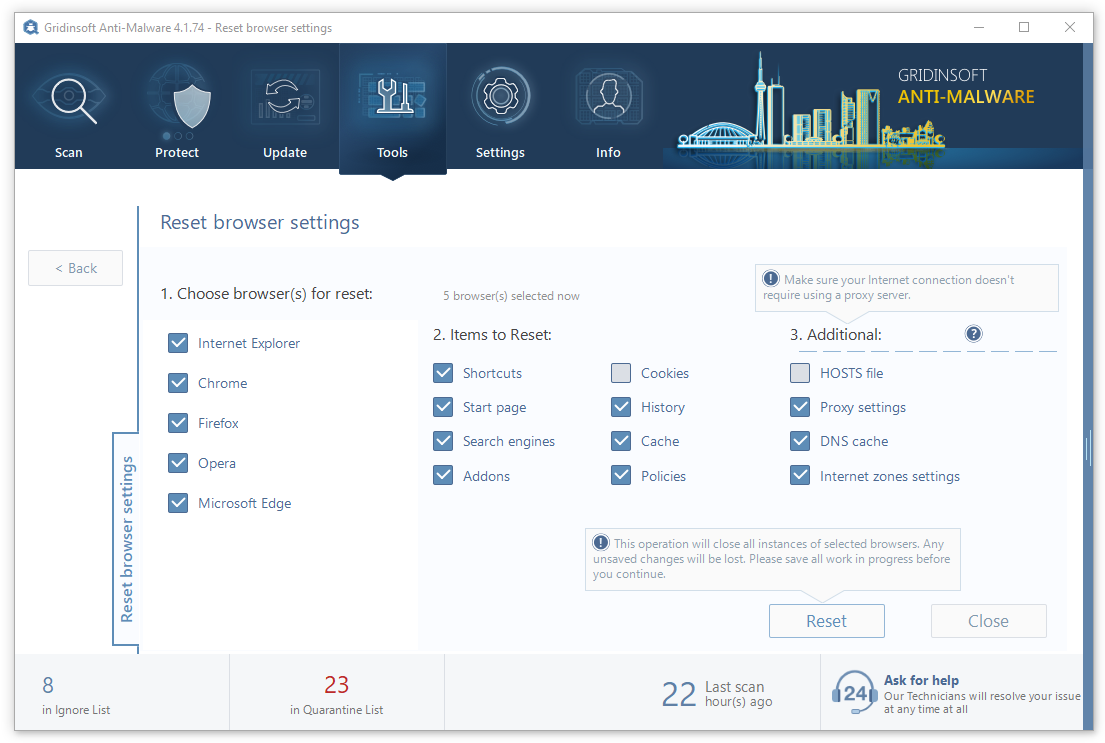
The browser reset is recommended to perform through the antivirus tool by GridinSoft because last can also reset the HOSTS file without any additional commands.
User Review
( votes)

