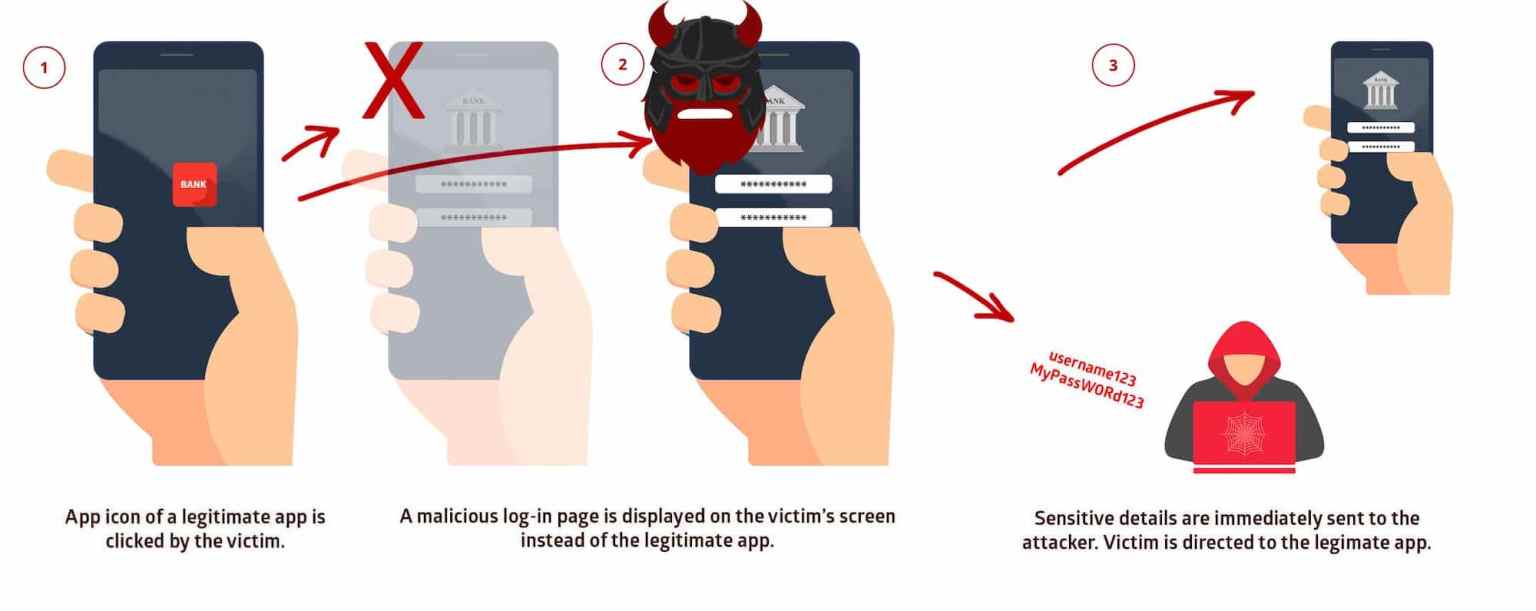
At the end of 2019, Promon’s information security experts reported about StrandHogg vulnerability in Android, which allows malicious applications to modify legitimate ones and perform malicious operations on their behalf. Now there is a modification of StrandHogg 2.0, which allows the malware to mask itself as other Android applications.
The bug is called StrandHogg and, in fact, it can trick the user into granting dangerous privileges to a malicious application, even during the interaction with the legitimate application. Additionally, the problem can be used to show victims fake login pages while connecting to legitimate applications.The root of the problem is that in Android activities have the taskAffinity flag. It allows to specify the name of the task, on the activity stack of which will get the specified application. This is needed for better control over reverse stacks. However, by default, the value of taskAffinity is equal to the name of the application package, which means that in some cases you can quietly push the activity of your application into the activity stack of someone else’s. And if you specify the flag allowTaskReparenting = “true”, this activity can be moved to the very top and the next time you click on the icon of the target application, it will appear on the screen first (that is, it will be on top of the stack)”, – experts explained StrandHogg essence.
For exploitation of the problem should be running both the malicious application and the victim application. The sequence of user actions should be the following: he launches the victim application, returns to the desktop, then launches the malicious application, then starts the victim application again. At this point, instead of a cold start, Android simply shows the “top” activity on the stack, and it turns out the activity of the malicious application.
Let me remind you that Google engineers refused to fix this vulnerability last year and refused to do it years earlier. The fact is that this is called design flaw, a design error, correction of which will break the existing software. In fact, Google chose to focus on detecting and blocking malicious applications that exploit the vulnerability, rather than releasing a patch.
Now the experts of the same company Promon have published information about the second version of the problem, calling the vulnerability StrandHogg 2.0 (CVE-2020-0096) and saying that it is much worse than the first.
The new version of the vulnerability works in a similar way: it makes the victim believe that he enters his credentials in a legitimate application, while in reality the victim interacts with the malicious overlay”, — say Promon researchers.
Additionally, Strandhogg 2.0 does not require any permissions to work, but can be used to obtain various permissions through other applications (for the subsequent theft of confidential user data, such as contacts, photos, location information).
Researchers write that the main weakness of the first Strandhogg was the need to declare taskAffinity in Android Manifest. Since the manifest is a regular XML file and must be included in a package hosted by the Google Play Store, it cannot simply be downloaded later, after installing the application. As a result, scanning the official application directory in search for applications with a suspicious taskAffinity was quite simple, and Google widely practiced it.
However, unlike its predecessor, the StrandHogg 2.0 problem does not require any special settings in Android Manifest and the use of taskAffinity. That is, the malicious code does not have to be present on Google Play, instead, the attacker can download it later when the dangerous application is already installed on the user’s device.
Strandhogg 2.0 poses a threat to most versions of Android (up to 9), so, approximately 90% of the entire Android user base is at risk, and we are talking about more than a billion devices”, – write Promon specialists.
This time, Google engineers finally released a patch to fix the vulnerability: the fix was included in the May updates for Android. Promon and Google experts write that they have no information that hackers have already exploited this problem. However, researchers that discovered the problem say that the operation of Strandhogg 2.0 is difficult to notice.