The DeathRansom ransomware, once considered simply a hoax, stopped joking and became a real threat, according to a recent Fortinet study. DeathRansom now really encrypts files.
The spread of DeathRansom occurred because of a massive information campaign that affected several people daily.The first DeathRansom infections were recorded in November 2019. However, IS community did not take it seriously. At that time, DeathRansom simply mimicked the actions of ransomware, and did not actually encrypt user files.
The first versions of DeathRansom added their extension to all the user’s files and placed a ransom letter on the computer to request money. Nevertheless, it was only an attempt to deceive a user, designed to make him panic. It was enough to remove the second extension in the file name to restore access”, – reports Fortinet.
However, we already wrote about how to painlessly get rid of the earlier versions of DeathRansom.
Apparently, the work on the code continued, and new versions of DeathRansom can now boast having the functionality of a real ransomware.
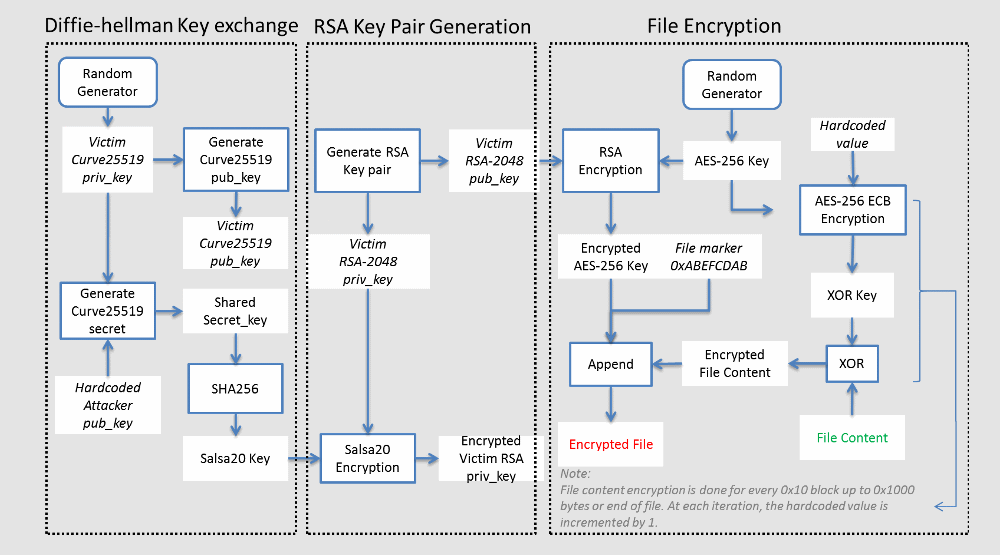
According to Fortinet, the new DeathRansom version use a complex combination of the Curve25519 algorithm for the Diffie-Hellman key exchange scheme, with an elliptic curve (ECDH), Salsa20, RSA-2048, AES-256 ECB and a simple XOR block encryption algorithm.
Security researchers are still examining the DeathRansom encryption scheme for implementation errors, but it can already be argued that this scheme is quite reliable.
However, Fortinet’s investigation of the DeathRansom was not limited to analyzing the source code of this new malware. Researchers also searched for clues about the source and author of the ransomware.
By analyzing the lines of the DeathRansom source code and the websites distributing it as a payload, the Fortinet team was able successfully associate the DeathRansom ransomware with the malware operator, which is responsible for a wide range of cybercrime campaigns.
According to Fortinet, before the creation and distribution of DeathRansom, this malware operator has participated in several campaigns that infected users with password stealers (Vidar, Azorult, Evrial, 1ms0rryStealer) and cryptocurrency miners (SupremeMiner).
The author of DeathRansom most likely spent several years spreading malware, extracting usernames and passwords from their browsers and selling stolen login information online.
This activity left a significant digital mark, which traced Fortinet analysts. The operator DeathRansom is known under the pseudonyms scat01 and SoftEgorka, the email address is vitasa01(@)yandex.ru, it has several phone numbers in Russia and the website gameshack(.)Ru (which, apparently, belongs to the author of DeathRansom).
Using this data, the researchers went to profiles on Yandex.Market, YouTube, Skype, UK, Instragram and Facebook, which are associated with a young hacker, named Yegor Nedugov, who lives in the small and depressed town of Aksay, near Rostov-on-Don.
Messages on hacker forums show that Nedugov, acting under the username Scat01, published malware reviews that he used, such as Vidar, Evrial and SupremeMiner.
The Fortinet report provides an overview of all the Nedugov accounts on the Internet and the obvious connections between them.
We’re sure we found the right person for DeathRansom. There is even more data, digital tracks and profiles that indicate this particular person, however, we decided not to include it all in the report”, – Fortinet researchers write.
Moreover, the author of DeathRansom also apparently violated one of the unwritten rules of the underground cybercrime scene, “no phishing and fraud with his forum colleagues.”
That’s why almost all of his accounts on underground forums were ultimately blocked”, — Fortinet wrote.
DeathRansom is currently distributed through phishing email campaigns. The Fortinet report contains trade-offs that companies can include in their security products and prevent business systems from being infected.
The company also said that they continue to analyze the ransomware coding scheme for possible errors that they hope to use to create a free decryptor to help former victims. Although still it is not worth hoping for this and it is better to remember the rules of information hygiene.