The developers of the stalker app LetMeSpy reported that hackers stole data from their product that was intercepted on target devices.
That is, victims of spyware were doubly unlucky: not only someone was following them, but also the messages collected by LetMeSpy, call logs and location histories were made public.
You might be interested in: How to Find Stalkerware on Your Smartphone? Or for example: Spyware vs. Stalkerware: What’s the difference?
Hack LetMeSpy
LetMeSpy is a classic Android stalkerware that is advertised as a parental control or employee monitoring tool.
Sometimes such products are even sold under the guise of remote access solutions designed for the corporate sector. But most often, such software is used to secretly monitor people without their consent, including the initiators of domestic violence, and therefore it often carries serious risks for those on whose devices it is installed.
Like other similar software, LetMeSpy is specially designed to remain hidden on the home screen of the phone, and it is difficult to detect and remove it. Once installed on a device, LetMeSpy automatically transfers all text messages, call logs, and precise location data of the victim to its servers, allowing the person who installed the app on someone else’s device to track their target in real time.
The author of the Polish research blog Niebezpiecznik was the first to notice the LetMeSpy hack. When he tried to contact the spyware maker, the response instead came from a hacker who claimed to have gained wide access to the LetMeSpy developers’ systems.
Who exactly was behind the LetMeSpy hack is unclear, and the motives of the hackers also remain unknown. Although the hacker told the researcher that he had deleted the LetMeSpy database stored on the server, the same day a dump with compromised data appeared on the network.
The leaked database was obtained by the activists of the DDoSecrets (Distributed Denial of Secrets) group, who position themselves as “fighters for transparency” and index data leaks in the public interest, and they shared the dump with TechCrunch. At the same time, DDoSecrets emphasized that they limit the spread of this leak, providing access only to journalists and researchers.
According to journalists, the dump contains call logs and text messages of victims dating back to 2013. The database contains records of at least 13,000 compromised devices, although some of them transmitted almost no data (LetMeSpy claims to delete data after two months of account inactivity). At the same time, among more than 16,000 SMS messages, not only personal correspondence of the victims, but also numerous messages with passwords and codes from various services were found.
Let me remind you that we also wrote that During quarantine, stalkerware usage increased by 51%.
In January 2023, the official LetMeSpy website reported that spyware was used to track over 236,000 devices and collected tens of millions of call logs, text messages, and location data. Now the counters on the site have been reset to zero, and most of the functionality (including the stalker app itself) does not work.
Journalists say that more than 13,400 geolocation points associated with several thousand victims were found in the leaked database. Based on this information, the majority of those affected by LetMeSpy are in the US, India, and West Africa.
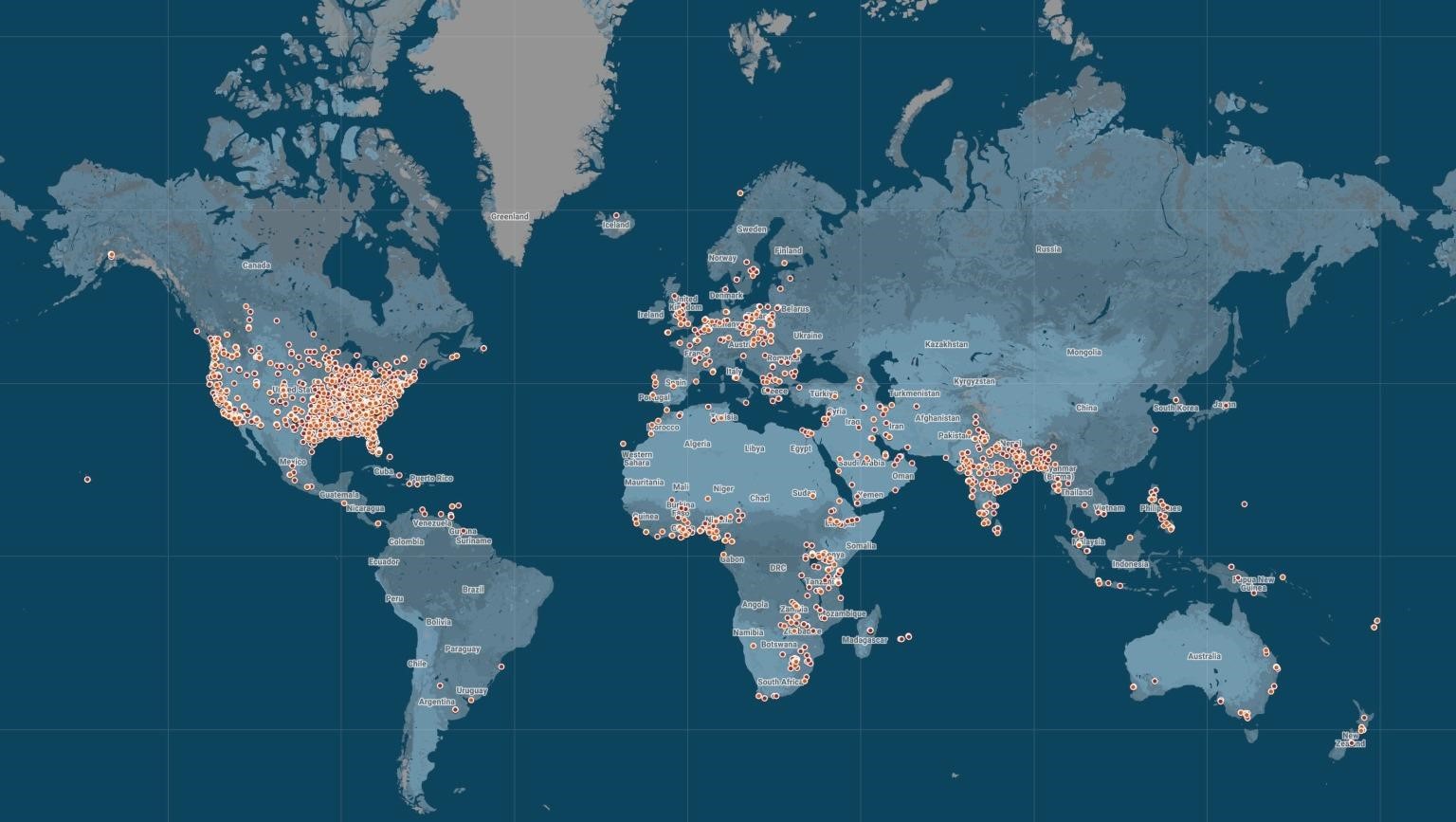
Geolocation of victims on the map
Interestingly, the leak also contains information about 26,000 customers who used the stalker software for free (including their password hashes), and email addresses of people who bought a paid subscription.
A more detailed analysis of this dump can be found on the blog of Swiss hacker maia arson crimew.
Developers and Victims
Usually, developers of spyware and stalker software prefer to hide their identities (after all, in many countries the development and use of such software is considered a crime), and it is very difficult to find information about the creators of such “products”. But in this case, the data leak revealed that LetMeSpy was created and maintained by a Polish programmer named Rafal Lidwin, who lives in Krakow. He refused to answer journalists’ questions.
In an official announcement about the hack, posted on the LetMeSpy website, the company says that it has already notified law enforcement agencies and the Polish Office for the Protection of Personal Data (UODO) about the incident. UODO confirmed to reporters that they had indeed received a notification from LetMeSpy.
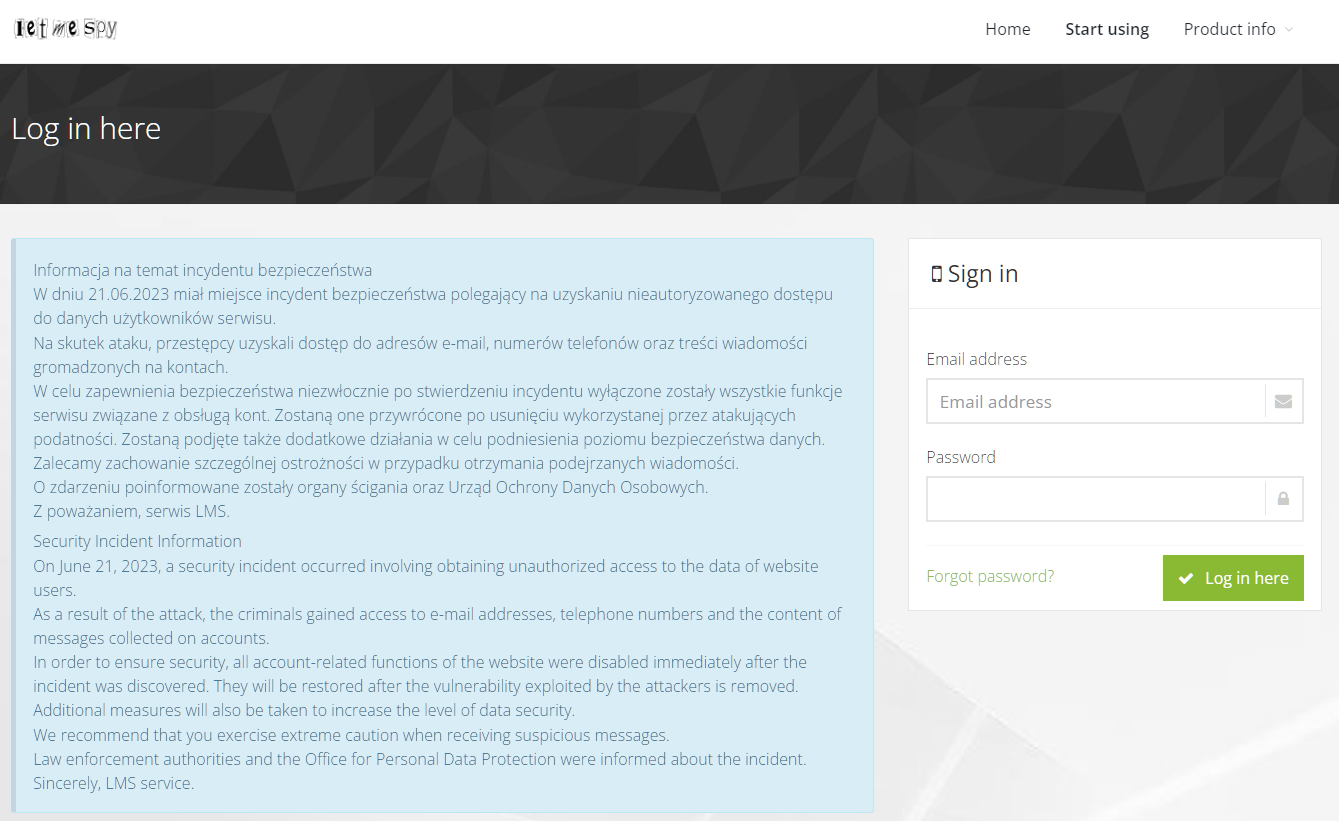
Hacking message on LetMeSpy website
At the same time, it is unclear whether LetMeSpy is going to notify the victims themselves, who were secretly monitored by the company’s clients, about the leak, and whether the company has such an opportunity.
It is noted that the dump that got into the network does not contain information that could be used to directly notify the victims. Even if such information was there, it is difficult to inform victims of spyware about surveillance and data leakage, because in this way it is possible to warn the person who installed the stalker application on the victim’s device, creating an unsafe situation.
It is worth noting that the LetMeSpy data leak is far from the first precedent of its kind. Developers of stalker software are regularly hacked, and the companies behind such spyware forget to secure their servers, credentials and private keys in the code, which makes the data of thousands of surveillance victims available to everyone.
