Modern network-based viruses act as a team – trojan virus, ransomware, and Mimikatz. Ransomware acts as a moneymaker, and the reason for such a role is easy to understand. It is impossible to do business when all data on the computers in your company, including reports, invoices, waybills, and many essential documents, are encrypted. But it was hard to infect all computers in the network simultaneously because most were using passwords. To remove such an obstacle, ransomware developers decided to use hack tools to collect passwords. Mimikatz is one of the most popular hack tools that malware creators use to wipe out the security shield. In this article, you will see the explanation of Windows vulnerabilities, as well as Mimikatz usage together with trojan viruses and ransomware.
About Windows password managing system
You can hear the opinion that Windows does not keep the password in the raw format (i.e., without any encryption, like plain text). Such a delusion is spread evenly through the system administrators and experienced Windows users. And from the one side, they are right – you will likely never see the “raw” password in any logs, in any files. But the HTTP Digest Authentication system, which is used in Windows 10, requires not only the hash of the password, like the original HTTP Digest Authentication but also the exact password.
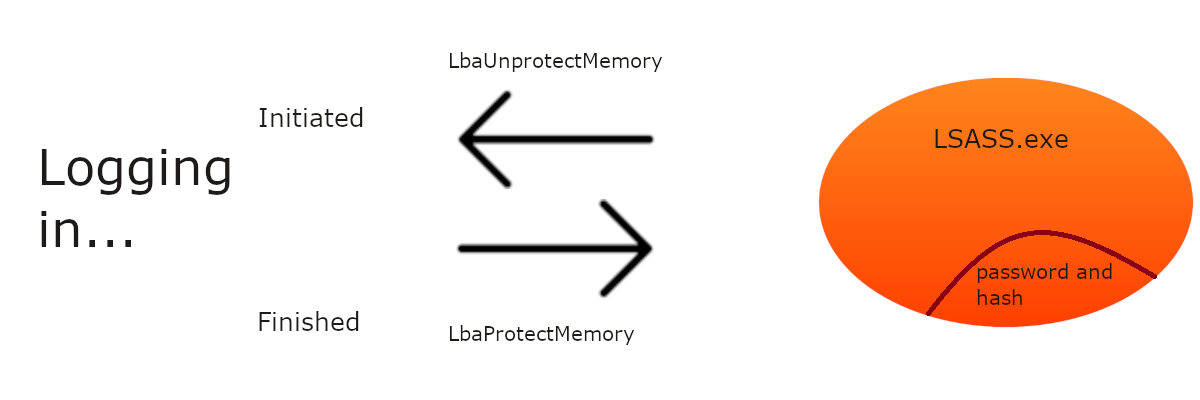
The password and its hash are kept encrypted in the memory of the LSASS.exe process, which launches together with the system and belongs to low-level processes that are responsible for basic system functions execution. At the moment when you are authorizing into your Windows account, the hash and password are extracted from the LSASS.exe memory, then decrypted and compared with the password you inputted. When both hash and password are fitting, the system allows you to log in. When the authentication is done, the mentioned credentials get encrypted back, and left in the memory of the LSASS process until they are needed again.
What is the problem?
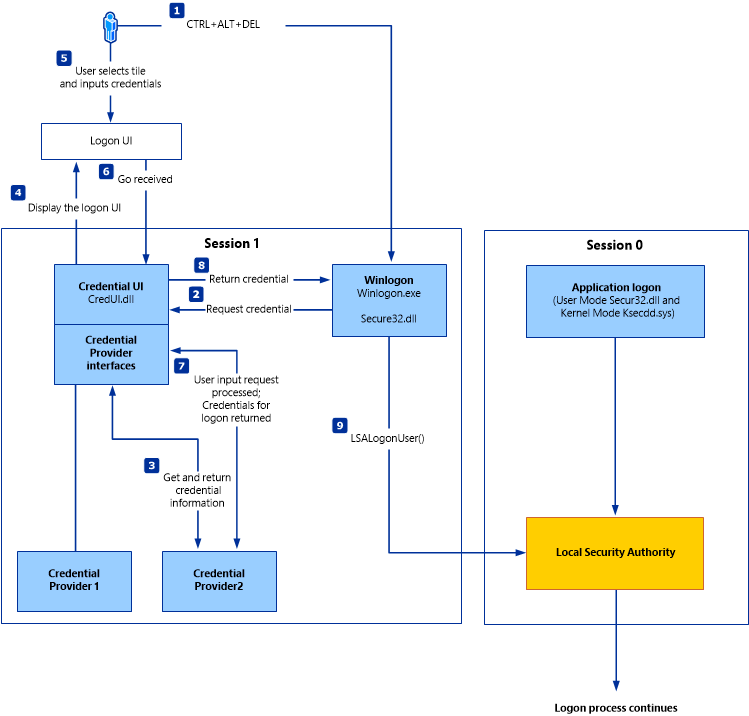
Extracting and decryption process, same as encryption after the authentication process, are realized through Win32 functions LsaUnprotectMemory and LsaProtectMemory1. And since these functions are used in the operating system equally with other functions, they can be used by other programs, for example, hack tools. Using the specific algorithm that Mimikatz uses, these tools can call for LsaUnprotectMemory, getting the “raw” password as well as its hash in the console.
Windows authentication scheme
The problem of such tool usage hides inside of the mechanisms of CPU and OS interaction. After the Windows boot record is initialized, your processor creates virtual memory levels, called “rings”, that are isolated from each other. Instructions set on the processor are on Ring 0, motherboard-related devices drivers are on Ring 1, and operating system basic processes and periphery device drivers are placed on Ring 2. The whole operating system (the part of it which is interacted with by the user) is placed on Ring 3. 2. Programs that are operating on separate rings are not able to interact. Hence, hack tools must be something bigger than simple programs: to operate successfully. They must be launched on the same ring with periphery devices drivers and system processes. And Mimikatz is designed to fit these criteria.
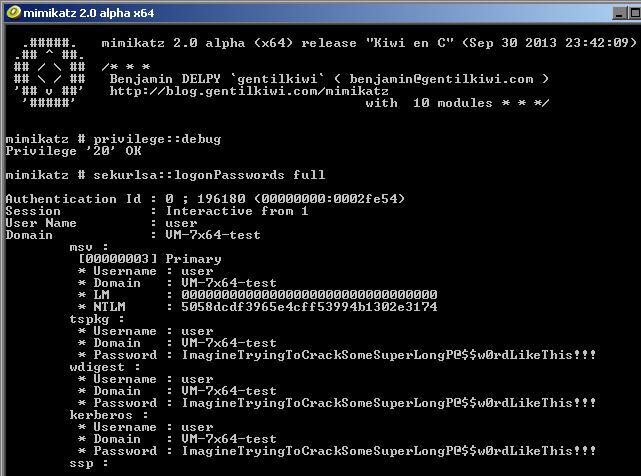
If the virus is implemented so deep in the system, it may take control of the whole computer. Fortunately, Mimikatz is created to dig the passwords from the system, so it cannot break your Windows down. But suppose cyber criminals who developed and distributed the trojan virus have decided to use Mimikatz to hack the passwords. What is the problem for these guys to use another low-level tool to make your system malfunction?
About Mimikatz and ransomware joint action
Infecting the corporate network is not easy. To do it, the initial virus (usually – a trojan), that will inject the ransomware later must have access to all computers in this network. And Mimikatz is called to grant this access to malware distributors.
To perform a successful crack of all computers in the network, Mimikatz must be injected on the computer that has the administrator user account. It can be the system administrator’s PC, as well as the computer of the secretary or one of the workers – whichever. The main criteria are an administrator user account. With such an account, Mimikatz can hack the passwords of all computers that are connected to the attacked network. After the passwords were cracked, trojan, which previously injected the hack tool, injects the ransomware in all computers in that network and then launches the encryption process with a backdoor that was injected together with hacking utility.
All modern global attacks were made in such a way. World-wide attack of WannaCry and its derivatives was done exactly because of the joint activity of Mimikatz and mentioned ransomware. It looked like these attacks were massive enough to make all needed corrections in the network safety of big organizations. But nowadays, in 2020, American hospitals are suffering from ransomware attacks that are executed in the same way. The biggest share of corporation-wide attacks is after DOPPELPAYMER ransomware, which collaborates with Mimikatz and trojan virus to infect the whole network and ask for the huge ransom that depends on the company size. Besides the file encryption, the developers of DOPPLEPAYMER also steal the data of the company they have attacked.
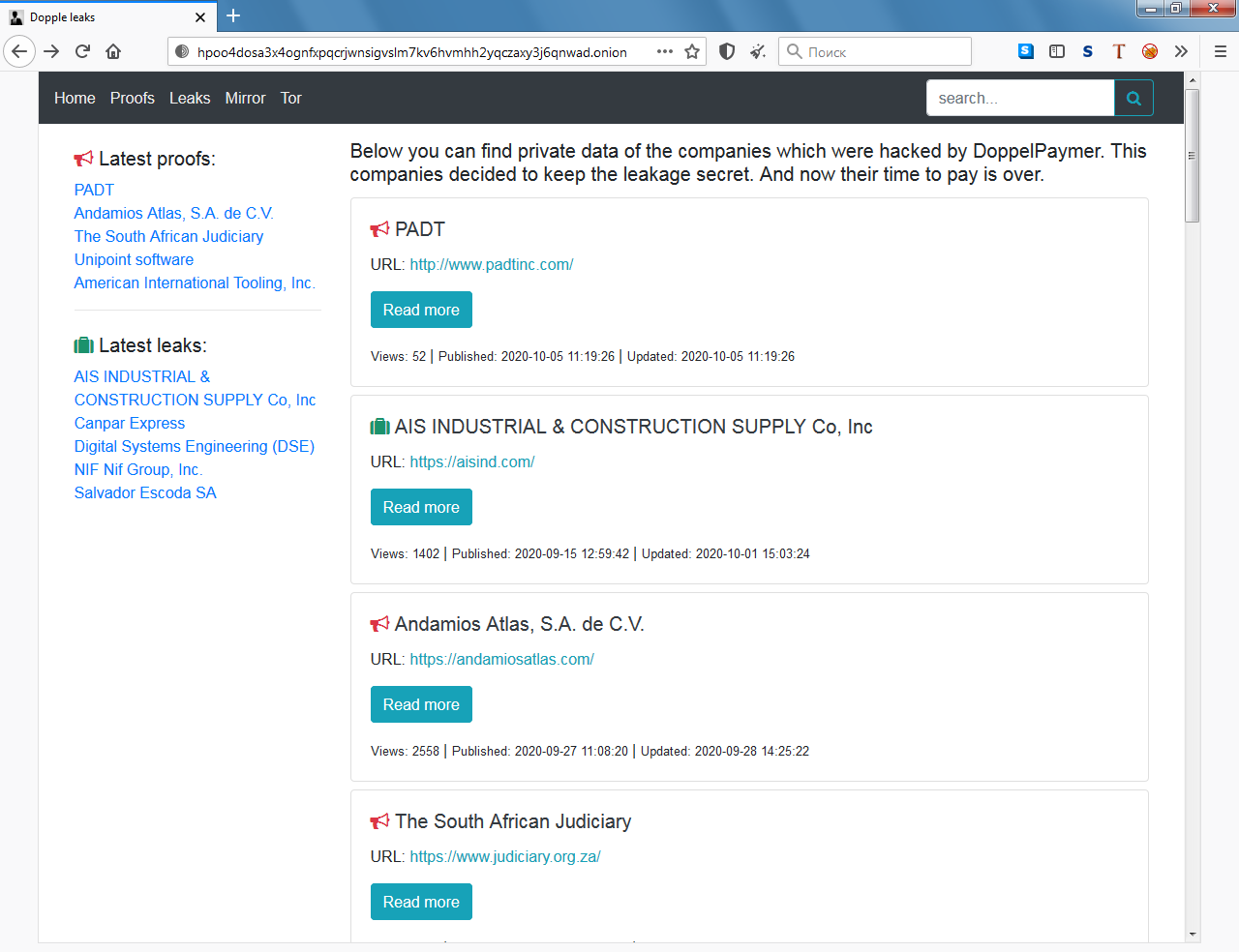
The website hosted by DOPPELPAYMER developers for publishing the stolen credentials and data
How to avoid ransomware attack in your network?
The majority of “dirty work” is done by Mimikatz. So, to cut the chance of a successful ransomware attack, you need to prevent the Mimikatz successful activity. There is a single way to prevent password hacking – remove it from the memory of the described LSASS.exe process. Microsoft offers a perfect solution for this case – Microsoft account as a method of the authorization in the system.
Logging in with the Microsoft account disables the password keeping in the LSASS memory – it will be kept on the Microsoft server. Hash will still be available, but getting the “raw” password is tough, having only a hash. So, using one easy step, which consumes no time and creates no problems, you can protect at least your system from such an assistant of ransomware.
As was already mentioned, all ransomware attacks are provoked by trojan viruses. Trojan injection at can be prevented with the steps which were described in a large number of articles on our website:
- Do not click on the dubious links in the emails. This may lead to downloading trojan, adware, or phishing websites where the credentials of your Facebook/Twitter/LinkedIn account will be stolen.
- Do not open the attachments to the emails, which were sent from dubious email addresses. Even if it looks like a message from the shipping service, it is better to spend five minutes remembering if you have pending deliveries. The best scenario is to check the real emails on the shipping company’s website and compare the addresses you found with ones in the email.
- Avoid using the cracked software or utilities for cracking something. Users who cracked the software can add the trojan virus to the installation package to earn money, the same as the developers of cracking tools.
These simple rules will help you avoid most ransomware attacks.
User Review
( votes)References
- Technical details of LSASS.exe process functions.
- More information about memory isolation on Wikipedia

![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian
