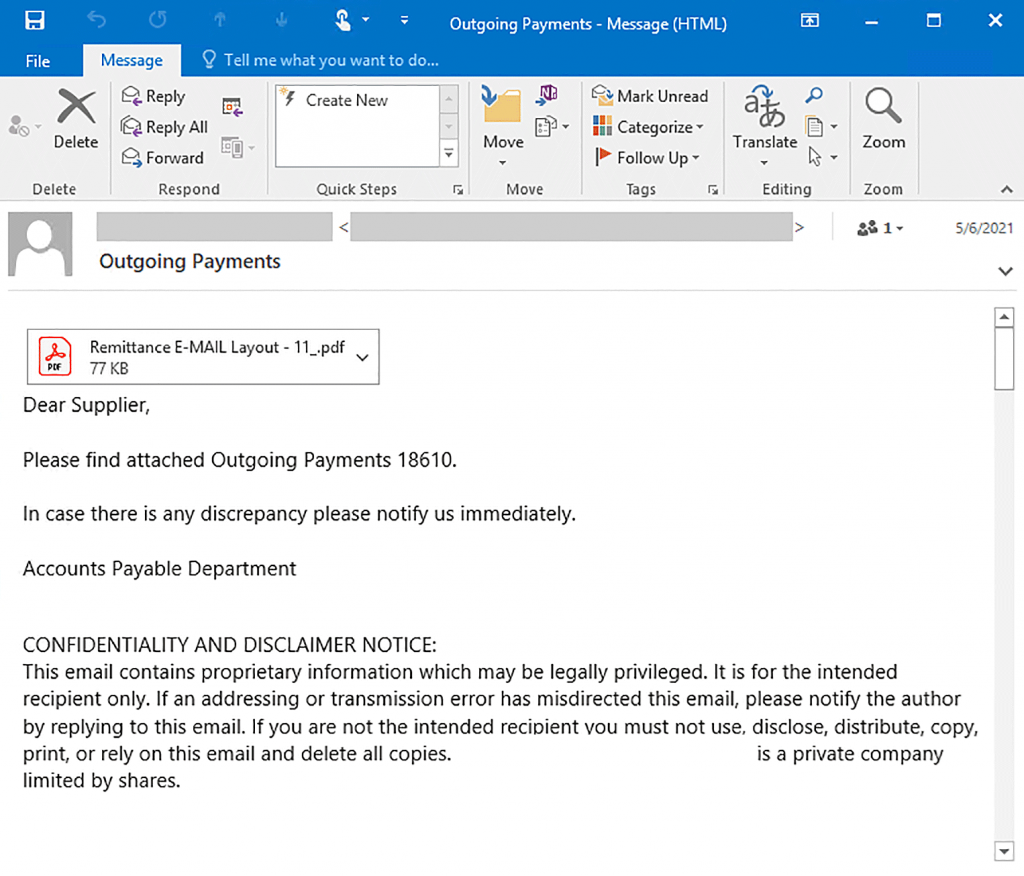
Microsoft has recorded a major campaign to distribute the STRRAT Java Trojan, which provides remote access (RAT) to its operators. This malware is known to steal data from victims, while simultaneously misleading it by simulating a ransomware attack.
A team of Microsoft researchers dedicated a series of tweets to a “massive email campaign” spreading the fake ransomware. To do this, the attackers used compromised electronic mailboxes.
Malicious emails were trying to force the recipient to open an attachment disguised as a PDF document. In fact, in this way, a Trojan was downloaded to the victim’s computer, providing the operator with remote access.
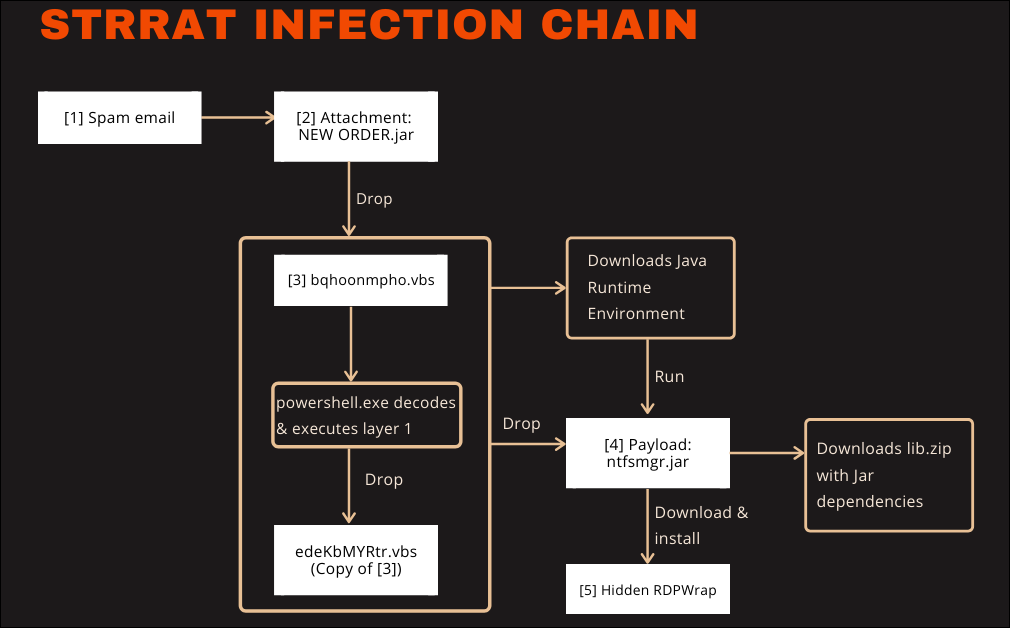
G DATA malware analyst Karsten Hahn said in June 2020 that the malware infects Windows devices via email campaigns pushing malicious JAR (Java ARchive) packages that deliver the finally RAT payload after going through two stages of VBScript scripts.
STRRAT logs keystrokes, allows its operators to run commands remotely, and harvests sensitive information including credentials from email clients and browsers including Firefox, Internet Explorer, Chrome, Foxmail, Outlook, and Thunderbird.
It also provides attackers with remote access to the infected machine by installing the open-source RDP Wrapper Library (RDPWrap), enabling Remote Desktop Host support on compromised Windows systems.
The version number “1.2” and the fact that this malware doesn’t seem to be described before indicates that this RAT is a fairly new player in the wild. The infection chain is not well thought out as it makes void certain features of the intermediate layers in the chain. Also haven’t seen any ransomware reports involving this RAT. Maybe the, for now, badly implemented ransomware module is just the first version of it.
The telemetry shows infection attempts on German customers. It should be noted that the number of potentially vulnerable systems is limited by the current infection chain.
- Even though it is Java based, the RAT only works on Windows
- Even though preparations have been made to overcome this, the current chain still needs a pre-installed JRE
- Outlook blocks the email attachment
Expected that the second and third limitations may be removed soon because they are already prepared or easily implemented. The limitation on Windows however would require too many code modifications.
STRRAT features and command listing
The following table shows a list of all available commands.
| Command | Description |
| reboot | Reboots the infected system |
| shutdown | Shuts down the infected system |
| uninstall | Removes persistence of the RAT by deleting the scheduled task and autorun entries in the registry. |
| disconnect | Closes the connection |
| down-n-exec | Downloads a file from a given URL and executes it |
| update | Disconnects, then executes a given file in the start menu. |
| up-n-exec | Executes a file given by name. Chooses the appropriate runtime environment for files with .jar, .js, .vbs or .wsf extension. Every other file is executed with cmd.exe /c. |
| remote-cmd | Executes commands with cmd.exe |
| power-shell | Executes commands with powershell.exe |
| file-manager | Provides commands to navigate, upload, download, delete and open files |
| keylogger | Logs keystrokes and sends them immediately |
| o-keylogger | Starts offline keylogger which saves logged keystrokes to a text file on the infected system |
| processes | Create a process listing |
| startup-list | Uses WMI to compile a list of autorun entries |
| remote-screen | Remote control the infected computer |
| rev-proxy | Reverse proxy |
| hrdp-new | Downloads and installs HRDPInst.exe[5] which stands for “Hidden RDP Installer”. Download URL hxxp://wshsoft.company/multrdp(.)jpg |
| hrdp-res | Same as hrdp-new, but takes an argument containing a user name. The session for this user is logged off. |
| chrome-pass | Extracts Chrome credentials |
| foxmail-pass | Extracts Foxmail credentials |
| outlook-pass | Extracts Outlook credentials |
| fox-pass | Extracts Firefox credentials |
| tb-pass | Extracts Thunderbird credentials |
| ie-pass | Extracts Internet Explorer credentials |
| all-pass | Extracts all credentials |
| chk-priv | Returns whether it is run as administrator or user |
| req-priv | Run as administrator |
| rw-encrypt | Appends “.crimson” extension to files on the system |
| rw-decrypt | Removes “.crimson” extension from files on the system |
| show-msg | Display a message with notepad.exe |
As you see, STRRAT can record keystrokes, allows attackers to remotely run commands, and extract important information such as credentials from email clients and from browsers Firefox, Internet Explorer, Chrome.