Malware.Heuristic.1004 is a heuristic detection name used by Malwarebytes antivirus software to identify potentially malicious files or programs based on their behavior and characteristics. Antivirus programs utilize heuristic analysis, an active technique, to proactively detect unknown or previously unseen malware by analyzing their behavior and structure.
The detection name “Malware.Heuristic.1004” indicates that the antivirus software has detected a file or program exhibiting suspicious behavior that matches specific heuristic rules or algorithms. However, providing detailed information about the specific malware variant is challenging due to the limited information available about the file and its behavior.
Heuristic detections serve the purpose of identifying potential threats that do not match known signatures or definitions in the antivirus database. While the detection suggests the presence of malware, it does not provide specific details about the type, functionality, or potential impact of the detected file.
Most of the instances, Malware.Heuristic.1004 virus will certainly instruct its sufferers to start funds move for the purpose of reducing the effects of the amendments that the Trojan infection has introduced to the sufferer’s gadget.
Malware.Heuristic.1004
The following adjustments may be implemented:
- The binary likely contains encrypted or compressed data. In this scenario, encryption serves as a means to conceal the virus’ code from antivirus software and virus analysts, preventing easy detection and analysis.
- The malware encrypts the files present on the victim’s hard disk, rendering them inaccessible and unusable by the victim.
- The malware restricts normal access to the victim’s workstation. This behavior is commonly associated with a type of virus known as a locker. It blocks access to the computer system until the victim pays the demanded ransom.
Similar behavior
Related domains
| z.whorecord.xyz | TrojWare.Win32.VirRansom.A@7fqw7c |
| a.tomx.xyz | TrojWare.Win32.VirRansom.A@7fqw7c |
Malware.Heuristic.1004 in Action
The most typical networks through which Malware.Heuristic.1004 Virus are infused are:
- By means of phishing emails;
- As a consequence of customer ending up on a resource that hosts a destructive software;
As quickly as the Trojan is efficiently infused, it will certainly either cipher the information on the victim’s PC or avoid the tool from functioning in a proper way – while also positioning a ransom note that states the requirement for the sufferers to effect the settlement for the purpose of decrypting the files or bring back the file system back to the preliminary condition. In most circumstances, the ransom note will certainly show up when the customer restarts the COMPUTER after the system has already been damaged.
Malware.Heuristic.1004 distribution channels.
In different edges of the globe, Malware.Heuristic.1004 expands by jumps and bounds. Nevertheless, the ransom money notes and tricks of obtaining the ransom quantity might differ depending upon specific local (local) settings. The ransom notes and methods of obtaining the ransom quantity may differ depending on particular regional (local) setups.
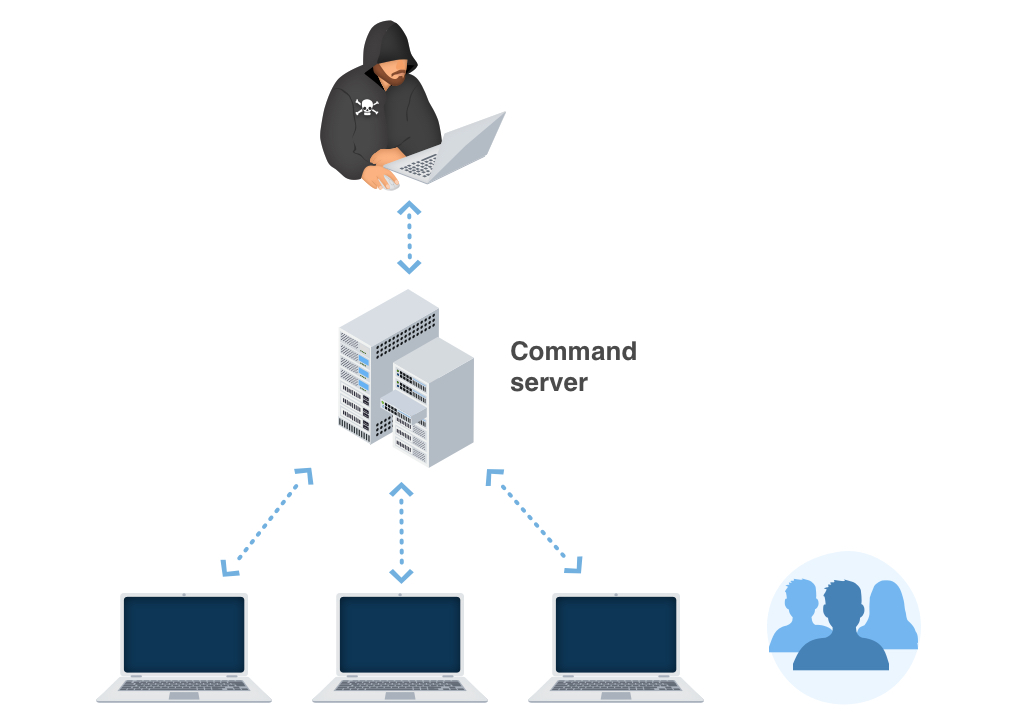
For instance:
Deceptive notifications regarding unlicensed software:
In certain regions, Trojans often deceitfully notify the user that they have detected unauthorized software on their device. The notification then demands a ransom payment from the user.
Misleading statements about illegal content:
In countries with less prevalent software piracy, this tactic may be less effective for cybercriminals. Instead, the Malware.Heuristic.1004 popup alert may falsely claim to originate from a law enforcement agency, alleging the discovery of child pornography or other illicit data on the device.
The popup alert, posing as a law enforcement institution, will also demand a ransom payment from the user.
Technical details
File Info:
crc32: 476E39DBmd5: 28be354bf5a3150cad2e59f6f9c382c4name: 28BE354BF5A3150CAD2E59F6F9C382C4.mlwsha1: bccbf146aac4ea24ee7a12640d48b2fed214918bsha256: dcb9103d3ac4bb13ad28442d791fe0f9b521402aeb1549d95b3e8e5134e45e2esha512: 8ced54bcd905944354a55eeafbaf5f78a2bcd04876162f0332afafcbec1d5044b5b2055783e0ca35d89319de1871247821f397640fe965035634bdb1468aa224ssdeep: 49152:nH+U7nB3+KiD1OUSvoLp+EHP0hRRbG+OZe0hLZMyMWJpiTbLXW+7hJTFegSKP:nLN3M19SvG+GPYG+OQ8ayMEpGLXWUXe8type: PE32 executable (GUI) Intel 80386, for MS WindowsVersion Info:
0: [No Data]
Malware.Heuristic.1004 also known as:
| Bkav | W32.AIDetectVM.malware2 |
| Elastic | malicious (high confidence) |
| DrWeb | Trojan.DownLoad3.63565 |
| MicroWorld-eScan | Gen:Trojan.Heur.GZ.igW@b0VCvxm |
| FireEye | Generic.mg.28be354bf5a3150c |
| Qihoo-360 | Win32/Trojan.03f |
| ALYac | Gen:Trojan.Heur.GZ.igW@b0VCvxm |
| Cylance | Unsafe |
| VIPRE | Trojan.Win32.Generic!BT |
| Sangfor | Malware |
| K7AntiVirus | Trojan ( 00536d121 ) |
| BitDefender | Gen:Trojan.Heur.GZ.igW@b0VCvxm |
| K7GW | Trojan ( 00536d121 ) |
| CrowdStrike | win/malicious_confidence_100% (D) |
| BitDefenderTheta | AI:Packer.51F9BC121E |
| Cyren | W32/Injector.ACA.gen!Eldorado |
| Symantec | ML.Attribute.HighConfidence |
| TrendMicro-HouseCall | Mal_MLWR-1 |
| Avast | Win32:Malware-gen |
| Kaspersky | HEUR:Trojan.Win32.Inject.pef |
| NANO-Antivirus | Virus.Win32.Gen-Crypt.ccnc |
| Rising | Trojan.Injector!1.AF22 (CLASSIC) |
| Ad-Aware | Gen:Trojan.Heur.GZ.igW@b0VCvxm |
| Sophos | ML/PE-A + Mal/Behav-238 |
| Comodo | TrojWare.Win32.VirRansom.A@7fqw7c |
| F-Secure | Trojan.TR/Crypt.XPACK.Gen |
| TrendMicro | Mal_MLWR-1 |
| McAfee-GW-Edition | BehavesLike.Win32.VirRansom.vc |
| Emsisoft | Gen:Trojan.Heur.GZ.igW@b0VCvxm (B) |
| Ikarus | Trojan.Win32.Injector |
| Avira | TR/Crypt.XPACK.Gen |
| MAX | malware (ai score=99) |
| Antiy-AVL | GrayWare/Win32.Injector.dpah |
| Microsoft | Trojan:Win32/Glupteba!ml |
| Arcabit | Trojan.Heur.GZ.E936E5 |
| ZoneAlarm | HEUR:Trojan.Win32.Inject.pef |
| GData | Gen:Trojan.Heur.GZ.igW@b0VCvxm |
| Cynet | Malicious (score: 100) |
| AhnLab-V3 | Unwanted/Win32.HackTool.C2270926 |
| Acronis | suspicious |
| McAfee | Packed-XV!28BE354BF5A3 |
| Malwarebytes | Malware.Heuristic.1004 |
| Panda | Trj/CI.A |
| APEX | Malicious |
| ESET-NOD32 | a variant of Win32/Injector.DPAH |
| Tencent | Win32.Trojan.Generic.Htcw |
| SentinelOne | Static AI – Malicious PE |
| eGambit | Unsafe.AI_Score_97% |
| Fortinet | W32/Injector.DPAH!tr |
| AVG | Win32:Malware-gen |
| Cybereason | malicious.bf5a31 |
| Paloalto | generic.ml |
| MaxSecure | Trojan.Malware.300983.susgen |
How to remove Malware.Heuristic.1004 ransomware?
Unwanted application has ofter come with other viruses and spyware. This threats can steal account credentials, or crypt your documents for ransom.
Reasons why I would recommend GridinSoft1
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes.2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
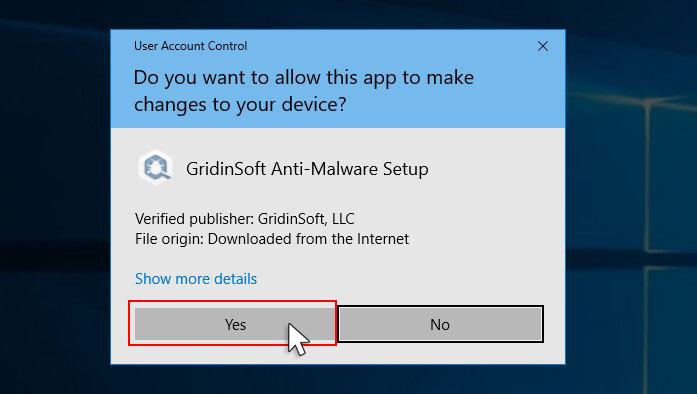
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

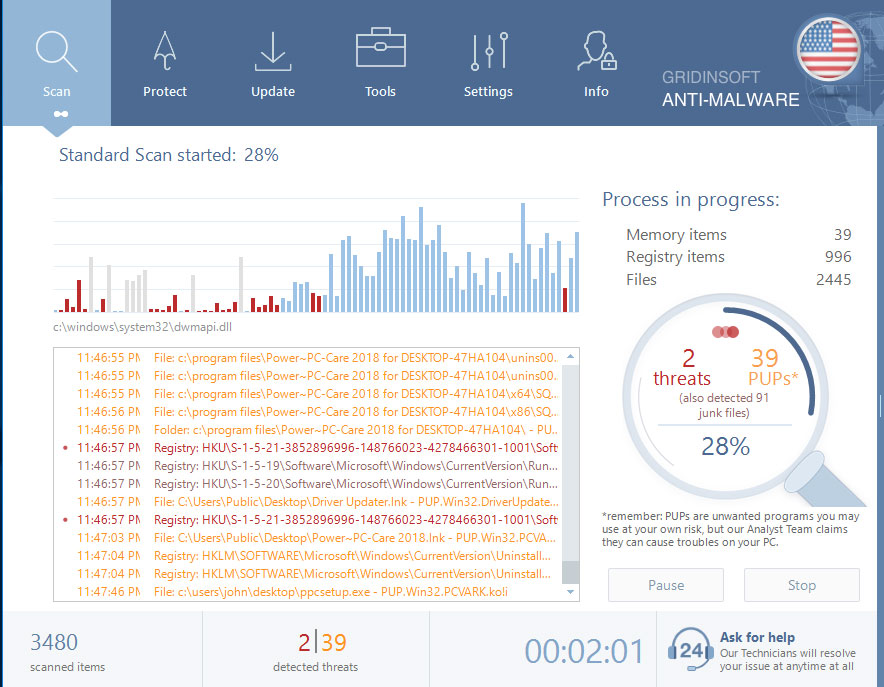
Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Malware.Heuristic.1004 files and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
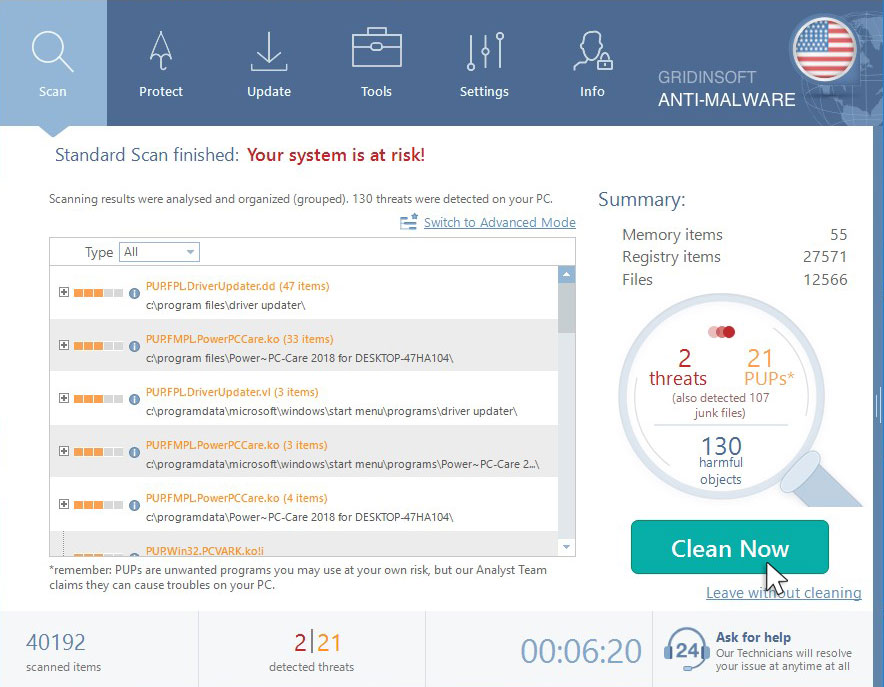
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
Are Your Protected?
GridinSoft Anti-Malware will scan and clean your PC for free in the trial period. The free version offer real-time protection for first 2 days. If you want to be fully protected at all times – I can recommended you to purchase a full version:
If the guide doesn’t help you to remove Malware.Heuristic.1004 you can always ask me in the comments for getting help.
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison