Haron ransomware is another example of malware that encrypts files and then extorts money for their decryption. If you see that your files are encrypted and got the .chaddad extension, be sure – you were attacked by Haron. Besides the essence that is usual for most ransomware families, it has a pretty interesting history of appearance.
What is so special about Haron ransomware?
At the first sight, Haron does not have anything that is significantly different from other ransomware. It uses AES+RSA encryption, which is typical for a lot of ransomware families, aimed at corporations. Another thing that doesn’t show as something unusual is the use of the ransomware-as-a-service model – just like almost all ransomware variants appeared in 2020 and later. But the things are not only about common facts – but they are also about details. Just like in the stories about Sherlock Holmes, isn’t it?
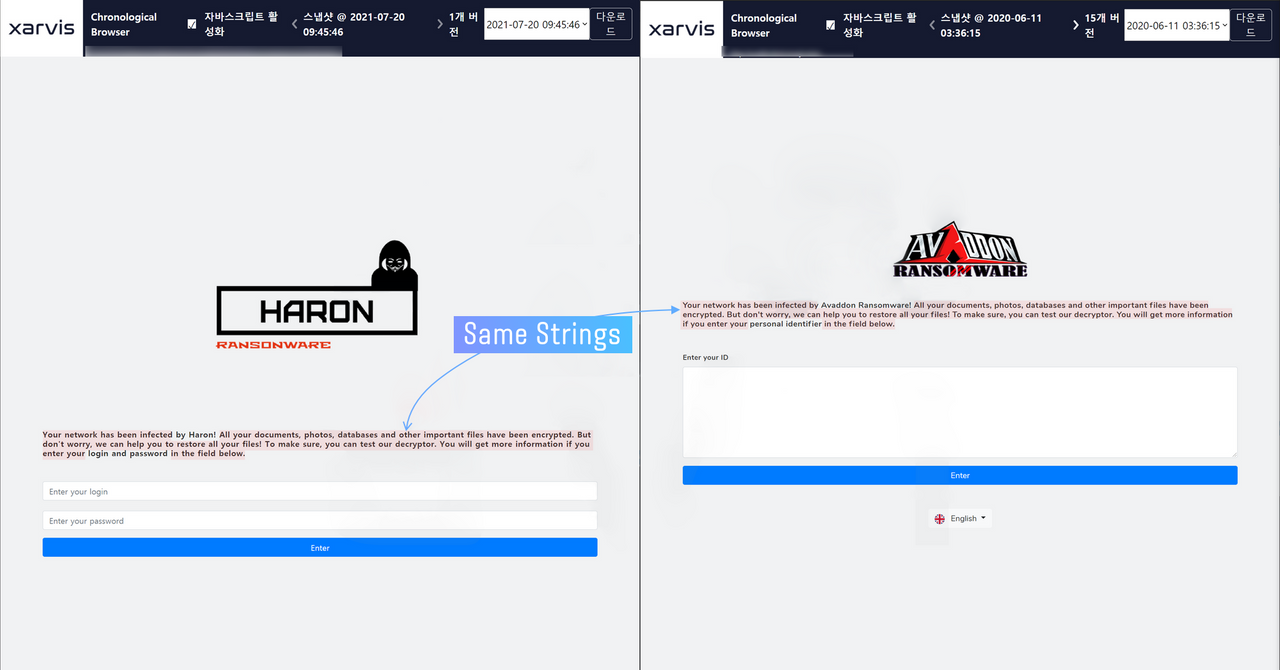
Cybersecurity experts from South Korean firm S2W labs, who have analyzed the “newbie” (Haron ransomware appeared on VirusTotal just on July 19, 2021) noticed that they have seen these specific elements before. The first thing they noticed was the contents of the ransom note. It has a lot in common with Avaddon ransomware notes (see the picture below). Avaddon shut down its activity at the end of May 2021 – almost simultaneously with another ransomware group, called DarkSide.
You may know the DarkSide’s name by its attack on Colonial Pipeline. That cyberattack became known in the whole world because of its huge affect on the fuel supply on the U.S. East Coast. At the peak of this disaster, some states reported about almost 20% of gas stations were shut down due to fuel shortages. This remark is important because a lot of rumors are going around the relationship between Avaddon and DarkSide. Different things point at the fact that Avaddon shutdown exactly after DarkSide’s one is not just a coincidence.
The merger of ransomware groups?
Avaddon and Haron (and, possibly, DarkSide) have not only ransom notes in common. This proof is definitely too weak to say that Haron is the same Avaddon, but with another name. So here is the list of things that points to the fact that Haron is an alter-ego of the Avaddon group:
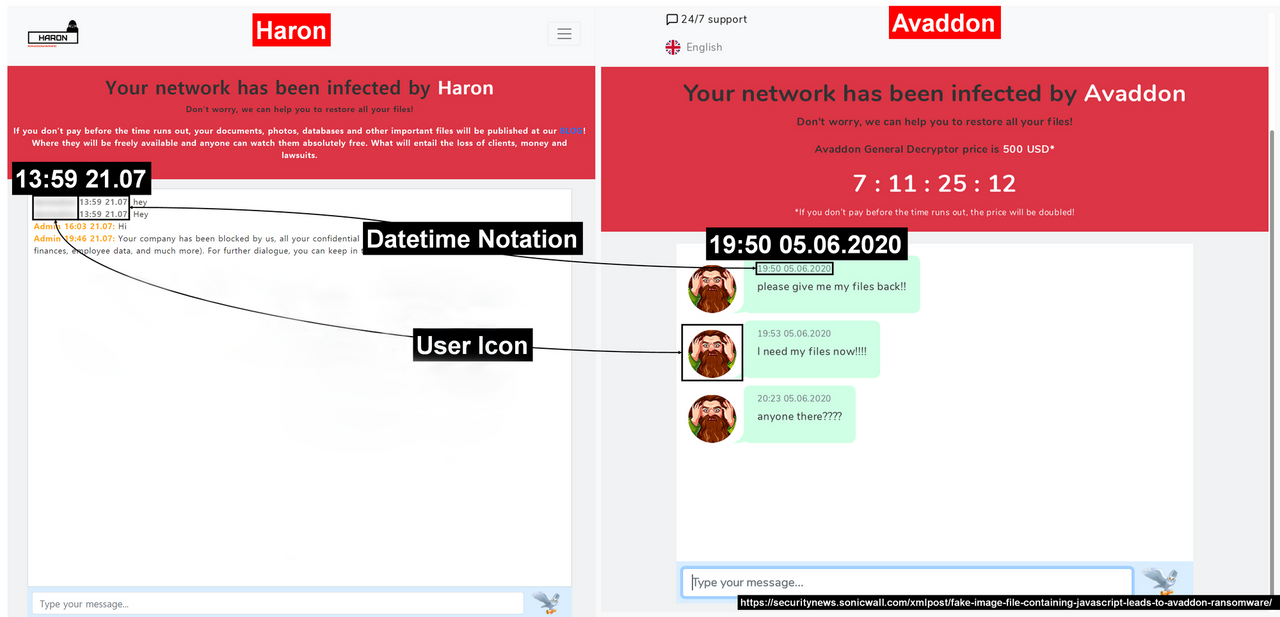
- Similar pages where negotiations take place. Exactly, they are not just similar – they are almost the same. All things that have changed are the logo and the name of the ransomware group in the text. However, in Haron’s case, it is required to log in with a login and password. Avaddon offered to type your ID, which is specified in the money ransom note.
- Going deeper into the negotiation site shows us other similarities. The overall design is almost the same – the scary banner at the top with the countdown timer, as well as the chat window. Date and time notes were simplified a bit, but still show the information in the same order.
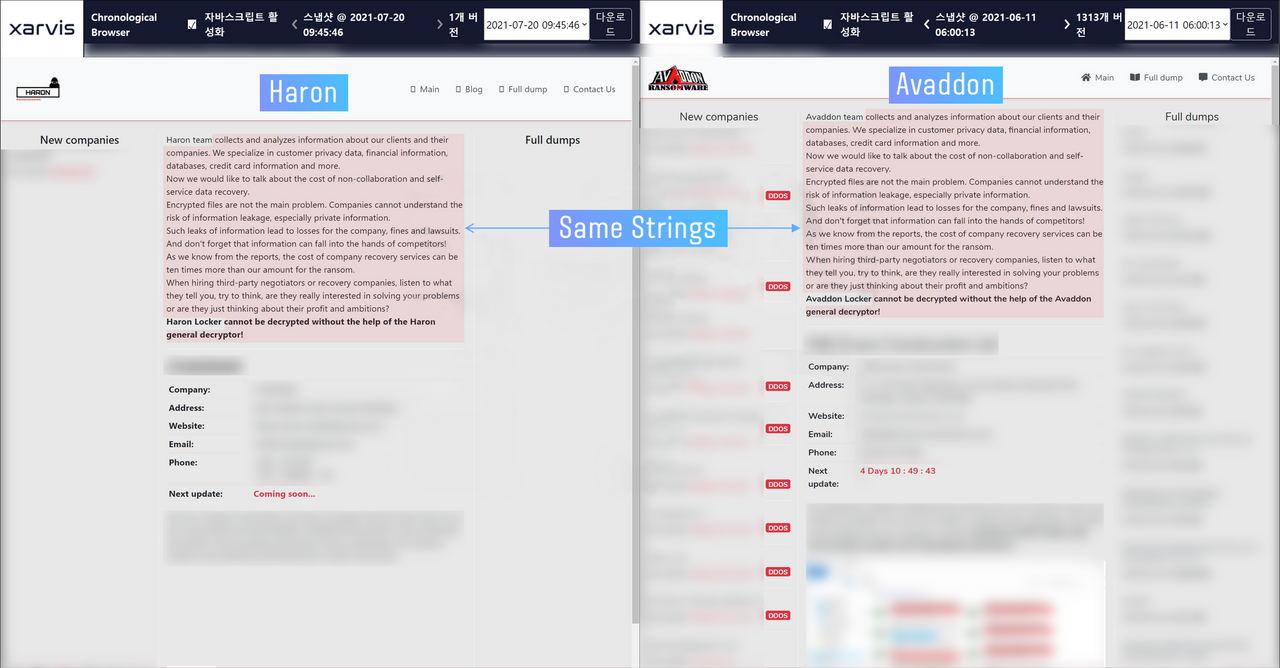
- Websites, where crooks publish the stolen information, are just the same. While all previous elements had a bit of redesign, this thing does not have it at all. The only change is the group name – “Avaddon” to “Haron”.
Phoenix from the ransomware world?
Is it enough to claim that Avaddon and Haron are the same group, but after the renaming? Possibly, those arguments could be used for it, but not after the counter-arguments that were published by the same S2W Lab.
Avaddon had its own ransomware application, developed by the group members in C++. Meanwhile, Haron uses the code of Thanos ransomware that was leaked earlier. Thanos’s source code is based on C#. Their online chat is also not their own development: it is based on the open-source solution, written in JavaScript. Those elements show that even if the aforementioned ransomware groups have something in common, this “something” is pretty small.
Polite ransomware. About Haron target restrictions.
At the moment of launching, one of the distributors of Haron posted the following information on the Darknet forum:
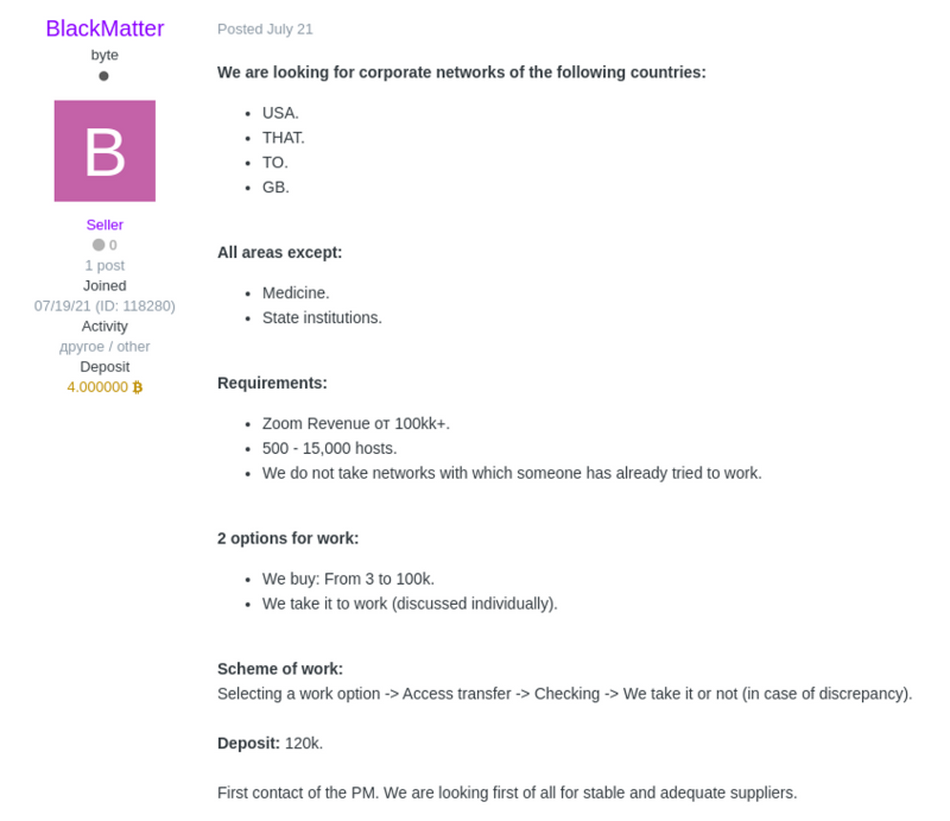
It seems that fraudsters are aimed exclusively at large corporations: even a lot of large public companies cannot beat the “required” range of $100 million of revenue. As the BlackMatter user says (he/she is likely the leader of the distribution group), they will attack only those corporations that are able to pay a big ransom. It seems that crooks are going to extort sums about several million dollars – so the toy shops, small clinics, or local supermarkets are out of range.
The same user also said that “We are ethical blood suckers”. Such a claim was complemented with the list of organization types they will avoid in their attacks. So, due to this claim, they will ignore critical infrastructure (power plants and water treatment facilities), hospitals, defense companies, government and non-profit companies, and oil and gas facilities. Did they get scared after the noise around Colonial Pipeline?
How does Haron ransomware work?
Its similarity with Avaddon ransomware says a lot about Haron, but as you can see from the S2W Lab report, it has a different payload – from Thanos ransomware. In contrast to Thanos, Haron doesn’t have the facilities to cipher the MBR – the loader for the system(s) you have on your computer. Nonetheless, the hazard is still high – AES+RSA encryption is impossible to decrypt. Decryption tools can give you the chance for decryption, but the chance to get the files back shortly after the attack is quite low.
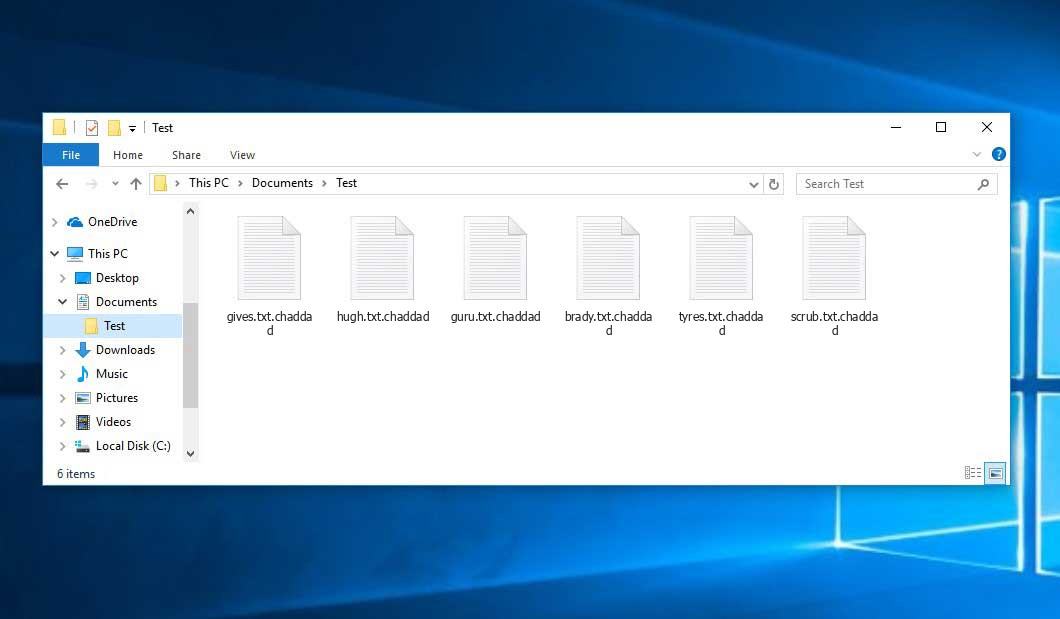
Files encrypted by Haron ransomware (.chaddad files)
Haron ransomware group uses the double extortion technique. This extortion manner means the “basic” ransom for file decryption and the ransom for keeping the stolen data unpublished. Ransomware has several other viruses in its payload, such as spyware or stealer virus. Those malicious items are integrated into the victim’s system and steal the confidential data stored on the machine. If you avoid paying the additional ransom, malware distributors will publish this data for sale on their website in Darknet and spread the information about the cyberattack on your network. Some corporations have strictly confidential information in their reports or invoices, so publishing this information may harm their reputation.
Portion of good news
In contrast to the most modern ransomware groups, Haron does not use triple extortion. That scheme means that besides file encryption and data leakage, fraudsters also get information about the clients of the company. Just as in the case of corporations’ data, they are threatening you that it will be published if the ransom is not paid. But the effect is different – while the image of the corporation may not suffer a lot after the attack, the reputation of some clients may be damaged significantly. And it is pretty easy to get a multi-million dollar lawsuit from these clients, especially if your company provides medical or insurance services.
How is Haron ransomware distributed?
Like the majority of ransomware families that attack corporations, Haron uses the RDP exploiting and email spam. RDP is a widely used technology for remote access to certain machines. Because of the vulnerable ports used in this protocol by default, it is very easy to find the breach for malware injection.
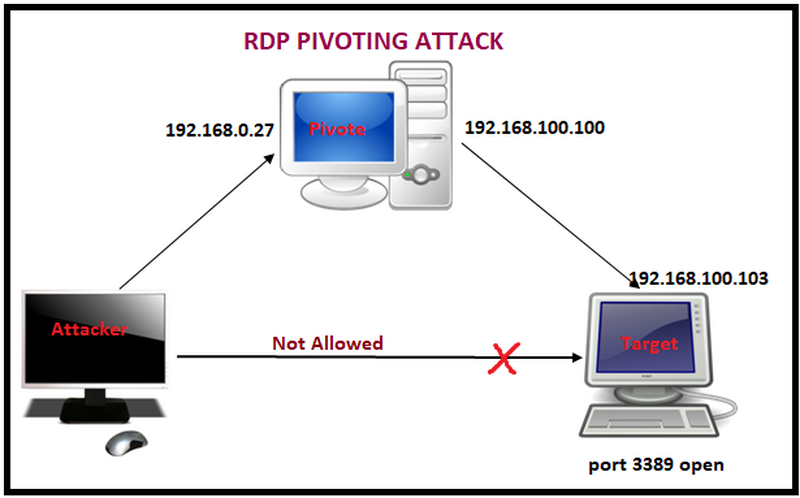
Email spamming is an old-timer of ransomware distribution. Malware hides inside of the file, attached to this message. Usually, the file belongs to a .docx or .xlsx file – because these formats can contain the macros. Macros, exactly, act as a “transmitter” of the malware. Because of its vulnerabilities, ransomware can easily skip the sandbox mode and inject itself into the system.
Examples of phishing emails
Is it possible to avoid the Haron injection?
For sure, you can do it, but only with anticipatory actions. Ensure that only your system administrators set up the RDP connections – they know which ports are safe, and which are not, if not profane. Email spamming, however, is harder to avoid. You must teach the staff that works with emails, how to distinguish fake messages from original ones.
You may identify the fake message by the email address of its sender – like [email protected], for example. Sometimes, fraudulent emails contain a lot of grammar mistakes, as well as other things that are not typical for official letters. Inventive crooks may mimic the email addresses of some famous companies, like Amazon or Microsoft. Addresses like [email protected] may look like something legit, but you can easily refute it by checking at least 1 message from real MS support.
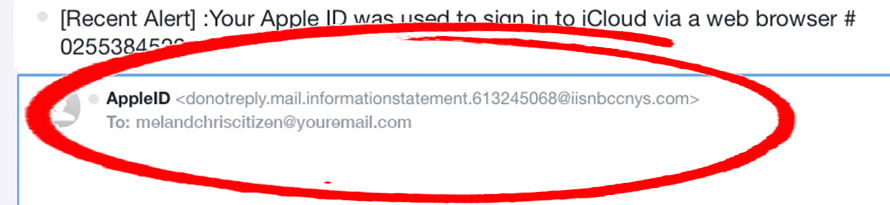
The example of dubious email address
How to Remove HARON Ransomware & Recover PC

Name: HARON Virus
Description: HARON Virus is a ransomware-type infections. This virus encrypts important personal files (video, photos, documents). The encrypted files can be tracked by a specific .chaddad extension. So, you can't use them at all.
Operating System: Windows
Application Category: Virus