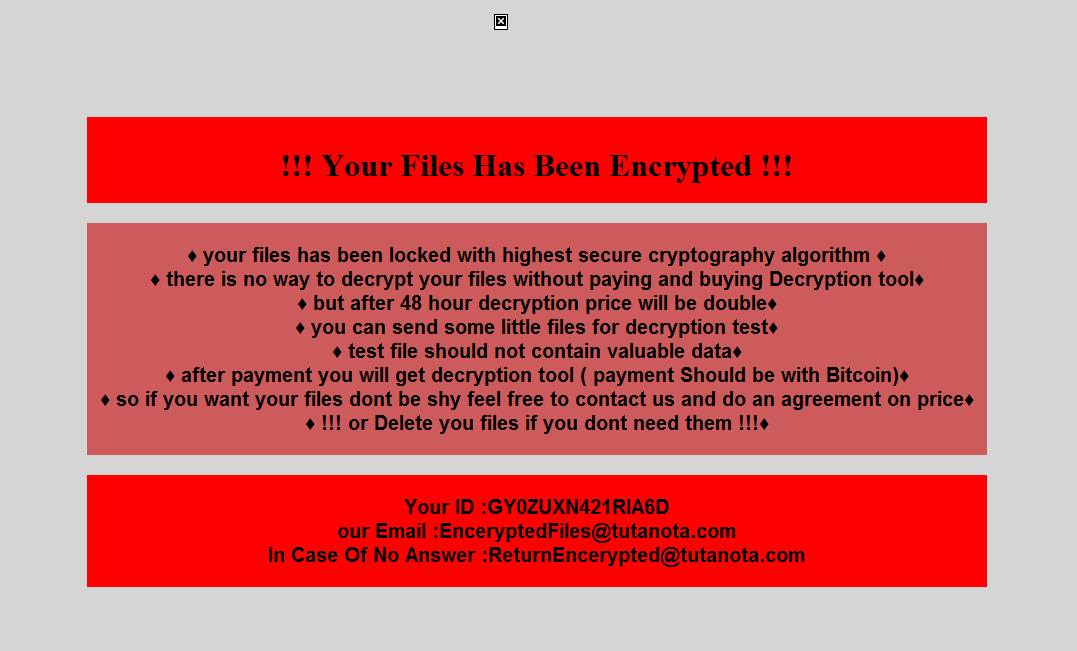
Chaos Ransomware is a newbie in the ransomware world. It was first detected in June, 2021, and was supposed to be an alter-ego of the Ryuk ransomware family. More precise analysis showed that they have much less in common than analysts thought.
Chaos ransomware: the story of evolution
Cybersecurity analysts usually examine the new ransomware group by its activity. However, there are no reported cases of Chaos ransomware attacks. The only thing that says clearly about the creation of this new group is an eponymous ransomware builder, which was published for testing on one of the Darknet forums.
Ransomware builder is, in fact, a special IDE that is designed to create and modify ransomware. It has almost the same functionality as usual IDEs, like IntelliJ IDEA or .NET Framework, but with specific settings that allows the crooks to adjust the final ransomware variant for their needs.
Builder v1.0: how it began
The first edition of Chaos builder appeared on June 9, 2021. This variant contained a Ryuk logo in the upper left corner, which gave birth to the versions that Chaos group is just an alteration of Ryuk. However, a closer look at the outcome of this ransomware builder showed that Chaos does not have a lot of elements in common with Ryuk, and not even ransomware at all.
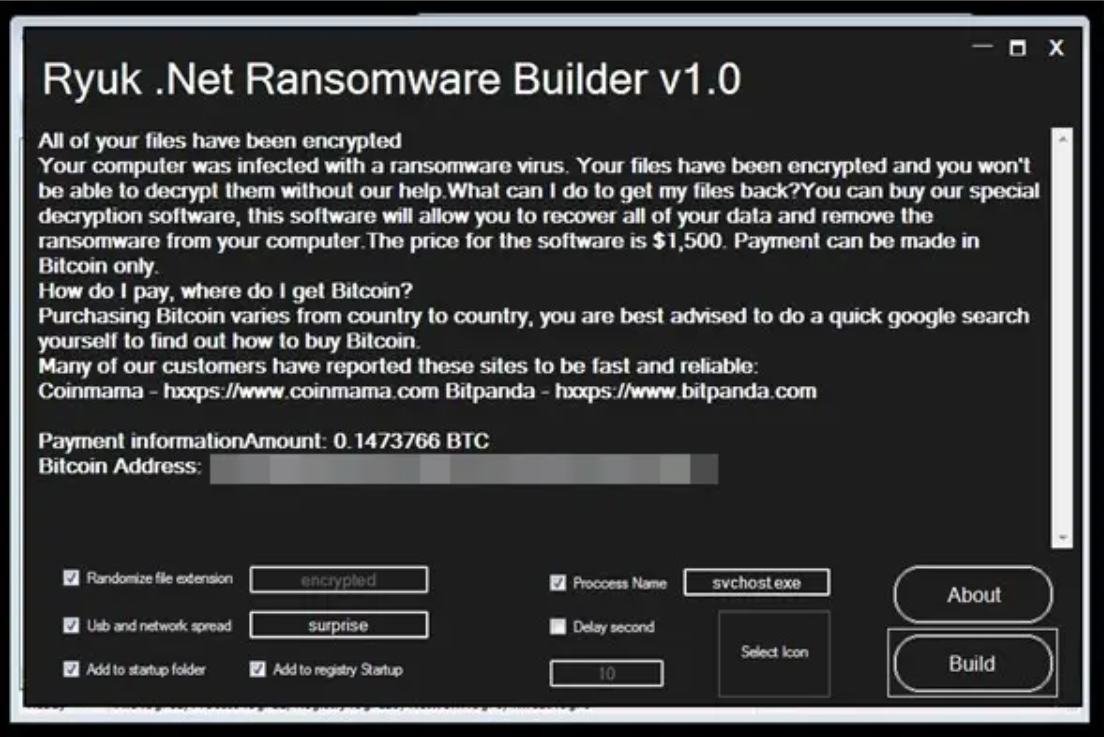
Due to what analysts saw, the first version of Chaos builder is rather a vandal trojan than ransomware. It does not encrypt the files in the system, it just overwrites them with randomly chosen bytes. Hence, paying the ransom will not lead to anything – your data is lost without any chances for decryption or other actions. Only backups could help you, but, again – there are no reported cases of Chaos attacks.
Vandal viruses are a very rare thing, which is almost unused by cybercriminals. They destroy the files kept in the infected system or even destroy the whole file system. In the last case, you have a chance to recover your data. The shelves in the “warehouse” (your disk) are just destroyed, and all items stored in it are now laying on the ground like a pile of rubbish. Nonetheless, if you recover those “shelves” (i.e. file system), you can try to use recovery tools.
Besides having no ransomware functions, the malware which was built by Chaos builder still has the abilities that are pretty typical for most ransomware. It scans the following directories to find the files (in chronological order):
- \\Contacts
- \\Desktop
- \\Documents
- \\Downloads
- \\Favorites
- \\Links
- \\Music
- \\OneDrive
- \\Pictures
- \\Saved games
- \\Searches
- \\Videos
After scanning, this malware attacks the files of more than 100 extensions. Of course, all popular extensions, like .png, .jpg, .jpeg, .txt, .docx and .xlsx are in the scope, too. This feature makes the Chaos from v1.0 builder almost the same effective as ransomware – but without the encryption.
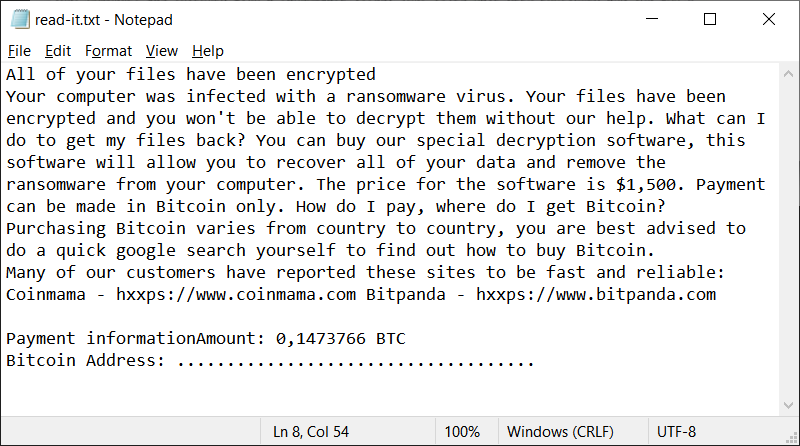
Nonetheless, besides the fact that your files cannot be recovered in any way after the attack, the virus still leaves the ransom note on your desktop. The read_it.txt file looks like this:
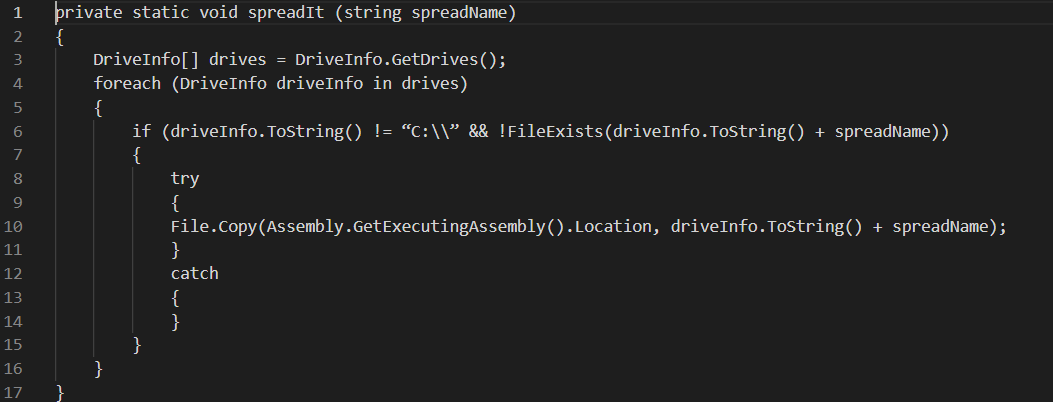
The specific feature that distinguishes this “ransomware” from others is that it can bypass the barrier between logical disks, and encrypt all your drives. No matter if you have a single physical disk divided into several logical ones or each logical disk corresponds to one physical – this virus will just overwrite the files on all of them. Even removable drives are not safe: thanks to the following code strings, it is able to infect even your USB drive:
Chaos builder 2.0: still overwriting
In the second version of Chaos builder, published June 17, 2021, the outcoming malware did not get any encryption functions. However, the new functions arrived: now Chaos ransomware has much more abilities in administrator mode, can disable the Volume Shadow Copies and Windows Recovery Mode. There is also a single visual change: the Ryuk logo has disappeared from the builder window.
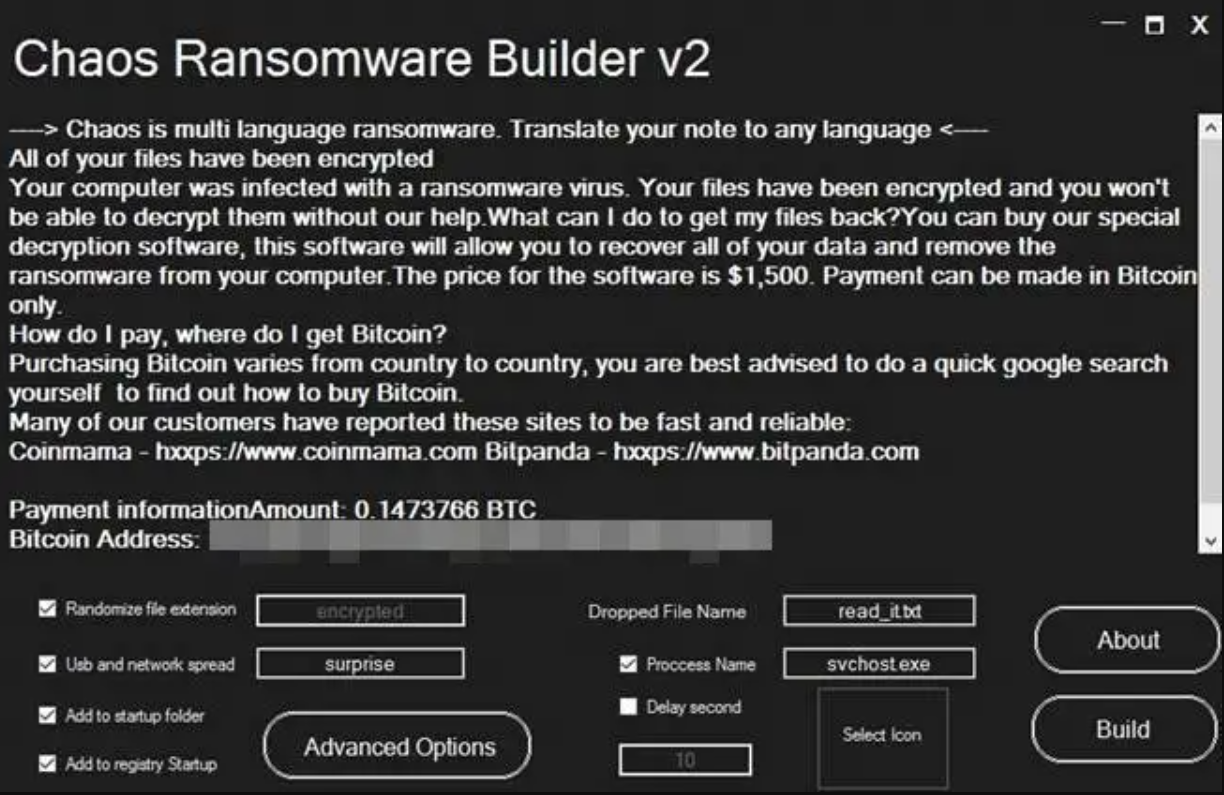
Chaos builder v3: finally, ransomware.
Being a vandal virus definitely creates ill fame around your ransomware. While almost all ransomware groups attempt to create a good image of themselves (pay the ransom = receive your files with a guarantee), Chaos has shown its sneaky nature even before the attacks. Hence, turning into “classic” ransomware was just a question of time. Money is always more important than revenge or reasonless vandalism.
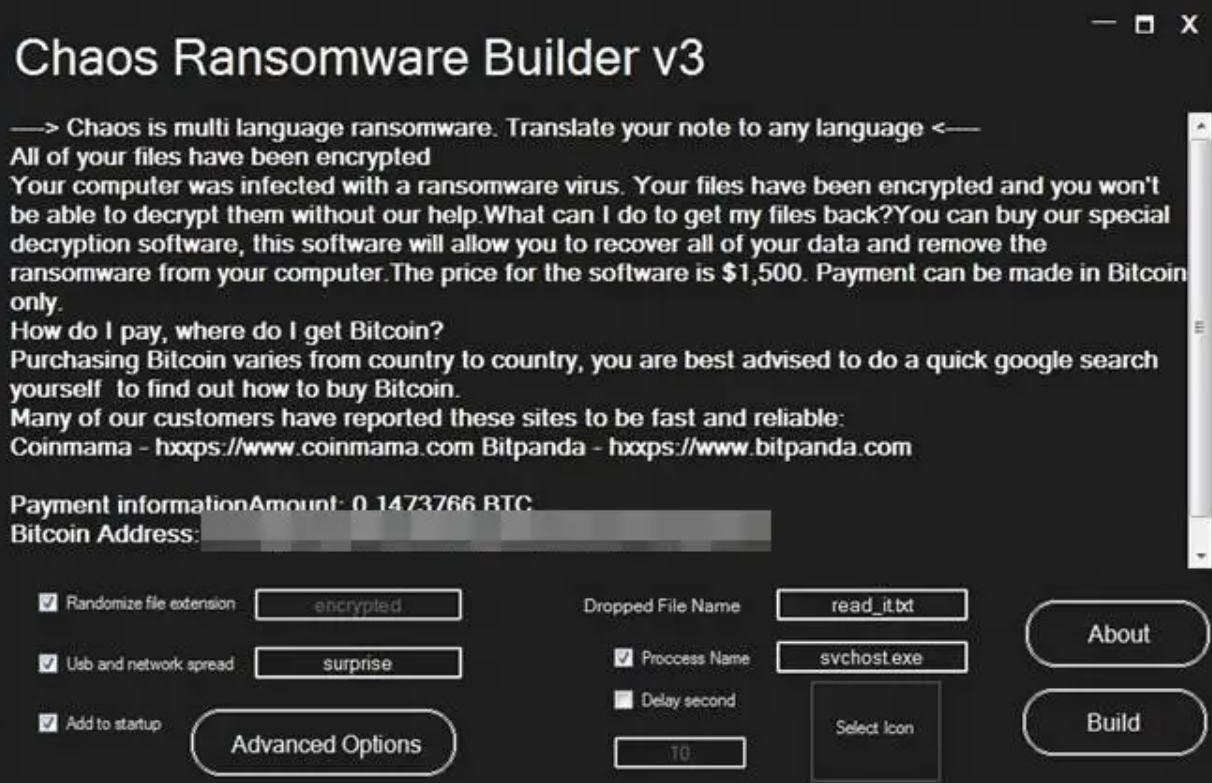
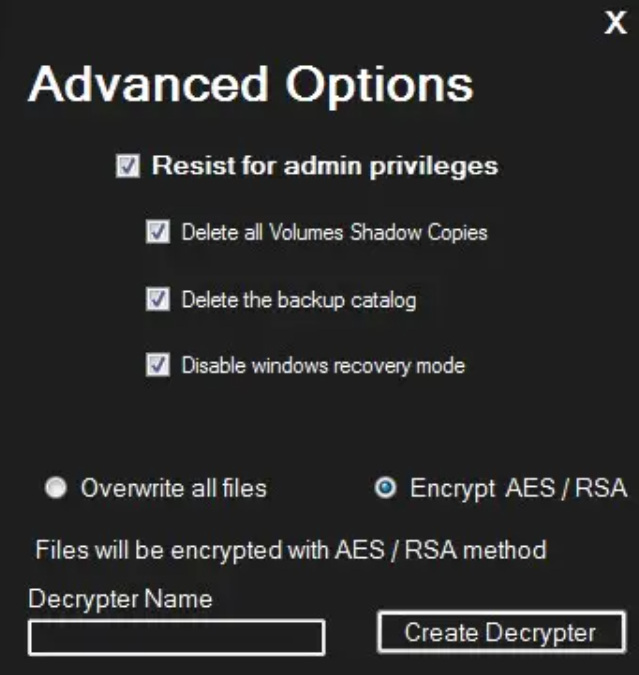
The result of the builder v3.0 activity (published June 5, 2021) is encrypting files smaller than 1MB using the AES+RSA mixed encryption. Besides that, the v3 builder also allows you to create the decryption tool for the ransomware. There is also the possibility to enable the overwrite mode – back to a more early version of Chaos ransomware.
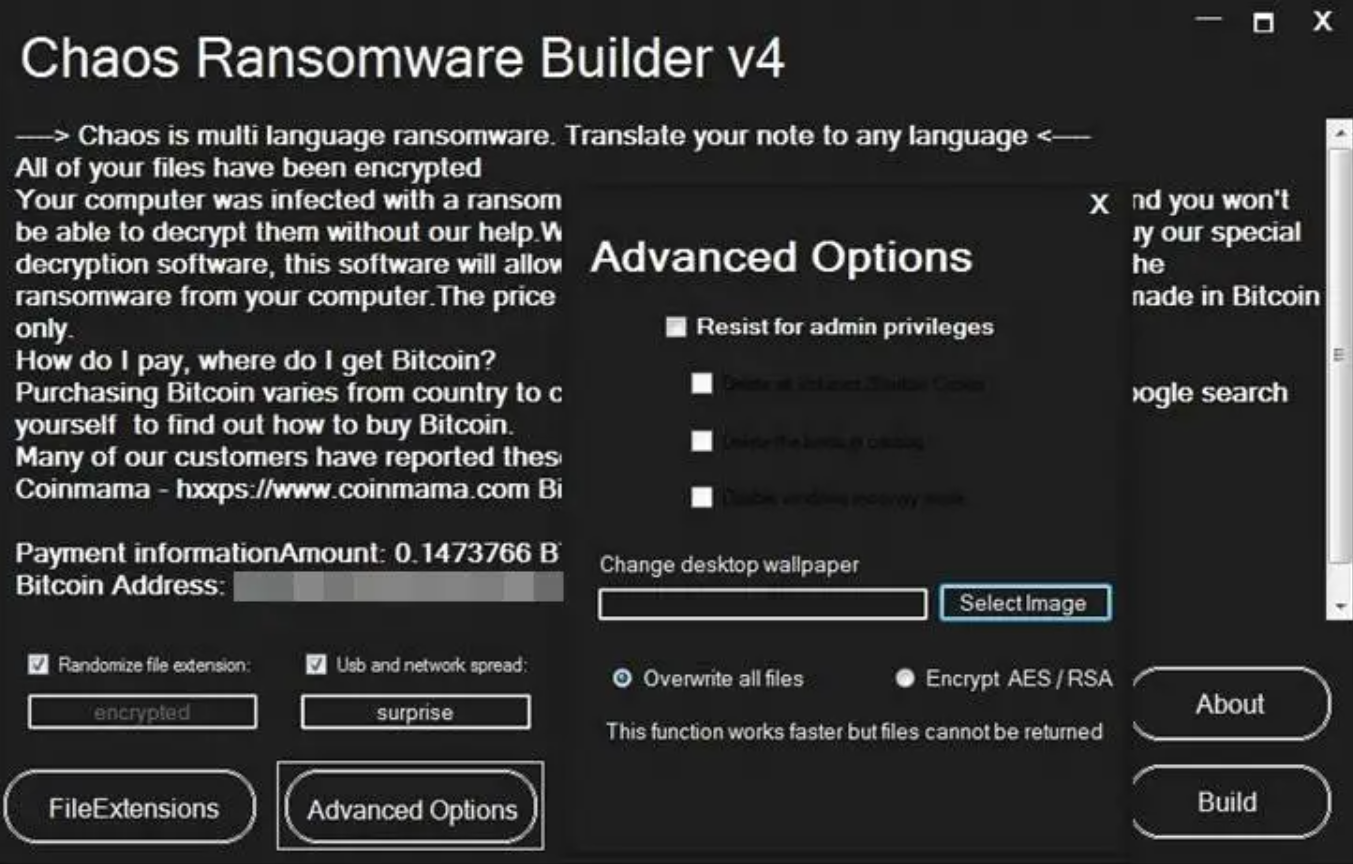
Builder v4.0
On August 5, 2021, the fourth version of Chaos builder appeared on public. This version did not bring something brand new to the outcoming ransomware but buffed the add-on functions. Now, the ransomware is able to change the wallpapers – that is often needed to display the ransom note constantly and keep the victim in fear. Other things that have been changed are the ability to add its own extension and the size of files that could be encrypted: the limit was increased to 2MB. That allows this virus to attack some small Photoshop projects, small or low-quality audio files, any .png and almost all .jpg files.
After all these alterations, which can surely be described as evolution, Chaos malware can surely be called ransomware. However, it has its features, which are not so unique – but never used in such a combination. Some facts were not spoken clearly, but it is obvious that such new ransomware will use the RaaS scheme, aim at corporations and apply the double extortion.
Here are the SHA256 hashes of the viruses from each builder versions:
| Chaos v1 | 0d8b4a07e91e02335f600332644e8f0e504f75ab19899a58b2c85ecb0887c738 |
| Chaos v2 | 325dfac6172cd279715ca8deb280eefe3544090f1583a2ddb5d43fc7fe3029ed |
| Chaos v3 | 63e28fc93b5843002279fc2ad6fabd9a2bc7f5d2f0b59910bcc447a21673e6c7 |
| Chaos v4 | f2665f89ba53abd3deb81988c0d5194992214053e77fc89b98b64a31a7504d77 |
User Review
( votes)