Trojan Emotet
Emotet is extremely innovative as well as a damaging financial Trojan used to download and install and also install other malware. Very first recorded in 2014, Emotet has obtained sophisticated abilities throughout its lifetime. Today Emotet is targeting governments, firms, small companies, and also individuals, focusing on Europe, America, and also Canada.
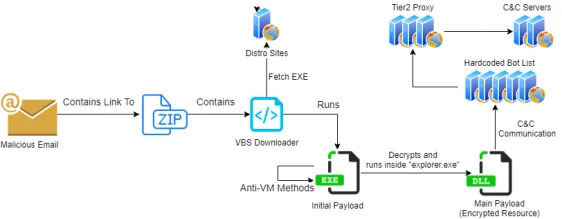
After 2 quiet weeks, Trojan Emotet has ramped up its servers, downloading TrickBot and Qbot payloads.1 Cybercriminals behind the botnet upgraded the downloader stage by adding clean Microsoft files to packages, possibly to thwart detection by machine learning solutions.
A large Emotet spamming campaign is underway, bombarding customers in Lithuania, Greece, Japan, Romania, and France. The emails typically consist of stolen legitimate communication and generic short lure by the operators such as:
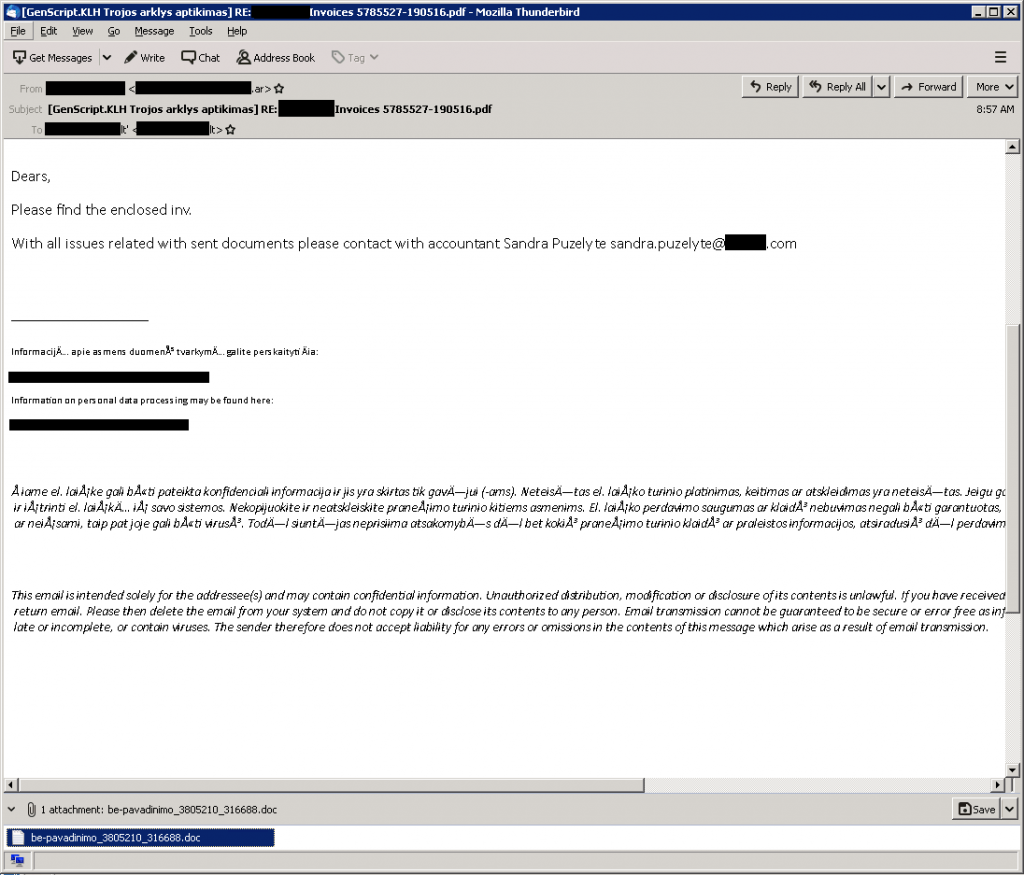
Attached to the spam messages is a document, detected as GenScript.KLH, with a malicious VBA script, detected as VBA/TrojanDownloader.Agent, that downloads Emotet trojans. Despite Emotet’s latest push, TrickBot remains well below its previous rates after disruption effort in the past weeks.
User Review
( votes)References
- Source: https://twitter.com/ESETresearch
