According to Checkmarx analysts, two unnamed banks have been the victims of attacks on the open-source supply chain in recent months.
Researchers say these are the first incidents of their kind. Although the FBI even issued a warning about an increase in the number of attacks on supply chains, but by other methods.
In February and April of this year, attackers uploaded packages with malicious scripts to npm.
So, during one of the attacks, hackers placed several infected packages with pre-installed scripts that checked the victim’s operating system. Depending on whether it was Windows, Linux, or macOS, the script decoded the other encrypted files in the package.
These files were then used to download the malware to the target computer, and the hackers moved on to using the Havoc post-exploitation framework, which is able to bypass standard protections such as Windows Defender.
The attackers who uploaded these packages to npm created a fake page on LinkedIn, where they pretended to be an employee of the victim’s bank. Because of this feature, Checkmarx researchers initially decided that perhaps this was not an attack, and the bank’s specialists themselves were conducting a pentest.
However, after contacting a financial institution, the researchers were convinced that they had not even heard of such software.
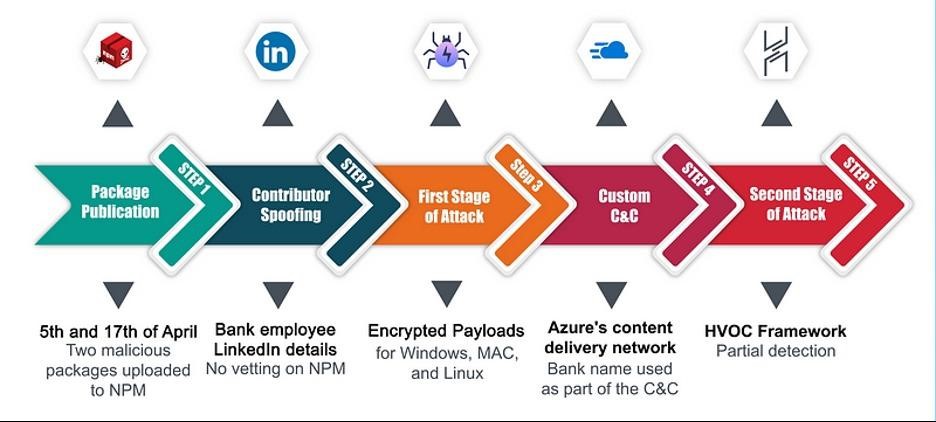
Scheme of the first attack
In another incident, hackers targeted a bank’s login page by creating an npm package into which they injected malicious code that “was dormant until prompted to act.” The code was focused on the mobile bank login page.
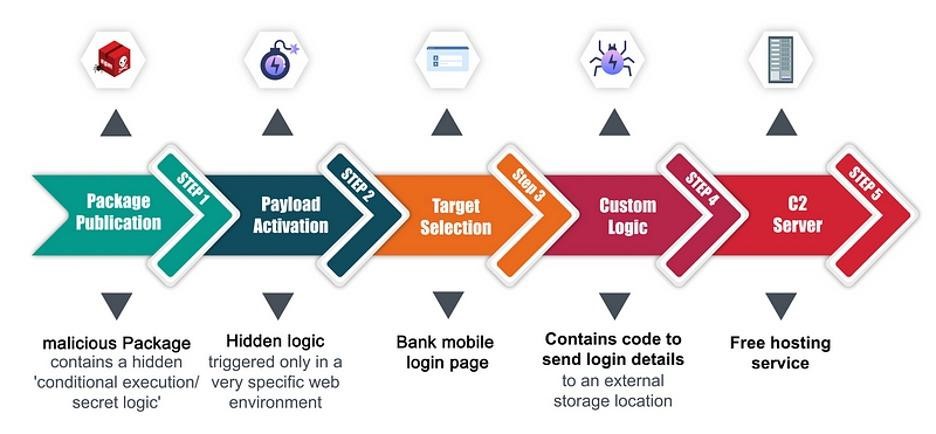
Scheme of the second attack
The malicious packages were removed shortly after they were discovered, but Checkmarx analysts believe that in the future we will see “a steady trend of attacks on the open-source supply chain in the banking sector.”
