Wiz analysts are confident that the recent theft of Microsoft’s MSA (Microsoft account consumer signing key) cryptographic key from Microsoft could have much more serious consequences than the hacking of Exchange Online and Outlook accounts, which were compromised by the Chinese group Storm-0558. According to experts, the leak affects all Azure AD applications running with Microsoft OpenID v2.0.
Let me remind you that more than two dozen organizations around the world, including government agencies in the United States and Western Europe, became aware of the theft of the MSA key and the attack on Exchange Online and Azure Active Directory (AD) in mid-July 2023.
Then it was reported that in mid-May, attackers managed to gain access to Outlook accounts belonging to about 25 organizations, as well as to some user accounts that were likely associated with these organizations. The names of the affected organizations and government agencies were not disclosed. It is known that among the victims are the US State Department and the country’s Department of Commerce.
As explained by Microsoft, for this attack, the attackers used authentication tokens forged with an MSA (Microsoft account consumer signing key) cryptographic key, which is used to sign the tokens.
Thanks to a 0-day validation issue in GetAccessTokenForResourceAPI, hackers were able to forge someone else’s signed Azure Active Directory (Azure AD or AAD) tokens and impersonate their victims.
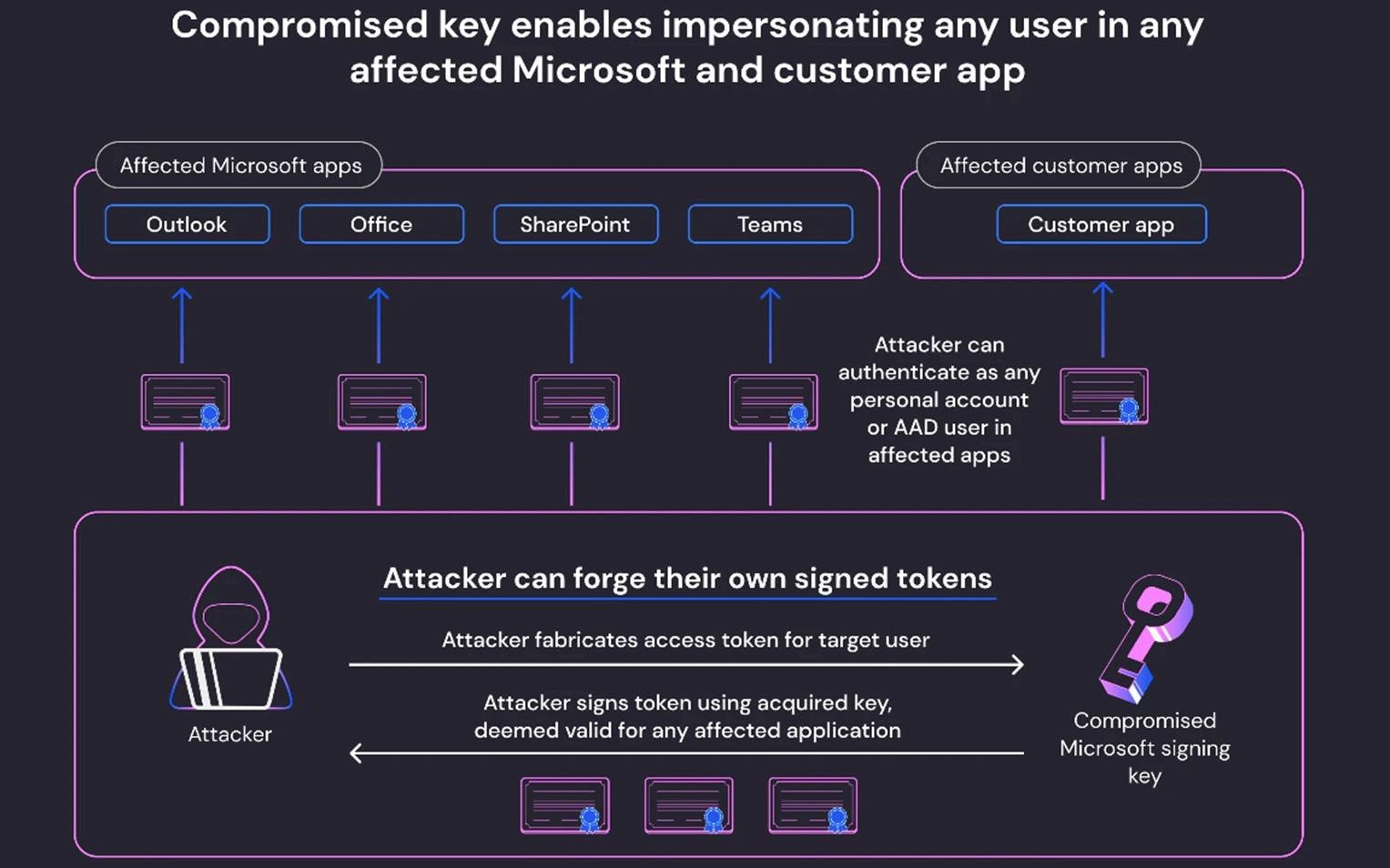
At the same time, Microsoft still has not explained how exactly such an important MSA key ended up in the hands of hackers.
Cloud security firm Wiz now says the issue has affected all Azure AD applications running Microsoft OpenID v2.0. The fact is that the stolen key could sign any OpenID v2.0 access token for personal accounts (for example, Xbox, Skype) and AAD multi-tenant applications under certain conditions.
By the way, we also talked about two sensational 0-day vulnerabilities in Exchange and about not always successful attempts by Microsoft to fix them. In addition, information security specialists reported that these and other problems in Exchange were exploited by attackers from the Lockbit group.
While Microsoft said only Exchange Online and Outlook were affected, Wiz believes the hackers could have used the compromised key to impersonate any account in any affected Microsoft client or cloud application. These include managed Microsoft applications such as Outlook, SharePoint, OneDrive, and Teams, as well as client applications that support Microsoft Account authentication, including those that enable the Login with Microsoft functionality.
In response to these allegations by researchers, Microsoft representatives reiterated that the company has revoked all MSA keys to ensure attackers do not have access to other compromised keys. And it completely prevents any attempts to create new tokens. The company also says that many Wiz experts’ statements “are speculative and not based on facts.”
After the stolen key was revoked, Microsoft reportedly found no additional evidence pointing to unauthorized access to customer accounts using the same token forgery method. In addition, Microsoft notes that Storm-0558’s tactics have changed, and hackers no longer have access to any signing keys.
The fact is that before this incident, logging capabilities were available only to Microsoft customers who paid for the appropriate Purview Audit (Premium) license. Because of this, Microsoft faced serious criticism from the information security community, and experts said that Microsoft itself prevented organizations from quickly detecting Storm-0558 attacks.
As a result, under pressure from the community and the US Cybersecurity and Infrastructure Protection Agency (CISA), the company agreed to expand access to cloud log data for free so that defenders can detect similar hacking attempts in the future.
