Cofense experts discovered a new phishing operation in which attackers infect Windows-based computers with Quasar Remote Administration Tool (RAT) using fake resumes.
While fake resumes and other types of documents are a fairly common method for delivering malware, one of the features of the new campaign is usage of several methods that complicate the analysis of infection vectors.“Organizations find a higher degree of difficulty with the ‘.doc’ file attachment distributing Quasar RAT itself, because the document employs a multitude of measures to deter detection”, — report Cofense specialists.
Quasar is a well-known open source tool developed in C#, which has been repeatedly seen in the operations of various hacker groups, for example, APT33, APT10, Dropping Elephant, Stone Panda or The Gorgon Group.
Read also: Cybercriminals used Google Drive for targeted phishing
The program’s functionality includes the ability remotely connect to the desktop, record keystrokes and steal victims’ passwords, download and filter files, manage processes on an infected device, as well as take screenshots and record from web-cameras.
As part of a new phishing campaign, attackers, under a mask of a resume, distribute password-protected Microsoft Word documents. After entering the password “123” indicated in the phishing message, the document requests activation of the macro.
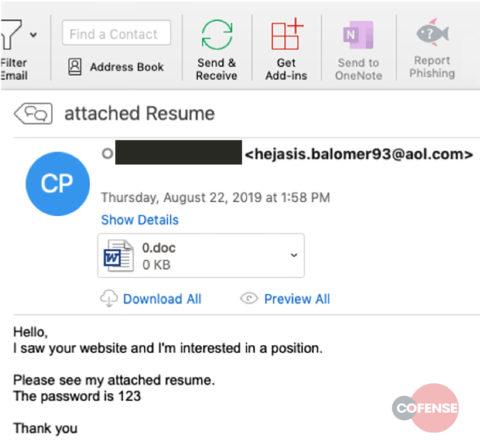
Original Email
A password of “123” is not particularly inventive, but to an automated system that processes attachments separately from emails it means that the document will be opened and no malicious activity will be recorded because the system has not determined either a need for a password or what the password is.
However, unlike other similar attacks in this case, the macro contains “junk” code encoded in base64, designed to disable the analytical tools installed on the computer.
“When the macro runs successfully, a series of images will appear on the screen, supposedly loading the content, but at the same time adding a “garbage” line to the contents of the document. Then an error message will be displayed, but at the same time, a malicious executable file will be downloaded and launched on the computer in the background”, — the experts explain.
Quasar infects the program through a 401 MB self-extracting executable file downloaded from a server controlled by cybercriminals. The large archive size complicates the task of malware analysis.
How to counteract an attack?
Along with automated tools, educating employees on new phishing trends is the best way of countering a campaign such as this.
